Accessory device authentication
A kind of accessory equipment and equipment technology, applied in digital data authentication, digital data processing parts, internal/peripheral computer component protection, etc., can solve problems such as inefficiency, danger, and reduced battery life
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] overview
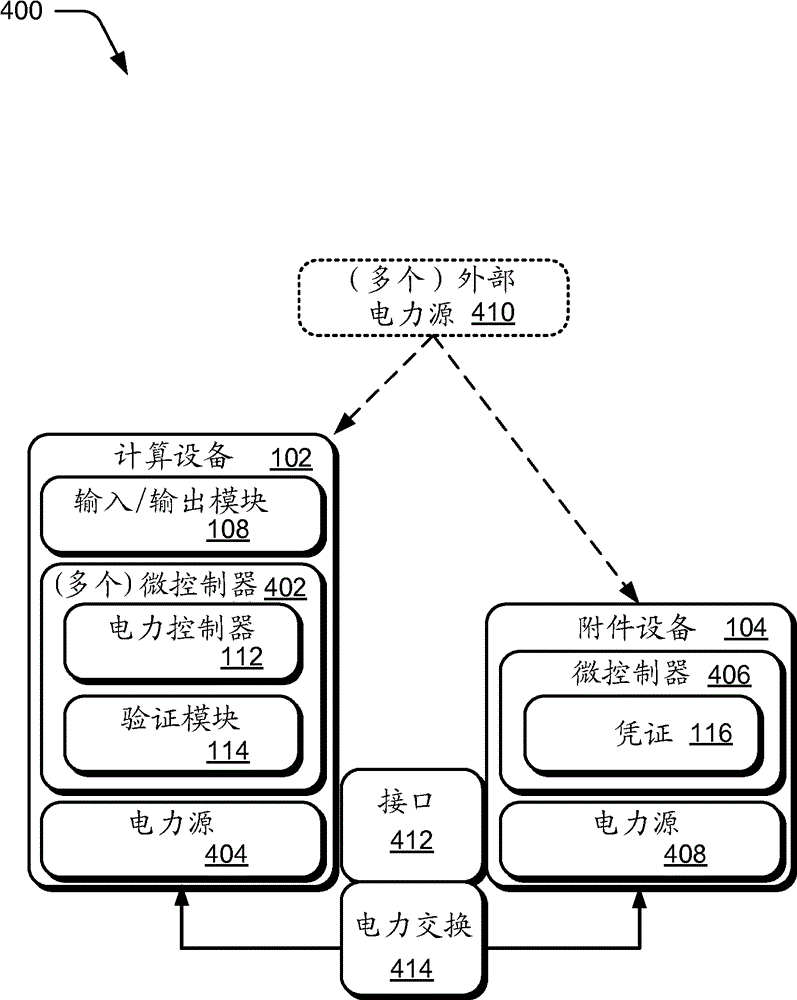
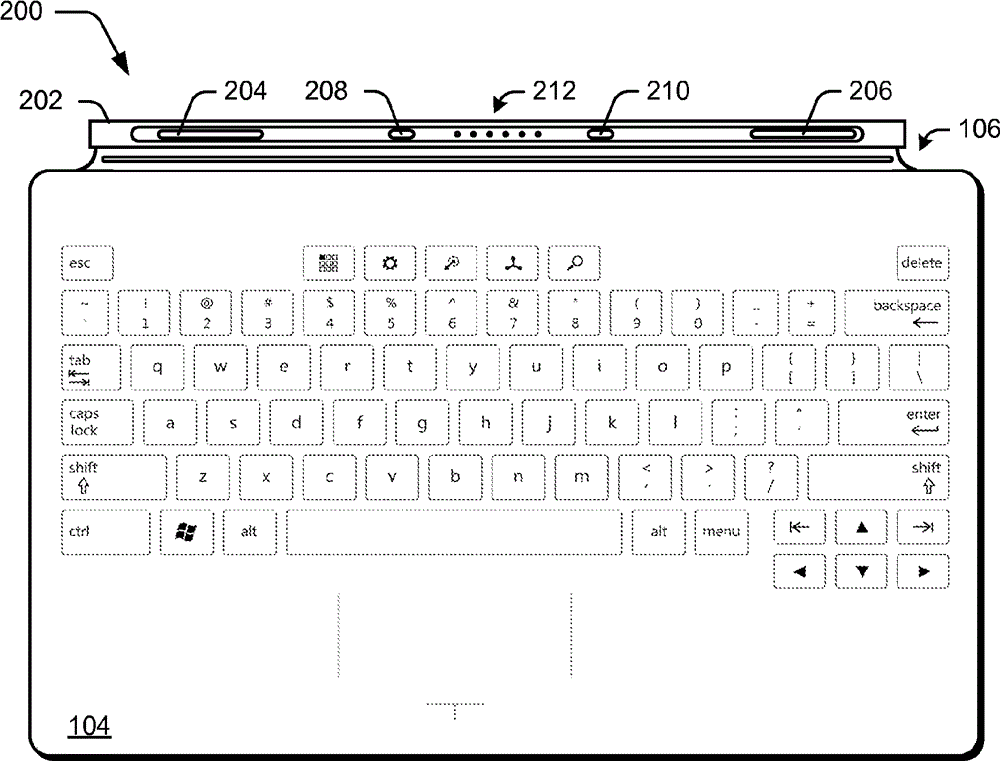
[0012] Enabling an accessory device to arbitrarily exchange power with a host device may reduce battery life in unintended ways, and / or may be inefficient and even dangerous if power transfer occurs between the host and an incompatible device.
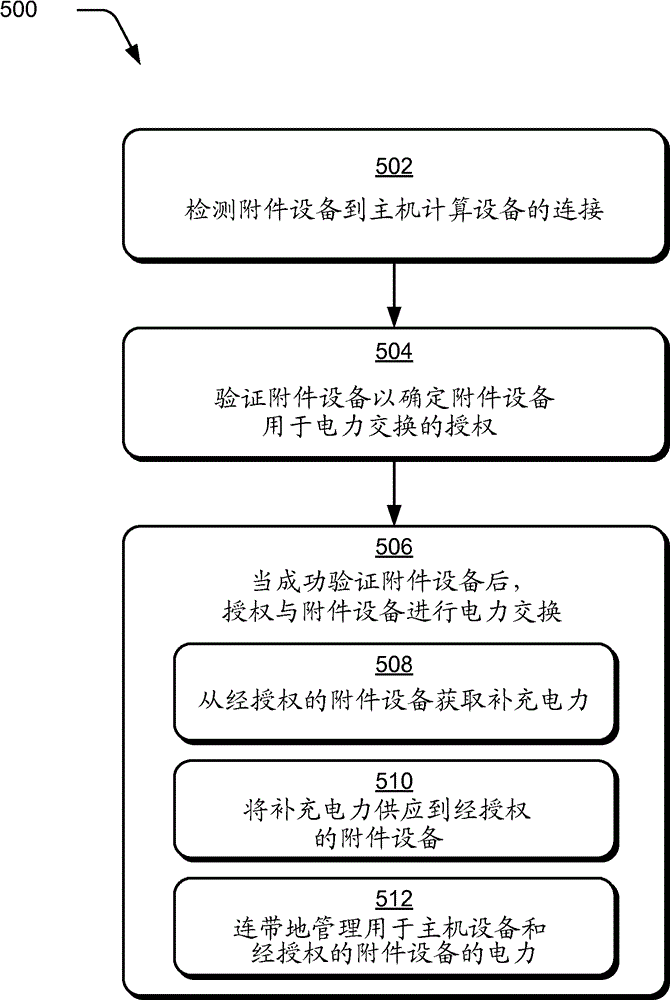
[0013] Accessory device verification techniques are described. In one or more embodiments, a connection of the accessory device to the host computing device is detected. In response to detection, an authentication sequence may occur to verify the identity and / or capabilities of the accessory device. Upon successful authentication of the accessory device, the host device can authorize the accessory device for power exchange interactions with the host device. The host device can then draw supplemental power from a power source associated with the authorized accessory device, such as a battery or power adapter. In some scenarios, the host device can also enable the accessory device to obtain and use power suppli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com