Method for verifying TCP (transmission control protocol) connection security
A technology of security and connection request, applied in the direction of digital transmission system, electrical components, transmission system, etc., to achieve the effect of protection and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1)
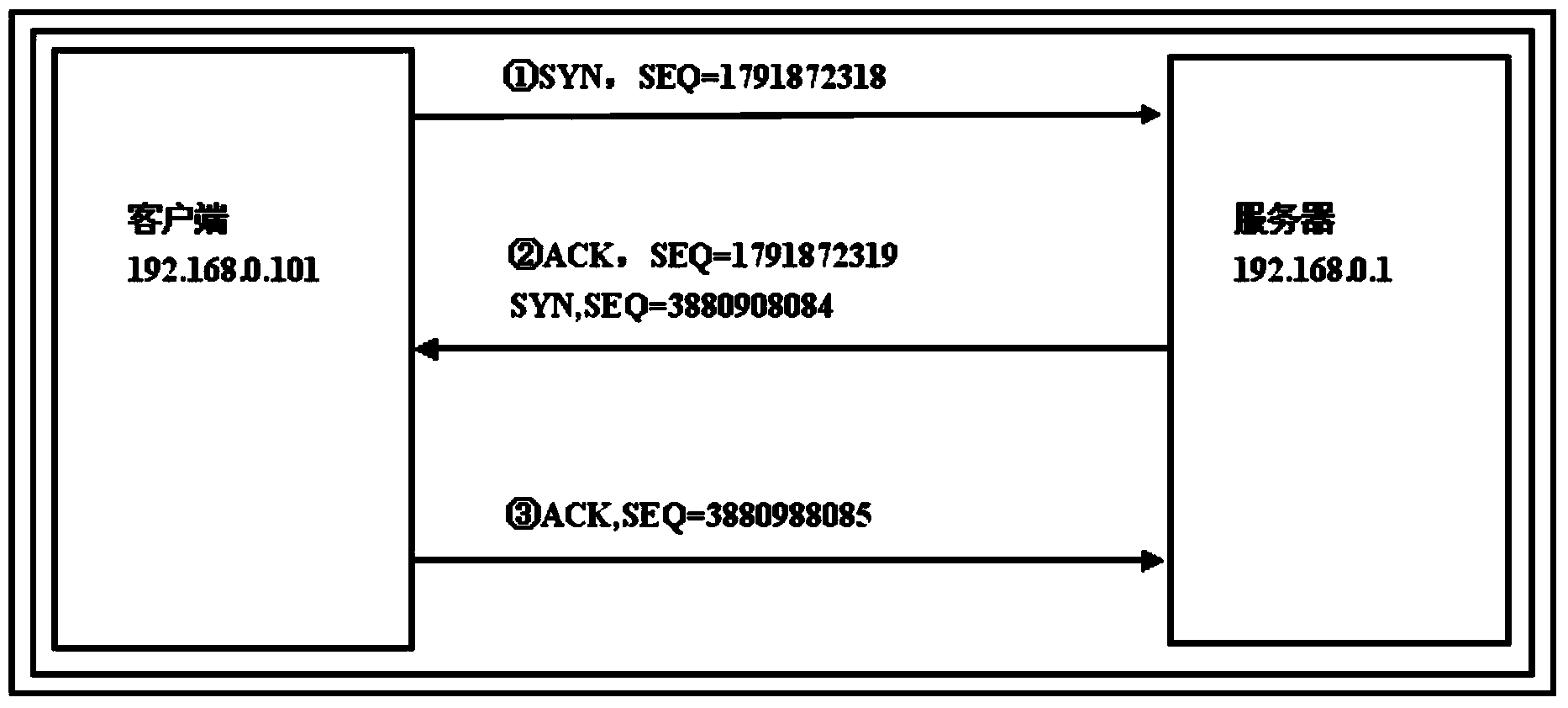
[0025] This embodiment is mainly aimed at applications using the TCP protocol. For the TCP protocol, a handshake connection must be performed before data transmission. If in the process of handshake, the inspection of connection information is added, the connection is allowed only when the connection packet contains specific information, and other ordinary connection request packets are hung up, or the packet is discarded, so that the connection cannot be completed. Subsequent attacks and theft cannot be completed. Through this approach, the security of the server can be effectively protected in the first place.
