Differential power attack testing method for DES (data encryption standard) algorithm circuit
A technology of differential power consumption attack and testing method, which is applied in the direction of electrical components, encryption devices with shift registers/memory, digital transmission systems, etc. It can solve the problem of anti-power consumption analysis characteristics of circuits that are not suitable for verifying cryptographic algorithms, and the results are credible Problems such as low precision and long verification cycle, etc., achieve the effect of shortening the design cycle, saving storage space, and fast speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
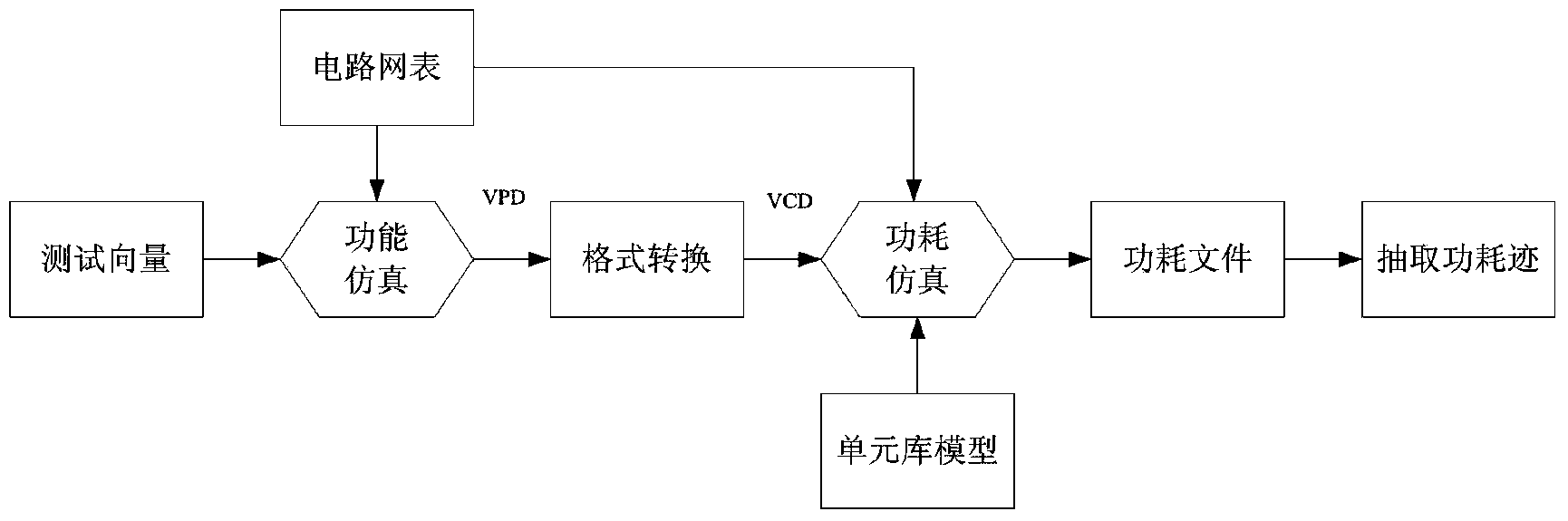
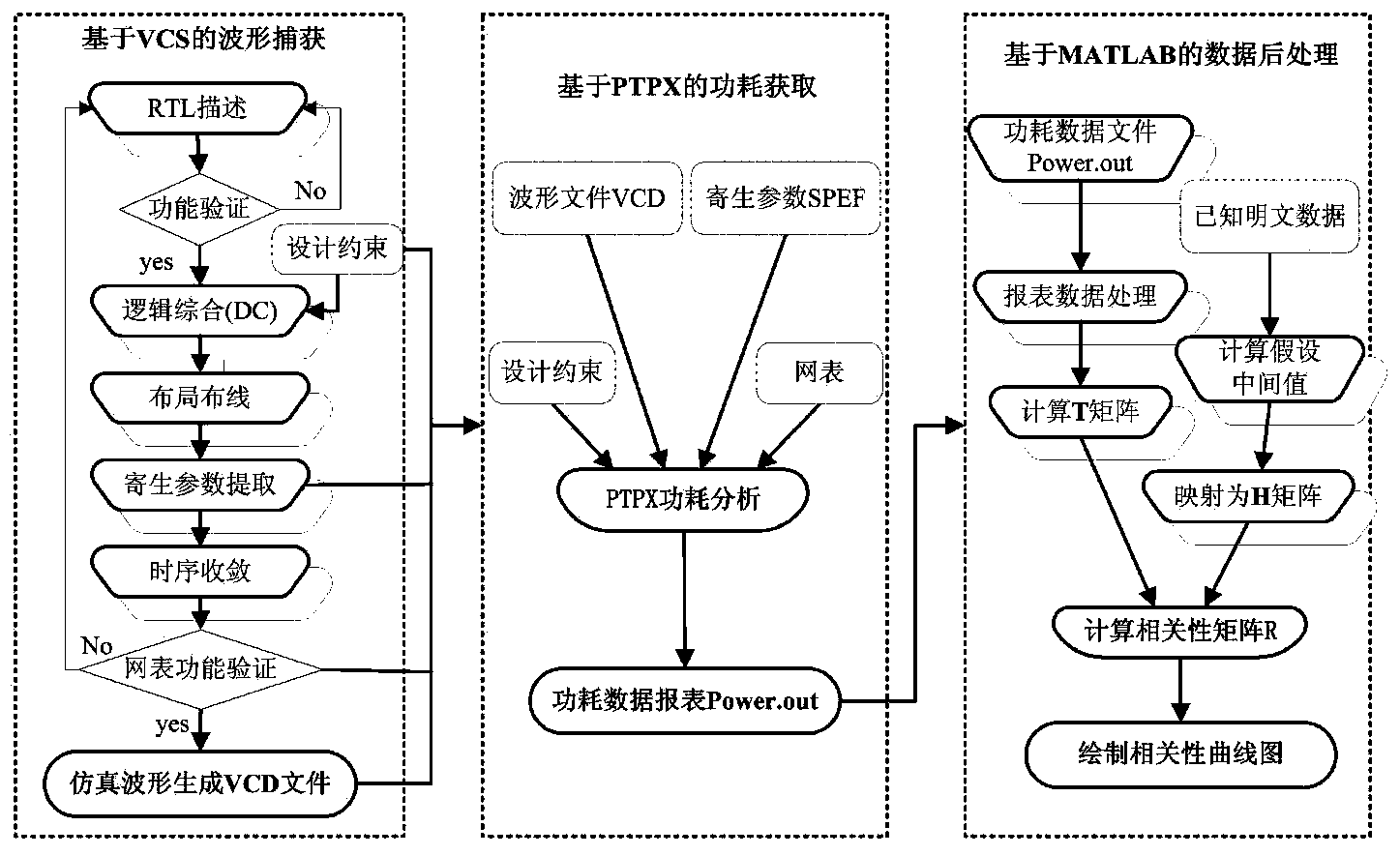
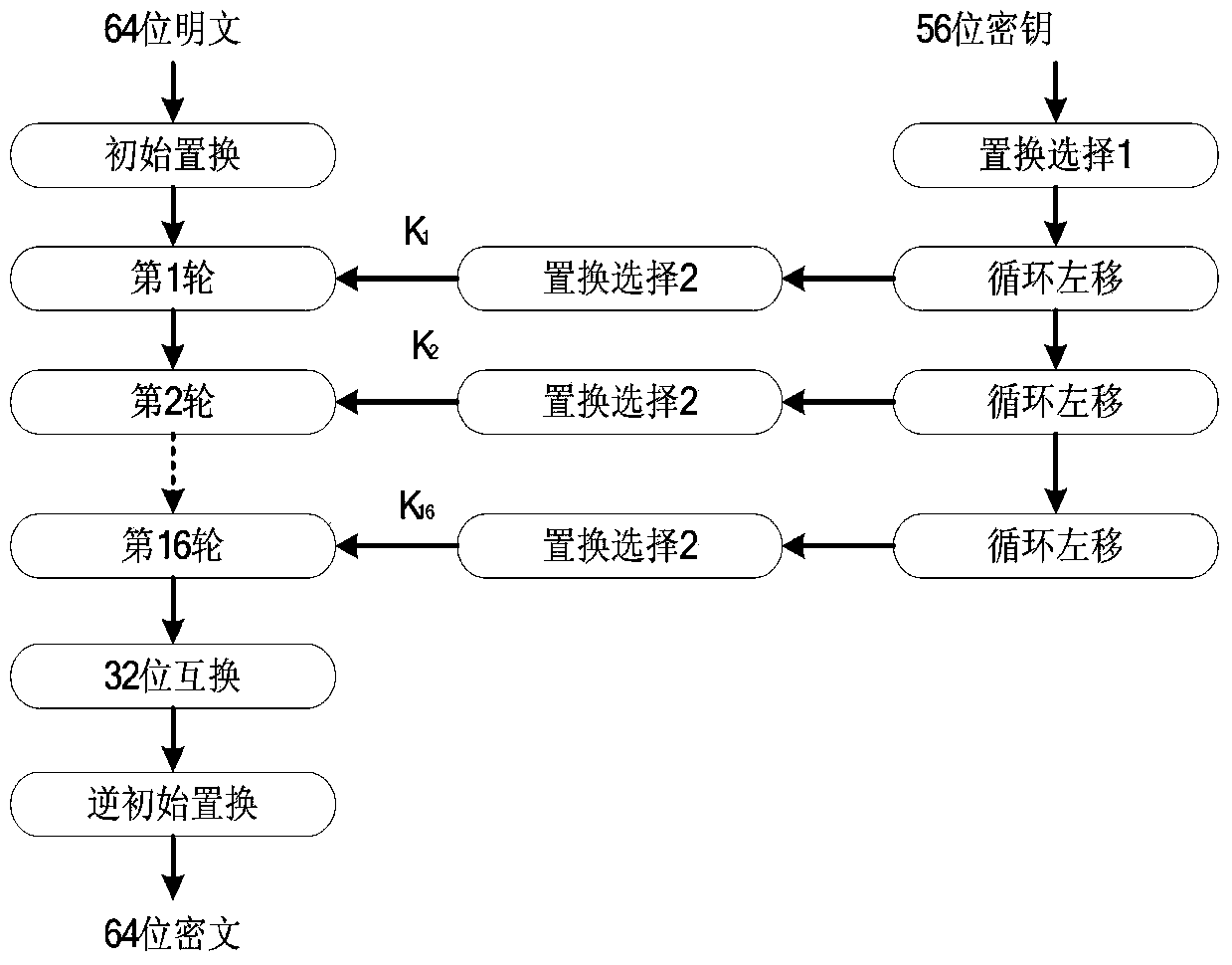
[0039] Such as figure 1 Shown is the process of obtaining power consumption samples in the present invention. First, set the working environment of the encryption algorithm circuit, that is, load a series of test vectors, such as clock, IO stimulus, random plaintext and key input, etc. The invention adopts VCS to carry out function simulation on the net list circuit of DES, and generates VPD (Vcd Plus Deltacycleon, VPD) file after the simulation is finished. This file contains the changes of various internal standard units during the operation of the encryption algorithm. The VPD file is then converted to a VCD file for use by the Power Consumption Simulation Module. The tool used by the power consumption simulation module is the PTPX tool of Synopsys Company. Properly configure PTPX, combined with the power consumption model of the cell li...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com