A mutual-aid lock system using asymmetric encryption technology and its control method
An asymmetric encryption and control method technology, which is applied in the field of mutual-aid lock system and its control, can solve problems such as difficulty for administrators to allocate safe deposit boxes, waste, and locks that cannot provide reliable security mechanisms.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
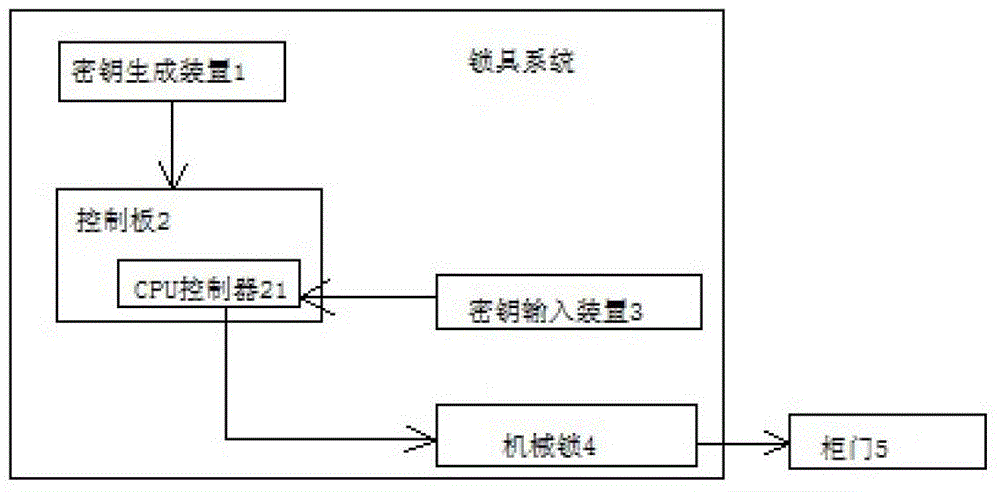
[0070] See figure 1 , figure 2 , image 3 and Figure 4 , this embodiment shows a mutual-aid lock system with single lock and single control, and it is a mode that does not consider privacy:
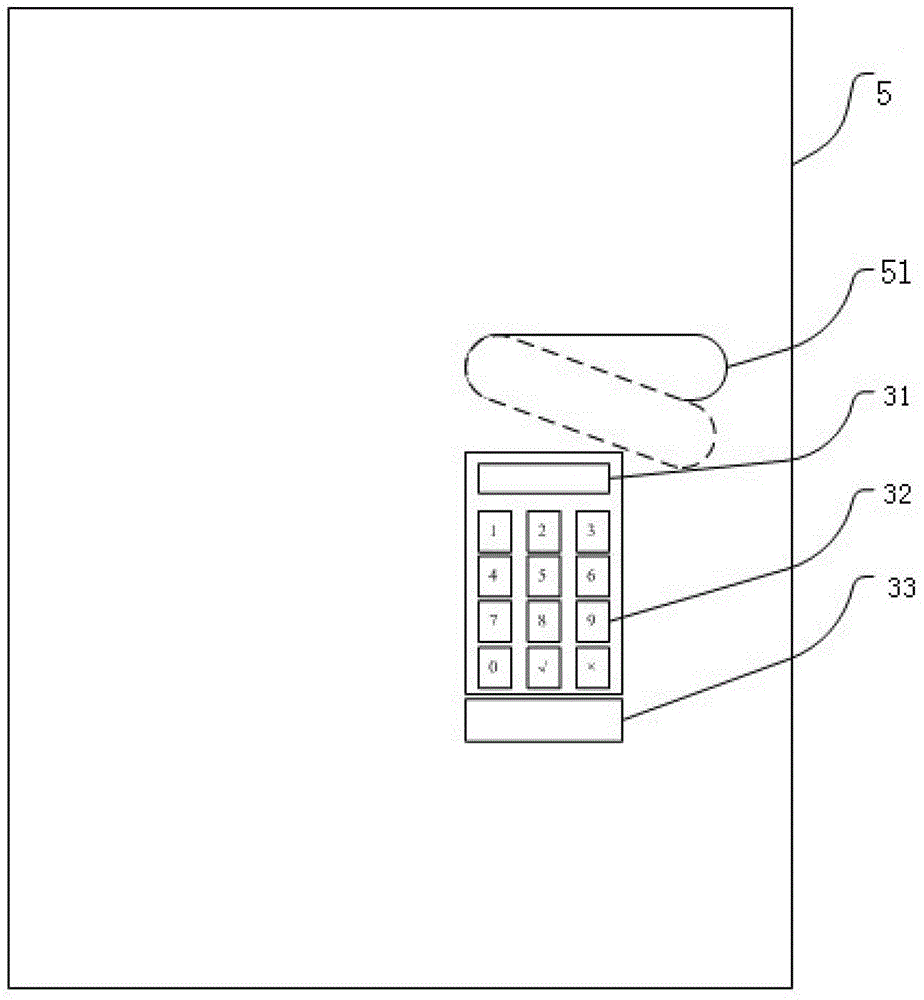
[0071] The lock system includes a key generation device 1, which can be a computer, a control panel 2 arranged on the door 5, a key input device 3, and an electromechanical lock 4 for locking or opening the door 5; the control panel 2 includes a CPU controller 21 and its accessories. Memory; Key generating device 1 generates two keys in pairs, unlocking key and adding lock key; The output end of key input device 3 is connected to CPU controller 21; CPU controller 21 controls electromechanical lock 4 to lock or open door 5; Electromechanical The lock 4 is installed on the door 5 . The present embodiment is a single lock and single control, that is, an electromechanical lock 4 . The door 5 where the electromechanical place 4 is installed is provided with a handle 51; the handle 51 is...
