Active defense method and device based on Linux system
A technology of active defense and execution system, applied in the computer field, can solve the problem of no active defense system and method, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
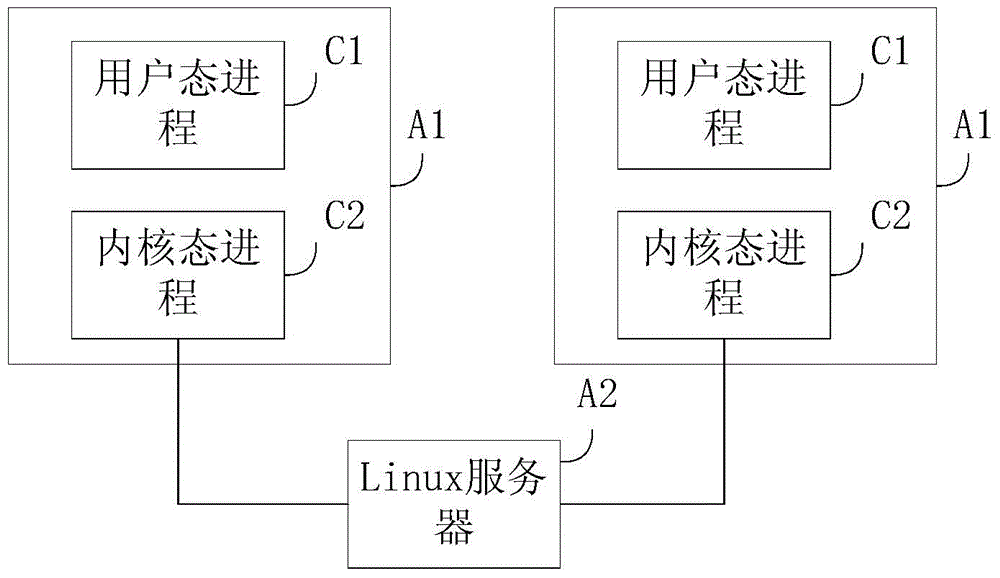
[0054] The embodiment of the present invention provides an active defense method based on a Linux system, which is suitable for a Linux host, and the Linux system includes a user state process and a kernel state process, see figure 2 , the method includes:
[0055] Step 101: Monitor system calls of the Linux kernel by using a hook.
[0056] Step 102: When it is detected that the system call with the Hook set is called by the user-mode process, determine whether the user-mode process exists in the whitelist.
[0057]Step 103: When the user-mode process exists in the whitelist, allow the user-mode process to call the system call;
[0058] When the user-mode process does not exist in the whitelist, the user-mode process is prohibited from calling system calls.
[0059] Wherein, the white list includes one or more user mode processes that are allowed to execute system calls.
[0060] The embodiment of the present invention monitors the system call of the Linux kernel by adopti...
Embodiment 2
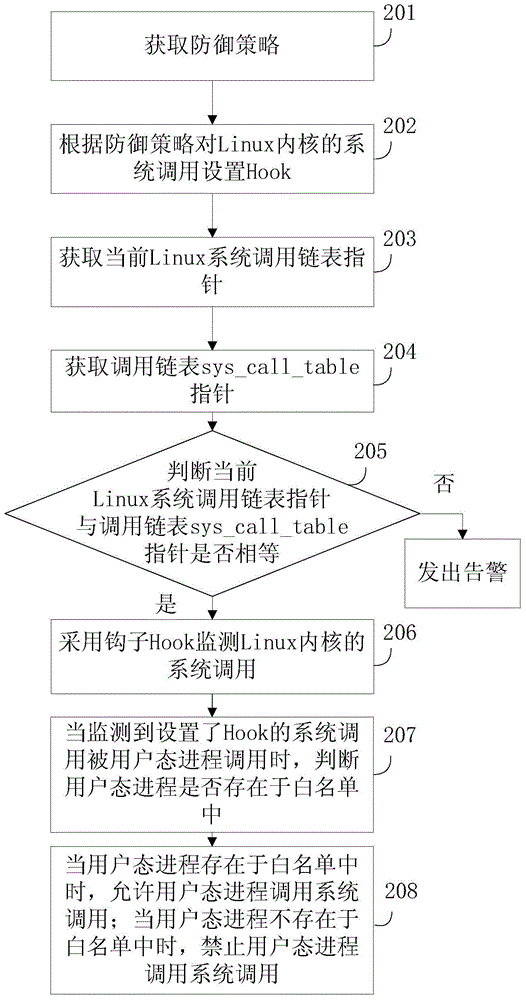
[0062] The embodiment of the present invention provides an active defense method based on Linux system, which is suitable for Linux hosts, see image 3 , the method includes:
[0063] Step 201: Obtain a defense strategy, where the defense strategy includes a Hook strategy and a white list.
[0064] During specific implementation, step 201 may include:
[0065] Receive the defense policy delivered by the server. Specifically, the defense strategy is delivered by the server to the user-mode process, and then sent to the kernel-mode process by the user-mode process.
[0066] Of course, in this embodiment, the defense policy is uniformly configured by the Linux server. In the scenario of multiple Linux hosts, the uniform configuration of the host defense policy is realized through the server to facilitate management. In the case of fewer hosts, defense policies can also be set directly on the host.
[0067] Further, this step 201 can be realized by the kernel state process in ...
Embodiment 3
[0092] The embodiment of the present invention also provides an active defense device based on Linux system, see Figure 4 , the device consists of:
[0093] Monitoring module 301, for adopting hook Hook to monitor the system call of Linux kernel;
[0094] Judgment module 302, for when detecting that the system call that Hook is set is called by user mode process, judge whether user mode process exists in white list;
[0095] A processing module 303, configured to allow the user-mode process to call a system call when the user-mode process exists in the whitelist;
[0096] When the user-mode process does not exist in the whitelist, the user-mode process is prohibited from calling system calls.
[0097] Wherein, the white list includes one or more user mode processes that are allowed to execute system calls.
[0098] The embodiment of the present invention monitors the system call of the Linux kernel by adopting the hook Hook, when monitoring the system call that Hook is set...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com