Method and device for assigning large-scale vulnerability scanning task
A vulnerability scanning and scanning task technology, applied in the Internet field, can solve the problems of different time required for vulnerability scanning, poor rationality, and slow execution of scanning tasks by nodes, so as to improve the rationality and the efficiency of vulnerability scanning.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0084] In order to enable those skilled in the art to better understand the solution of the present invention, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings and implementation manners.
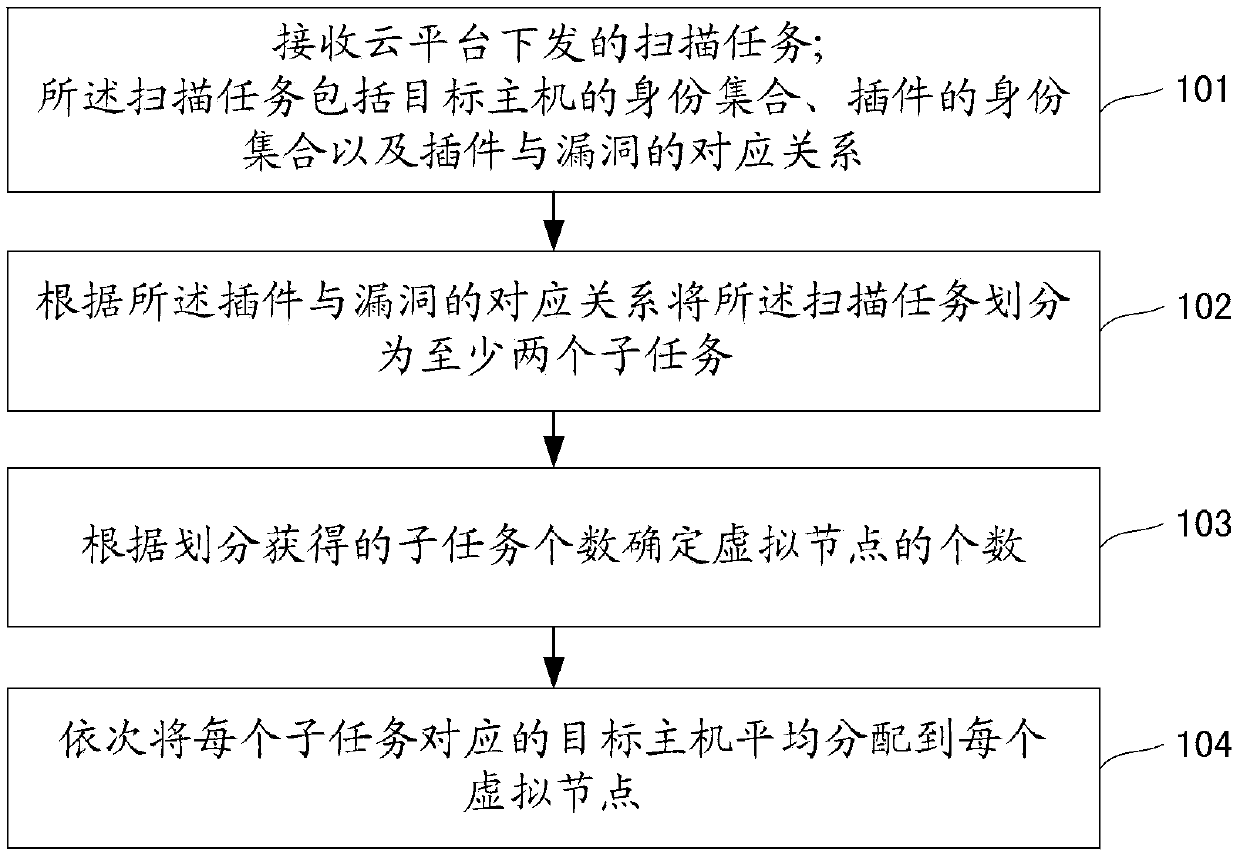
[0085] In order to realize the reasonable distribution of scanning tasks and improve the scanning efficiency, it can generally be realized through the mutual cooperation of static allocation and dynamic scheduling. For static allocation, it refers to assigning tasks to each virtual node as reasonably as possible before the task is officially executed, so as to achieve a reasonable allocation of initial resources, so that the task can achieve load balance to the greatest extent during the execution process. The task allocation method in the embodiment of the present invention is a static task allocation method, and the allocation process will be explained below.
