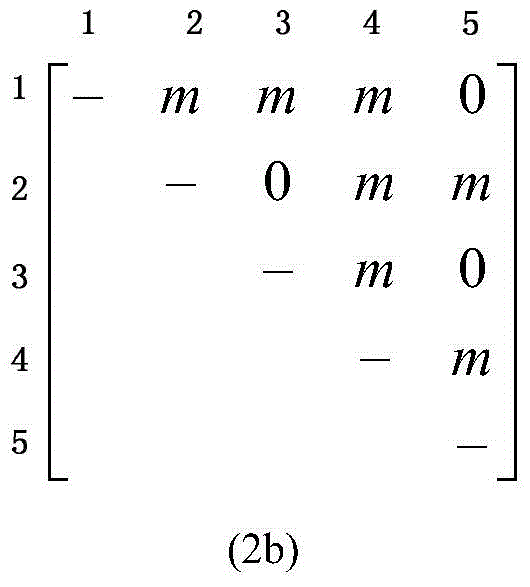A cluster-based traffic grooming and differentiation importance protection method
A technology of importance and business volume, which is applied in the field of cluster-based traffic grooming and differentiation of importance protection. It can solve problems such as excessive consumption of protection resources, failure of shared protection to achieve complete protection, and failure to consider different quantities. Achieve the effect of improving network resource utilization, reducing protection resource overhead, and fast and effective dredging
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
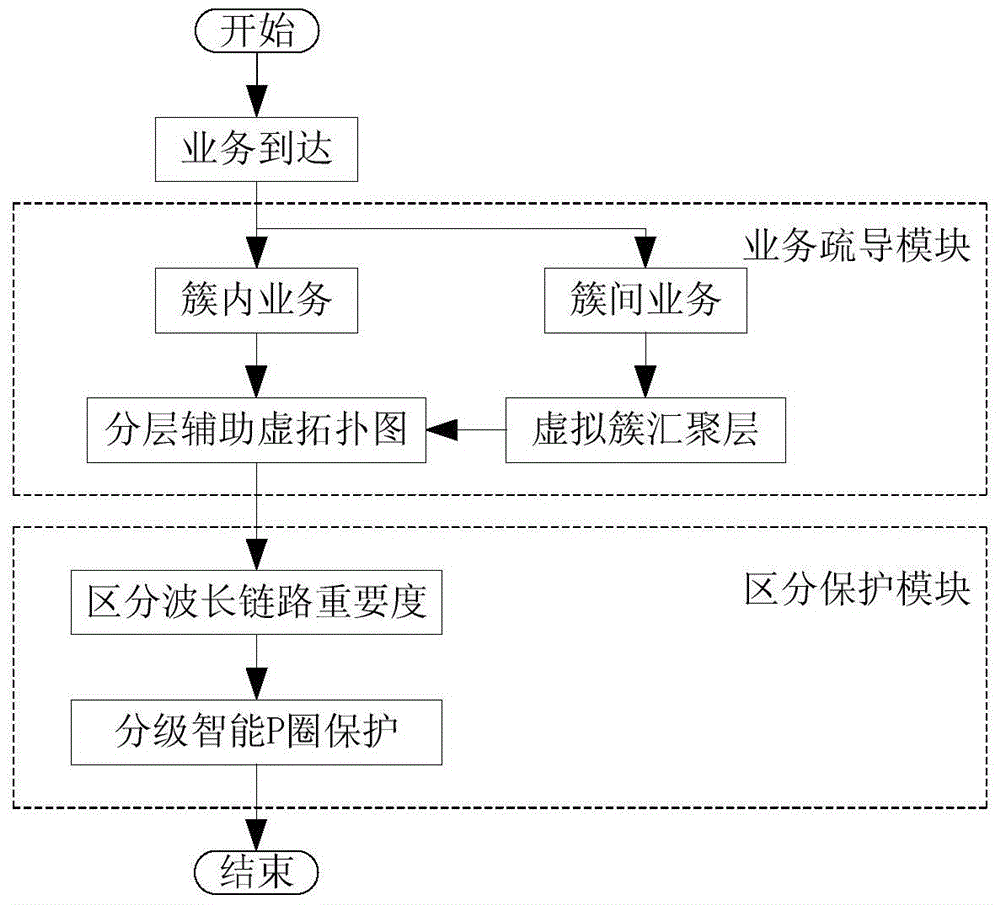
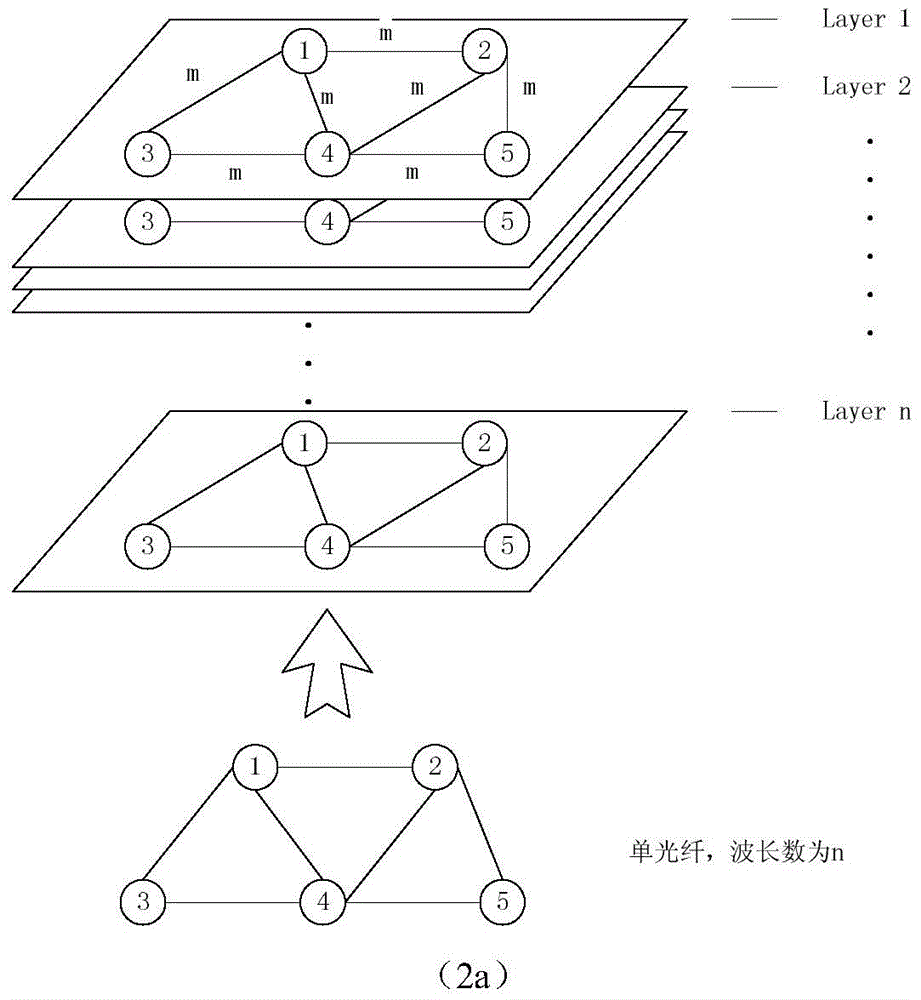
[0029] figure 1It is a flow chart of traffic grooming based on clustering and differentiated importance level protection. As shown in the figure, a business grooming module and a differentiated protection module are adopted in this method. Among them, in the business grooming module, the intra-cluster business is directly guided by the hierarchical auxiliary graph, and the inter-cluster business first uses the virtual cluster convergence layer to find the shortest path between clusters, and then maps it to the hierarchical auxiliary graph for grooming. The distinguishing protection module first perceives the proportion of each priority service in the wavelength link, evaluates its importance level, and then uses the P circle to perform single and double link fault protection respectively, and the wavelength link protected by the single link...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com