Ways to protect against web attacks
A whitelist and sub-process technology, applied in the field of web application security, can solve the problems that WAF cannot quickly defend against unknown attacks, it is difficult to protect against unknown attacks, and it is difficult to quickly defend
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The detailed features and advantages of the present invention are described in detail below in the specific embodiments, the content of which is sufficient to enable any person skilled in the art to understand the technical content of the present invention and implement it accordingly, and according to the specification, claims and drawings disclosed in this specification , those skilled in the art can easily understand the related objects and advantages of the present invention.
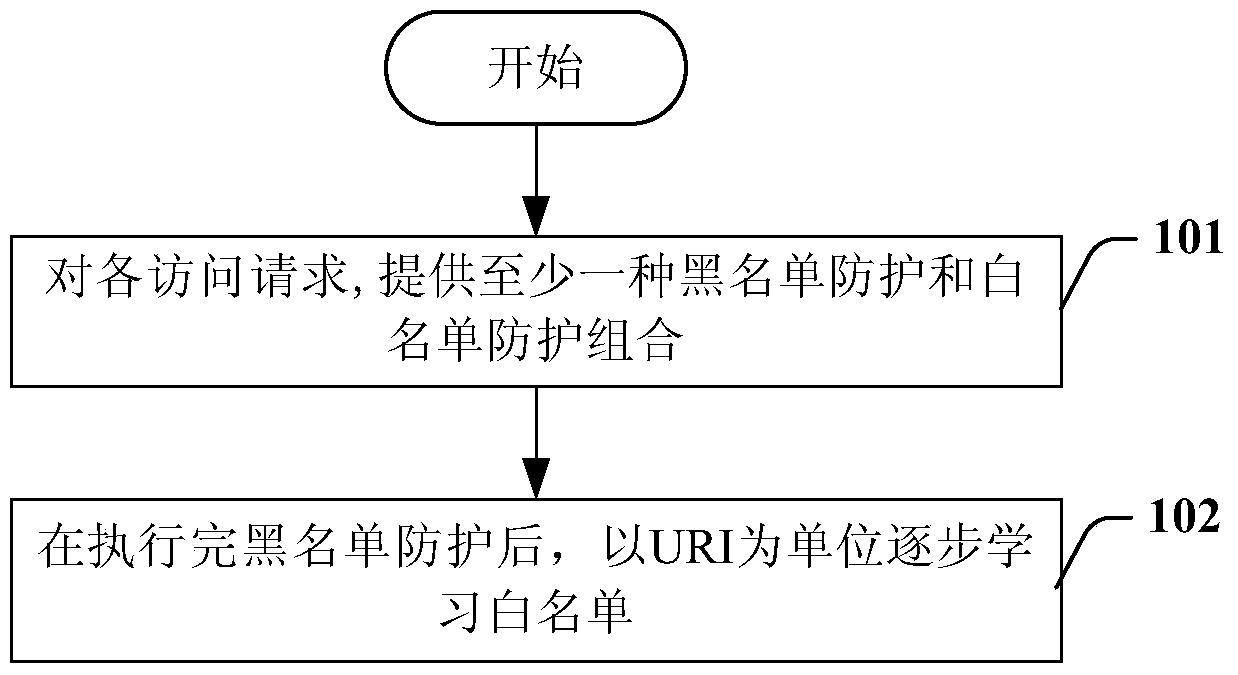
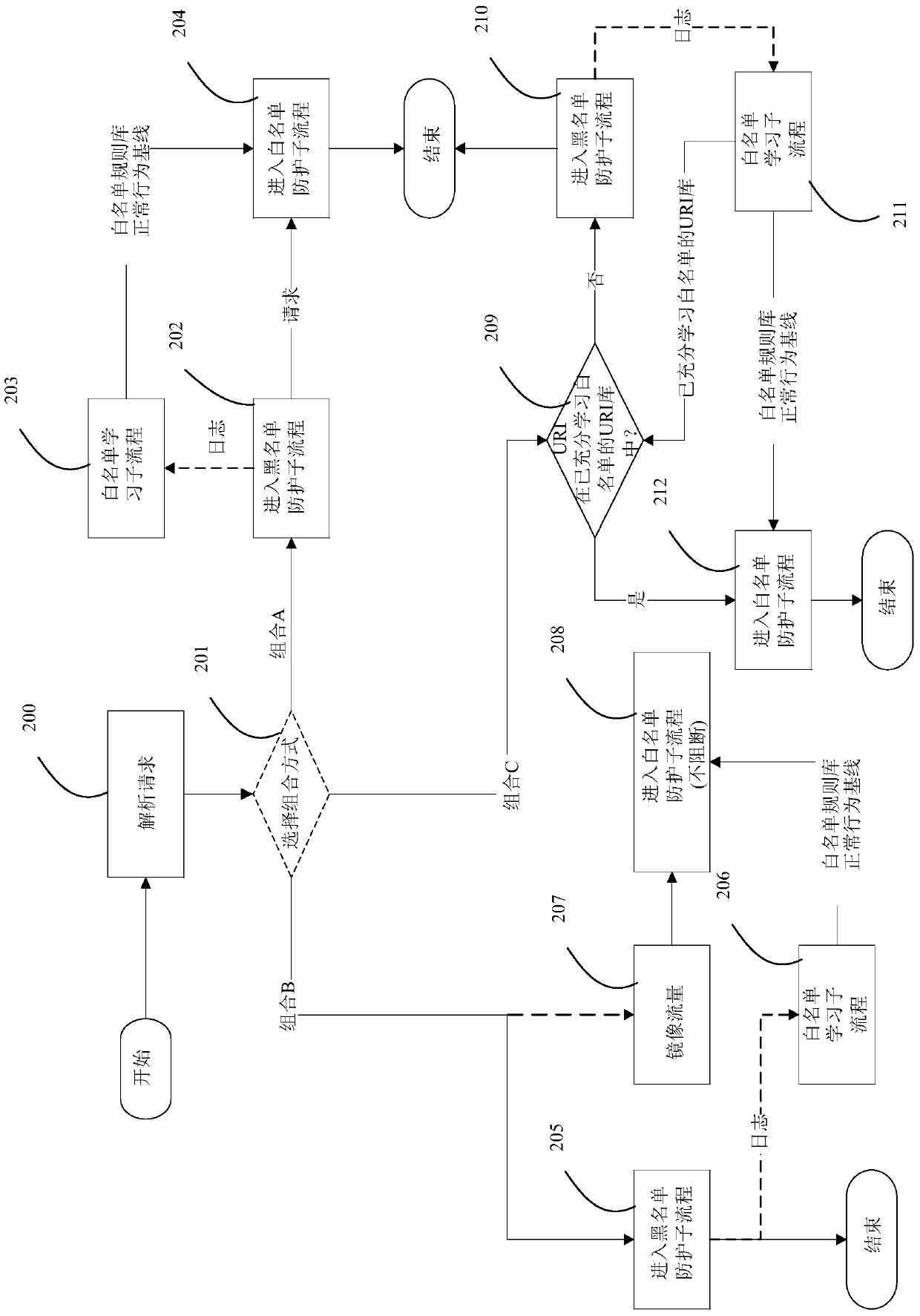
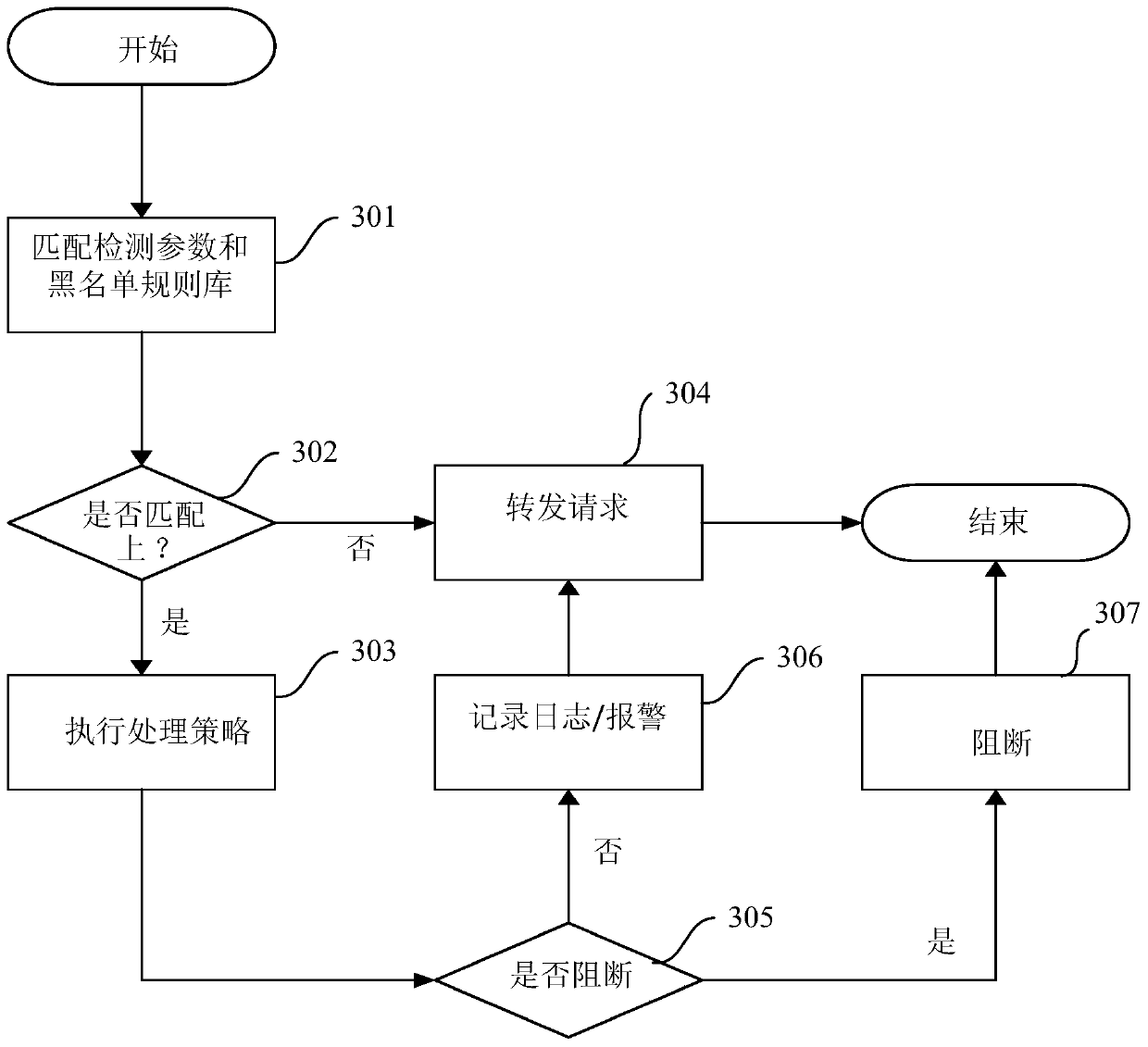
[0030] Embodiments of the present invention describe a method of protecting against web attacks that uses blacklist protection and whitelist protection in combination. Blacklist protection mainly extracts the attack signature library by collecting known vulnerabilities, so it can protect against known attacks. Whitelist protection is mainly aimed at the traffic of the website. After a period of study, a set of normal behavior baselines can be established to protect against unknown attacks. I...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com