Method and system for viewing embedded device log
An embedded device and log technology, applied in transmission systems, hardware monitoring, electrical components, etc., can solve problems such as reappearing abnormal status of applications, low efficiency of troubleshooting methods, and protection of product information security risks, so as to improve efficiency, Simplify viewing the effects of your process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to describe the technical content, structural features, achieved goals and effects of the present invention in detail, the following will be described in detail in conjunction with the embodiments and accompanying drawings.
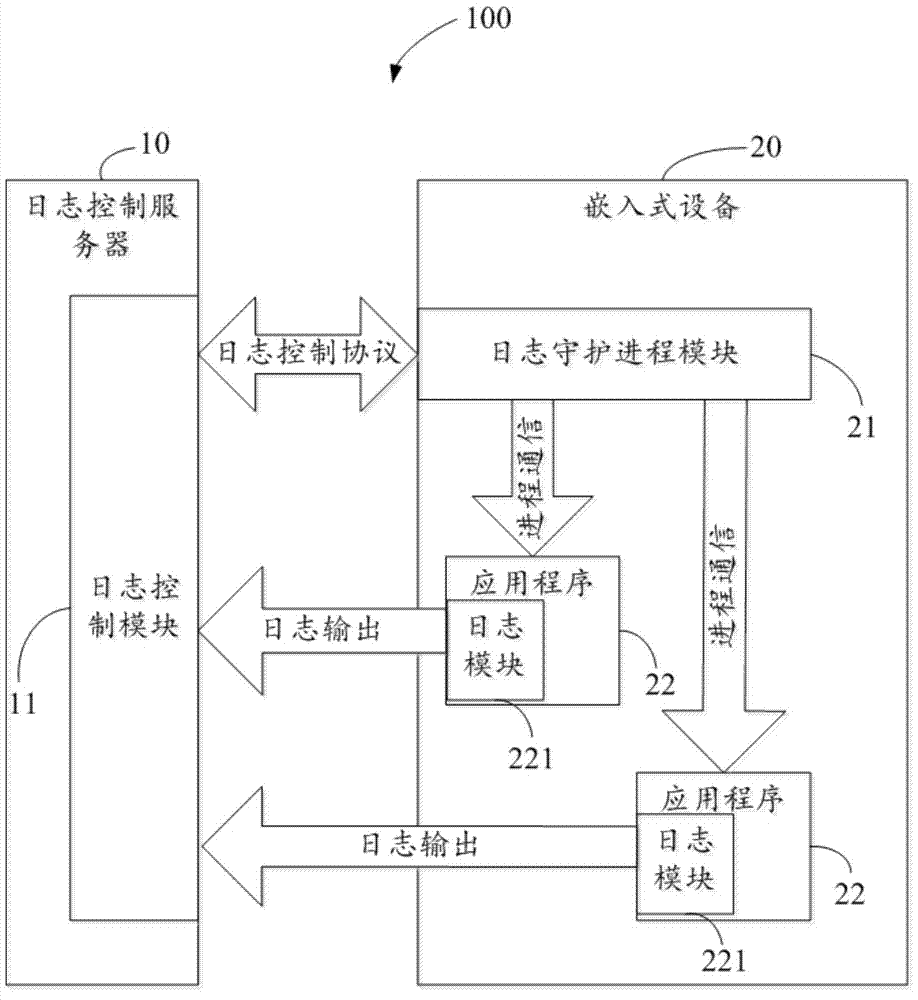
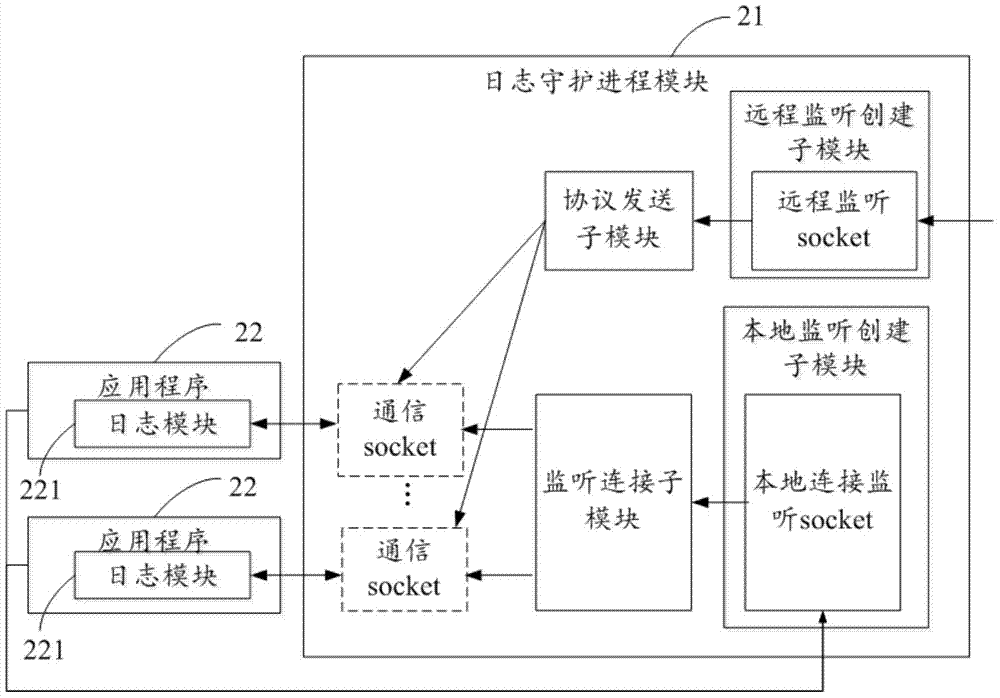
[0022] The present invention provides a system and method for viewing logs of embedded devices. By implementing a log daemon process to receive the log control protocol of the server, when receiving the log control protocol, it notifies other applications, and then the log modules in other applications According to the content of the agreement, the log information in the application program to which it belongs is transmitted to the log control server. The unified hierarchical management of log information of embedded devices is realized, and the viewing process of log information of embedded devices is effectively simplified.
[0023] see figure 1 , is a structural block diagram of a system for viewing embedded device logs in an embodimen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com