A sensitive mail filtering system and method based on client/server mode
A server mode, client technology, applied in the field of sensitive mail filtering system, can solve the problems of sensitive data leakage, users do not have control over the server, data theft, etc., to achieve the effect of preventing mail transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
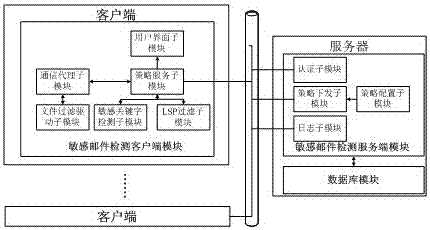
[0050] The first step of implementing the present invention is to build a sensitive mail interception system, which is composed of a client and a server.
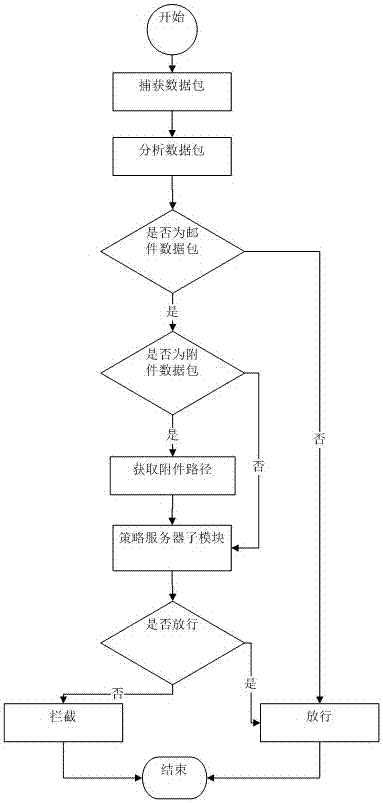
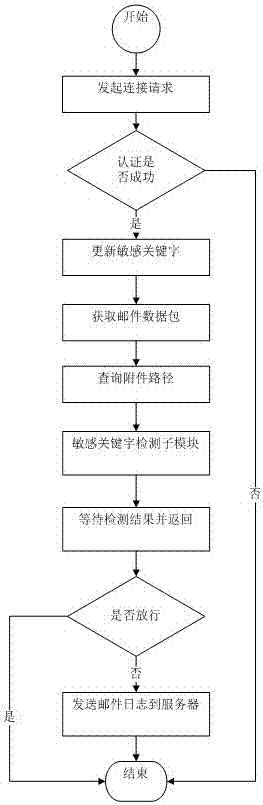
[0051] The client is a user computer installed with a sensitive email detection client module, which is responsible for the following work: (1) Sensitive keyword detection, multi-keyword search of email data to determine whether the email contains sensitive keywords; (2) Email Interception, intercepting sensitive emails sent by users; (3) Policy update, the policy service module completes the policy update operation, and executes updates according to the policies issued by the server to adjust the customer's security policy in real time; (4) Sensitive email reminders, put The keywords contained in the intercepted sensitive emails are returned to the user in a pop-up interface.
[0052] The server is a computer installed with a sensitive mail detection server module and a database module, and the computer is deployed at any ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com