Method and system for remote initialization of Internet of Things virtual subscriber identity module card
A virtual user and identification module technology, applied in the field of the Internet of Things, can solve problems such as insecurity, users cannot initialize operations, steal or tamper with virtual SIM card data, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
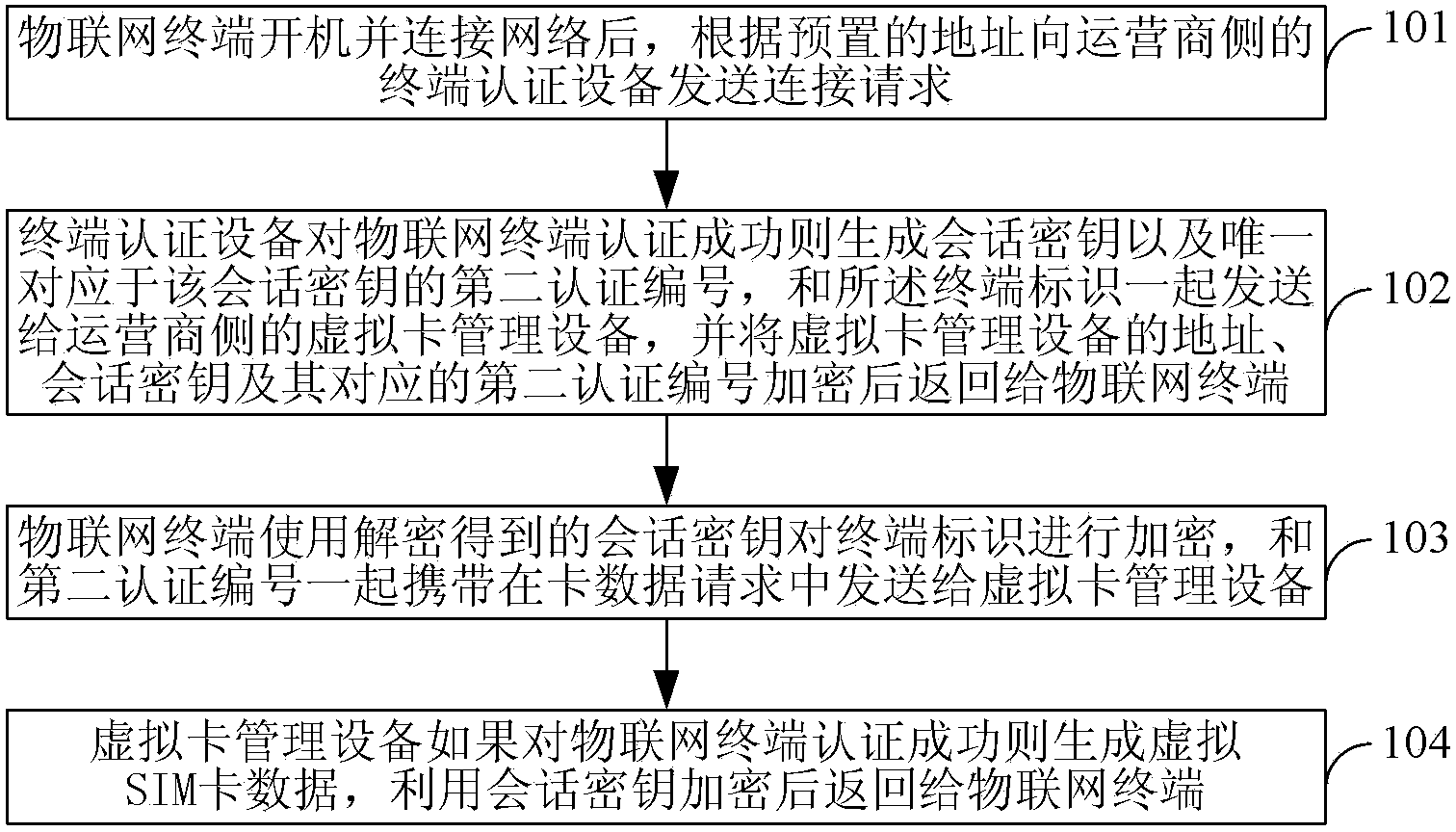
[0048] Embodiment 1. A method for initializing a virtual SIM card of the Internet of Things, such as figure 1 shown, including:
[0049] 101. After the Internet of Things terminal is turned on and connected to the Internet, it sends a connection request to the terminal authentication device on the operator side according to the preset address, which carries the terminal identifier encrypted by the preset root key and the preset unique corresponding to the first certification number of said root key;
[0050] 102. After the terminal authentication device receives the connection request, it decrypts the root key corresponding to the first authentication number carried in the connection request to obtain the terminal identifier, and if the authentication of the IoT terminal is successful, generates The session key and the second authentication number uniquely corresponding to the session key are sent together with the terminal identifier to the virtual card management device on ...
Embodiment 2
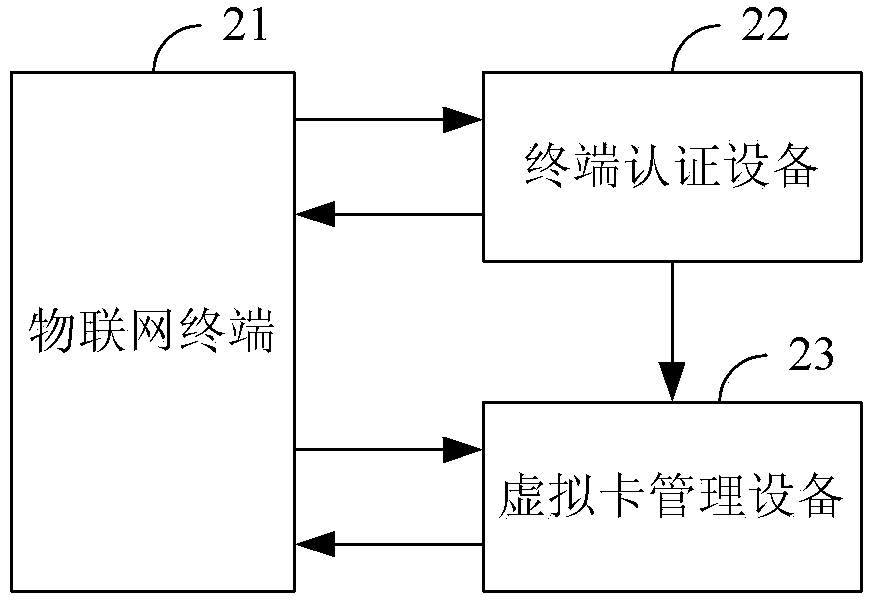
[0094] Embodiment 2, an initialization system of a virtual SIM card of the Internet of Things, such as figure 2 shown, including:
[0095] IoT terminal 21, terminal authentication device 22 and virtual card management device 23 on the operator side;
[0096] The IoT terminal 21 is configured to send a connection request to the terminal authentication device 22 according to a preset address after it is turned on and connected to the Internet, which carries a terminal identifier encrypted by a preset root key, and a preset , the first authentication number uniquely corresponding to the root key; after receiving the information returned by the terminal authentication device 22, use the root key to decrypt, and use the decrypted session key to perform the terminal identification After encryption, carry it in the card data request and send it to the virtual card management device 23;
[0097] The terminal authentication device 22 is configured to decrypt the root key correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com