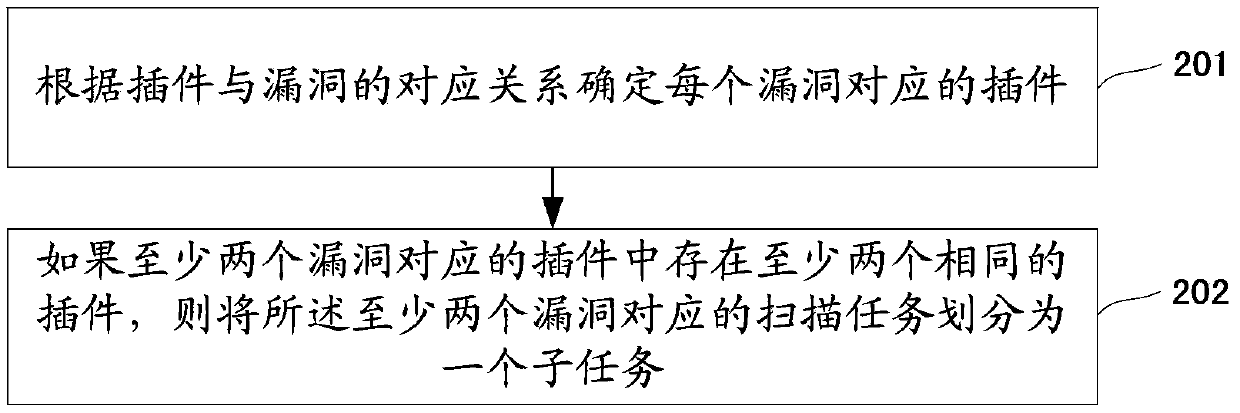
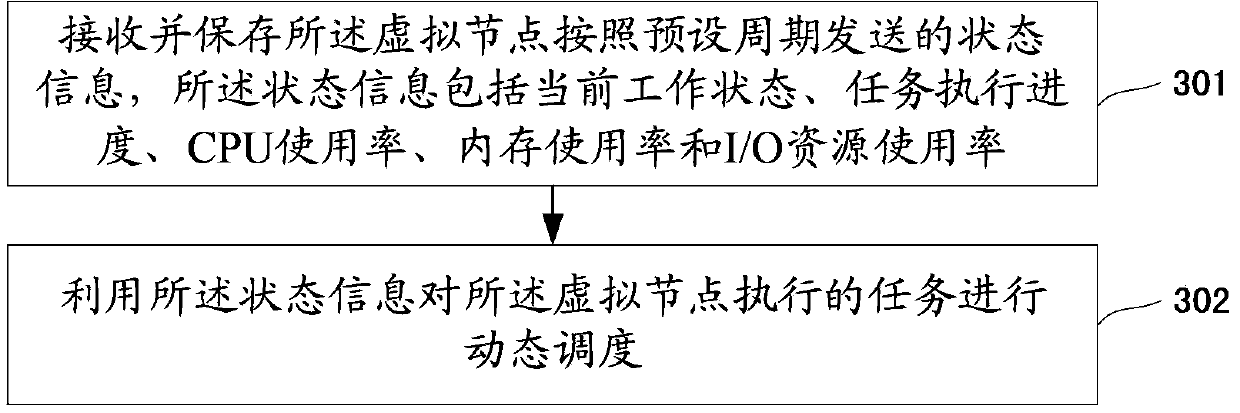
[0086] Such as figure 1 As shown, the flow chart...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com