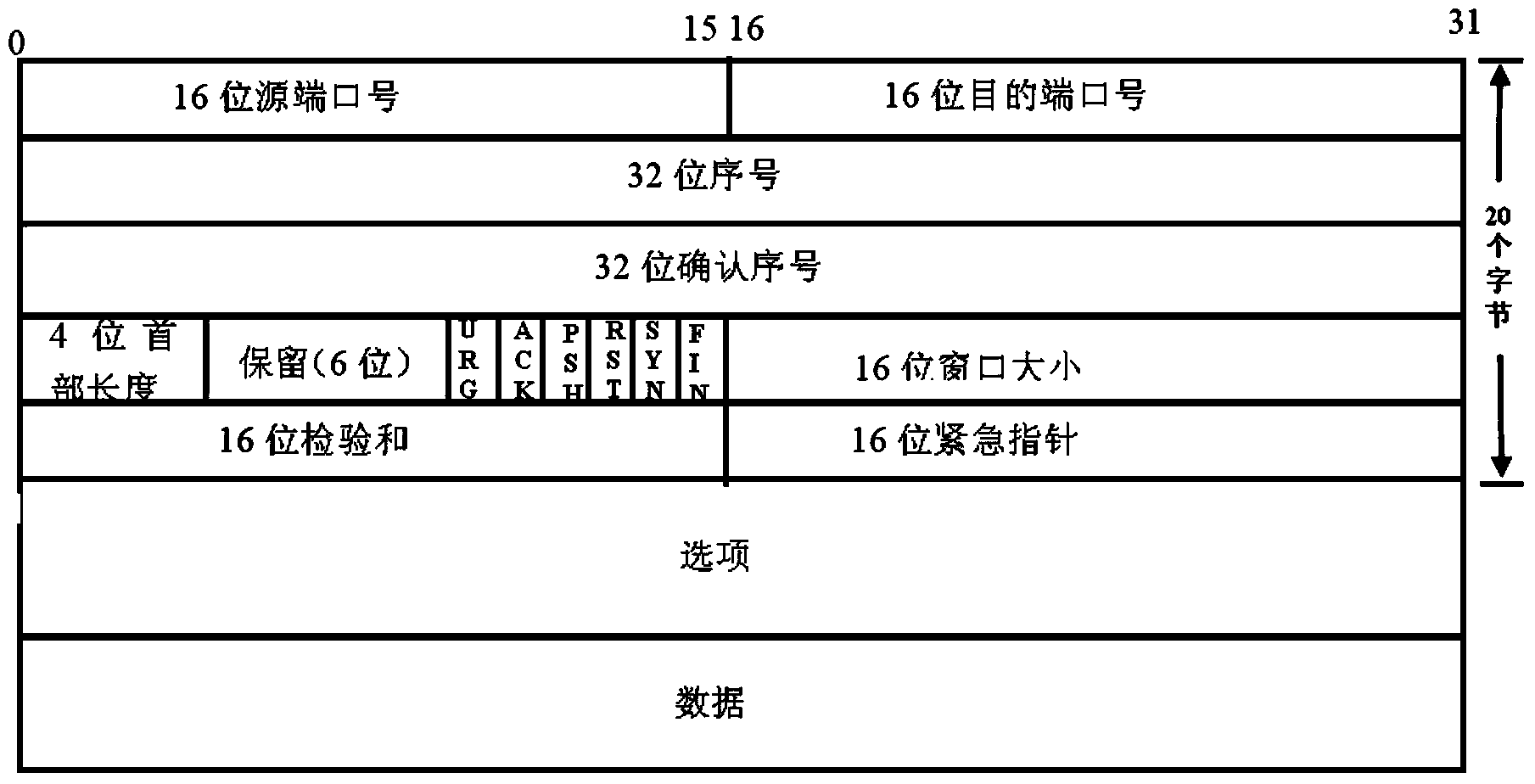
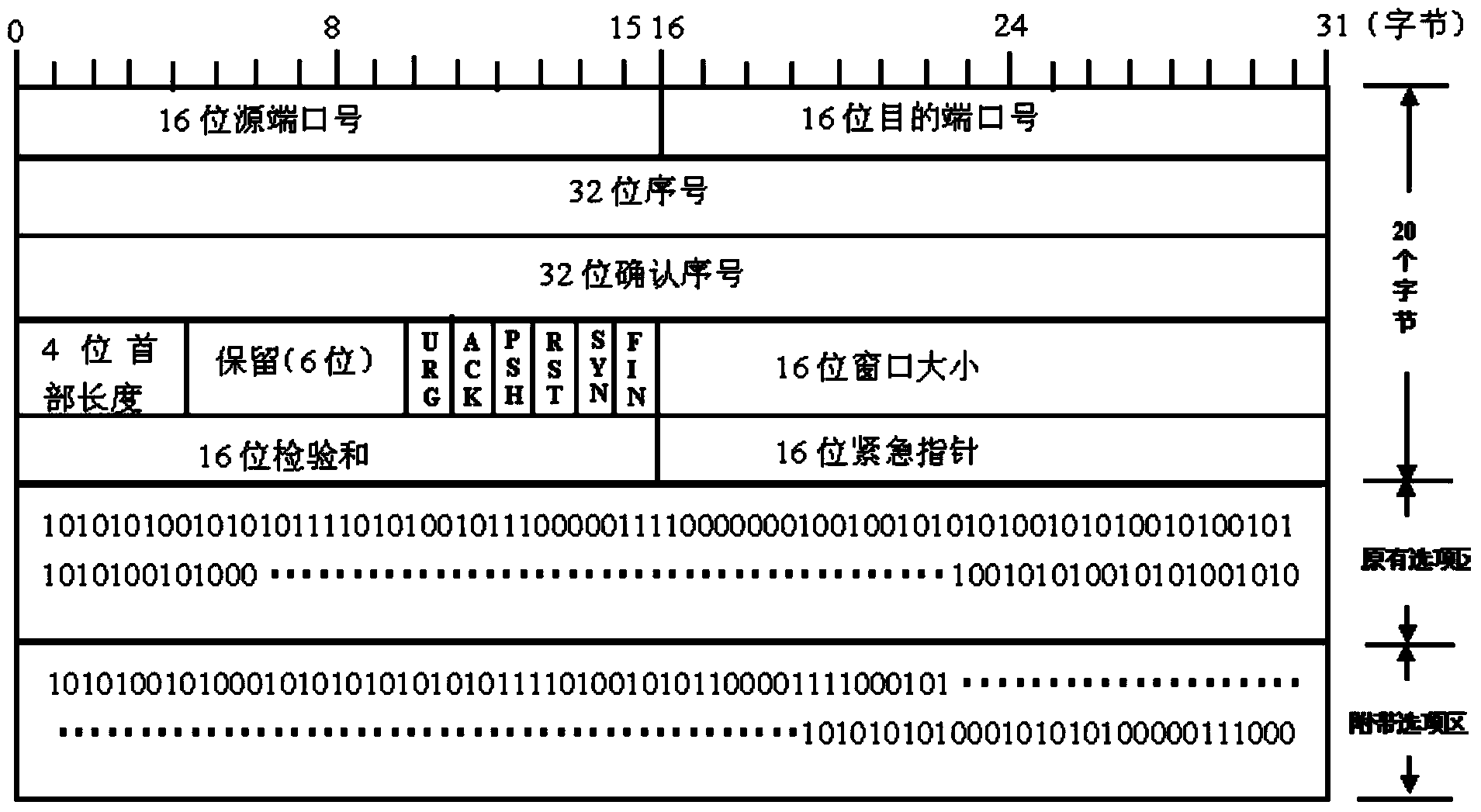
[0026] See Figure 1 to Figure 4 , according to the TCP protocol, the TCP header can have an option area, and its maximum possible space is 40 bytes. In the first step of the handshake between the client and the server, the options that it may use are: MSS maximum message Segment length, Kind=2, 4 bytes. Window Scale window expansion factor, Kind=3, 3 bytes. SACK...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com