Security detection method for design of cryptographic algorithm hardware
A cryptographic algorithm and hardware design technology, applied in the security detection field of cryptographic algorithms, can solve the problems of increased chip production cost, difficult analysis conditions, low chip security, etc. Consume the simple effect of alignment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
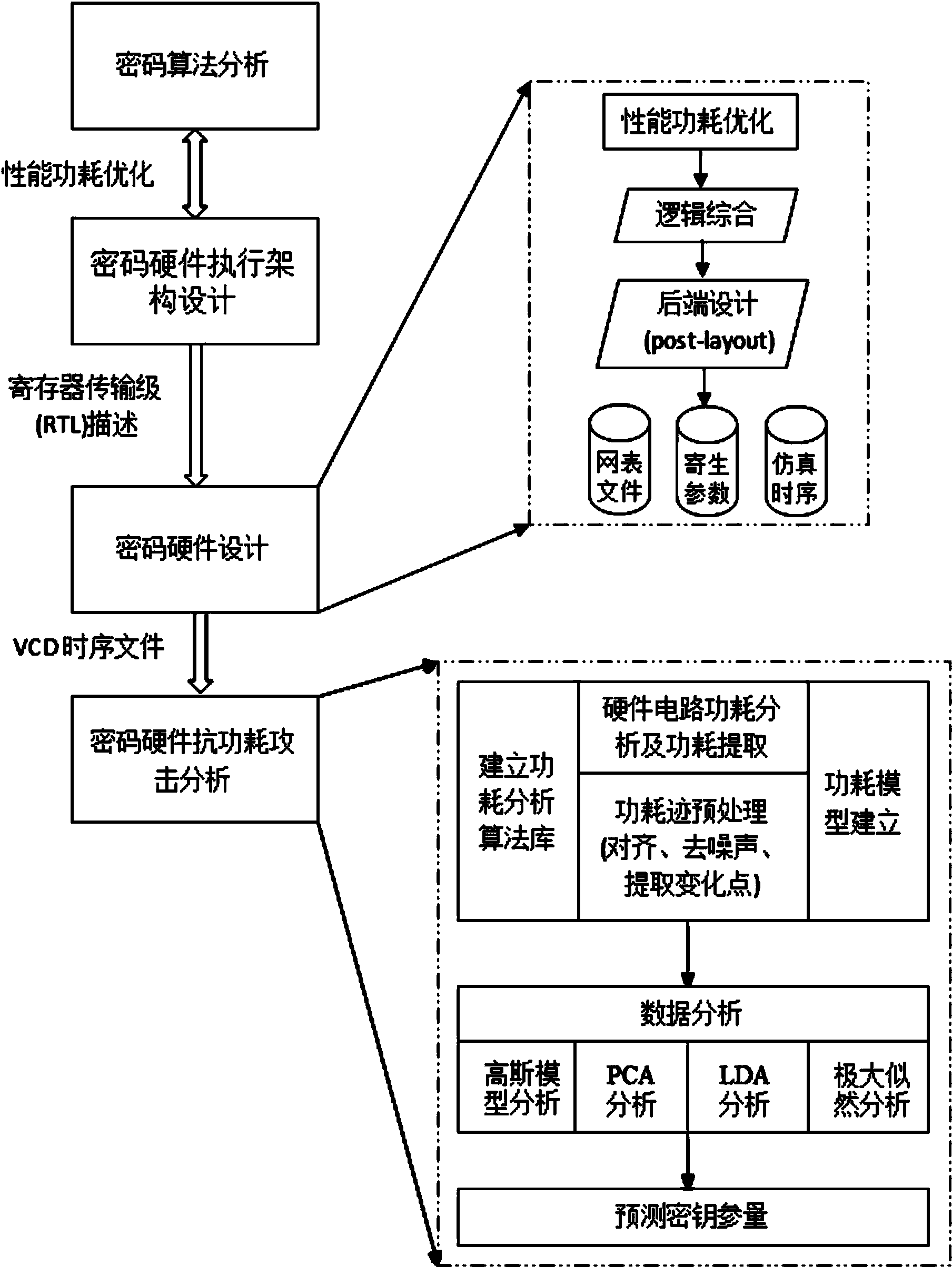
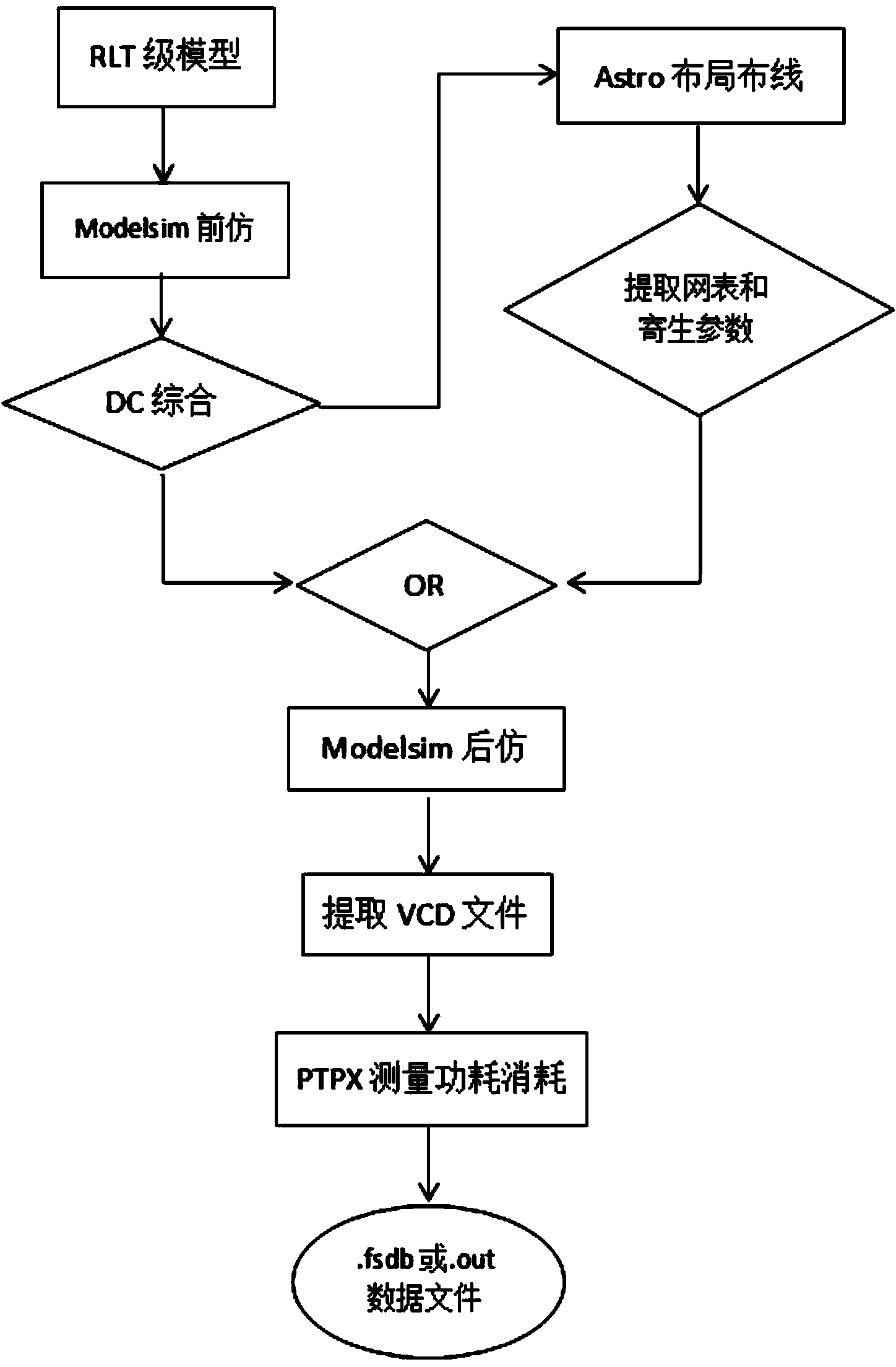
[0022] A security detection method for a cryptographic algorithm hardware design of the present invention will be described in detail below in conjunction with the embodiments and the accompanying drawings.
[0023] A security detection method for cryptographic algorithm hardware design of the present invention mainly includes four parts: public key cryptographic algorithm research, cryptographic execution algorithm hardware architecture design, cryptographic hardware circuit design, and power consumption attack resistance analysis. These four parts are closely related. The first two parts are theoretical improvements to the hardware implementation of the cryptographic algorithm. They mainly optimize the cryptographic algorithm from the perspective of theory and hardware architecture, so that the operating speed of the cryptographic chip is improved and the anti-attack performance is enhanced. The third part is to use Verilog HDL, VHDL and other hardware description languages ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com