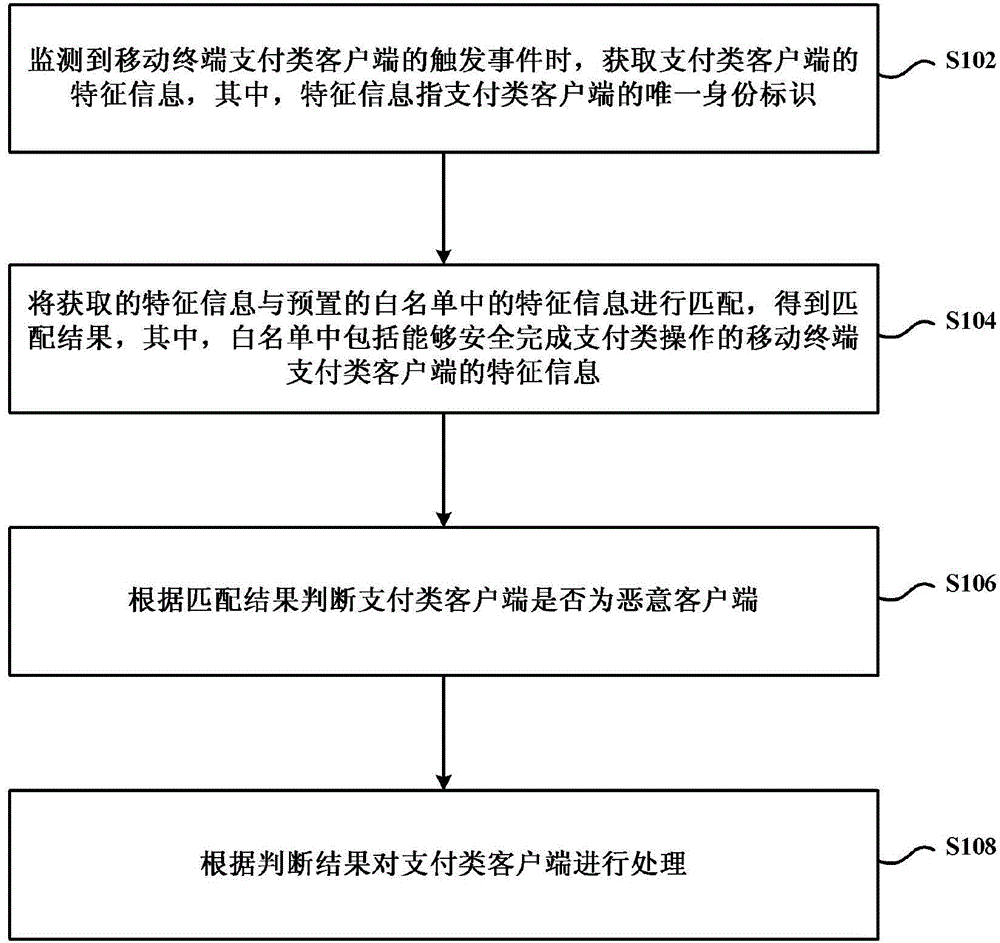
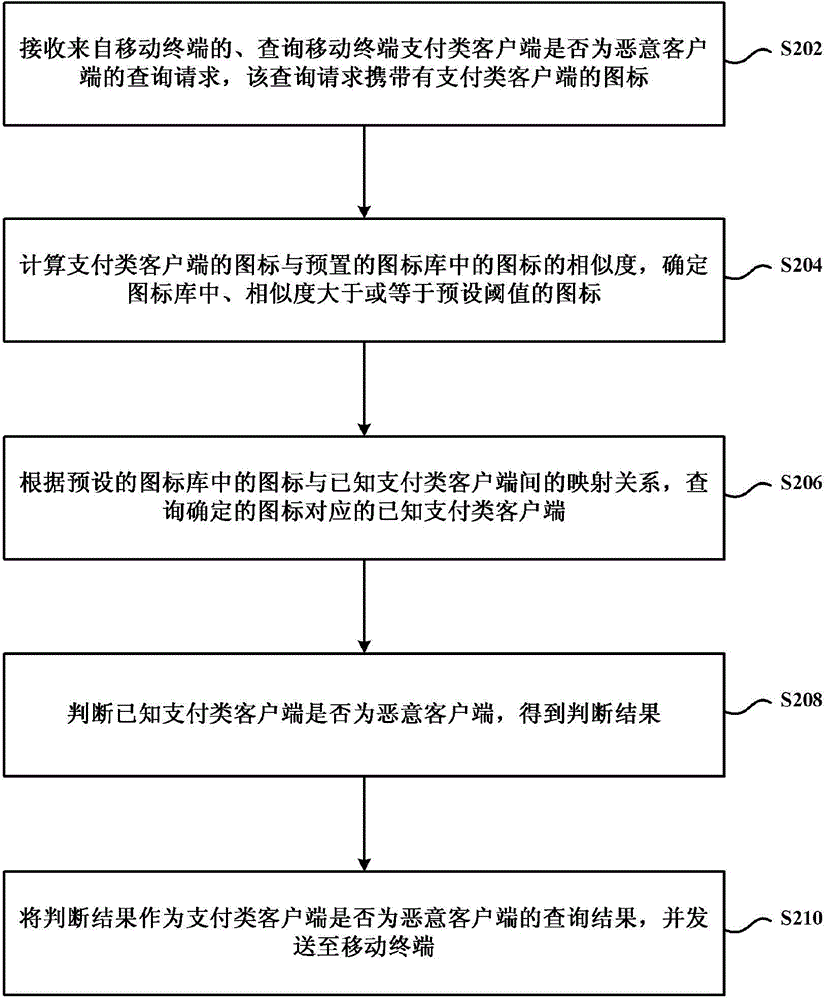
Mobile payment security protection method, mobile payment security protection device and cloud server
A mobile payment and security technology, applied in the payment system, payment system structure, equipment, etc., can solve problems such as user loss, user privacy, traffic, phone bill theft, poor protection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
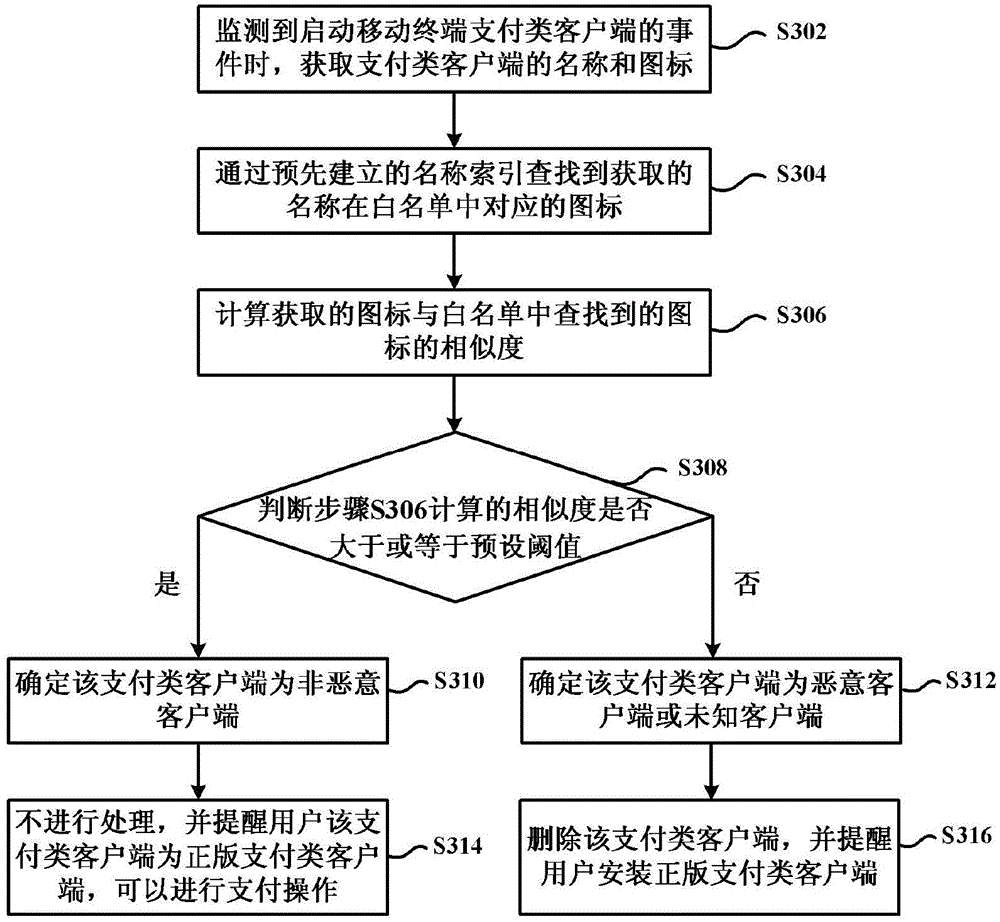
[0128] image 3 It shows another flow chart of the mobile payment security protection method at the mobile terminal side according to an embodiment of the present invention. In this embodiment, the similarity of the icons is used to effectively identify the counterfeit clients that counterfeit the names of genuine payment clients and highly emulate the icons of genuine payment clients, and deal with them in a timely manner. like image 3 As shown, the method includes the following steps S302 to S316.
[0129] Step S302, when an event of starting the payment client of the mobile terminal is detected, acquire the name and icon of the payment client.
[0130] Step S304, searching for the icon corresponding to the obtained name in the white list through the pre-established name index.
[0131] Step S306, calculating the similarity between the acquired icon and the icon found in the white list.
[0132] Step S308, judging whether the similarity calculated in step S306 is greate...
Embodiment 2
[0140] Figure 4 A third flow chart of a method for protecting mobile payment security at the mobile terminal side according to an embodiment of the present invention is shown. In this embodiment, the signature information is used to effectively identify the payment client whose name remains unchanged but whose signature is changed and which has been packaged with a Trojan horse or a virus program twice, and handle it in a timely manner. like Figure 4 As shown, the method includes the following steps S402 to S414.
[0141] Step S402, when an event of installing a payment client on a mobile terminal is detected, acquire the name and signature of the payment client.
[0142] Step S404, searching for the signature corresponding to the obtained name in the white list through the name index established in advance.
[0143] Step S406, judging whether the acquired signature is the same as the signature found in the whitelist, if yes, proceed to step S408; otherwise, proceed to st...
Embodiment 3
[0150] Figure 5 A flow chart of a mobile payment security protection method combining a mobile terminal and a cloud server according to an embodiment of the present invention is shown. As shown in 5, the method includes the following steps S502 to S518.
[0151] Step S502, when an event of starting the payment client of the mobile terminal is detected, obtain the package name, MD5 and SHA1 of the payment client.
[0152] Step S504 , sending an inquiry request to the cloud server for inquiring whether the payment client is a malicious client, wherein the inquiry request carries the package name, MD5 and SHA1 of the payment client.
[0153] Step S506, the cloud server receives an inquiry request from the mobile terminal to inquire whether the payment client of the mobile terminal is a malicious client, and the inquiry request carries the package name, MD5 and SHA1 of the payment client.
[0154] Step S508, the cloud server finds the MD5 and SHA1 corresponding to the obtained ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com