Embodiment 2
[0080] See Figure 5 and Figure 6 , the principle of this embodiment is the same as that of Embodiment 1. What is shown is a system with multiple locks and single control. There is a handle 51; the handle 51 is controlled by the CPU controller 21, and is in different positions when the door 5 is locked or opened; its core process is similar to the single-control single-lock of embodiment 1, but when locked, the recorded data increases the lock number . When unlocking, use the unlock key in turn to try to open those locks that are in the locked state.
[0081] Its control method comprises the following steps:
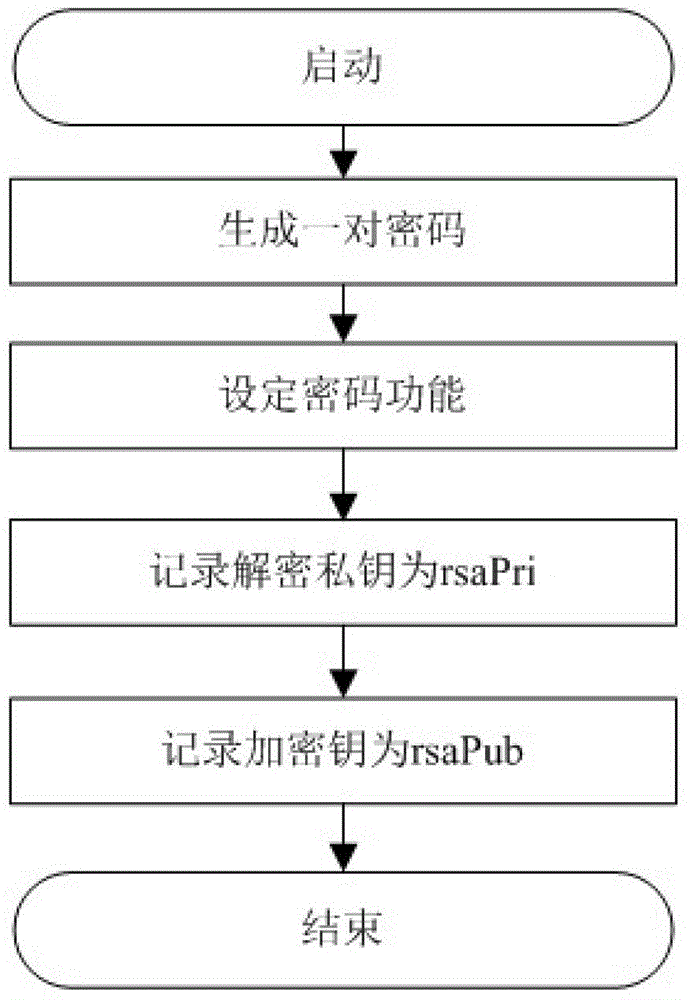
[0082] Step 1: The system generates a key: the key generating device 1 randomly generates one or more pairs of locking keys for locking and unlocking keys for unlocking; Personal express delivery, put the items in two doors, lock the two doors with the same encryption, and the consignee uses the same decryption lock to open the two doors, that is, as long as the enc...
Embodiment 3
[0088] See Figure 7 and Figure 8 , the principle of this embodiment is the same as that of Embodiment 1, and the system shown is a single-lock and single-control system, and it is also a privacy protection mode. The difference is that the door 5 is provided with a handle 51 and a cabinet door reset mechanism (such as a spring), so that the door 5 can be automatically closed without external force; at the same time, the position of the handle 51 is always fixed, so unrelated personnel cannot know the cabinet from the outside. Whether there is something in it; its control method includes the following steps:
[0089] Step 1: the system generates a key: the key generating device 1 randomly generates a paired locking key for locking and an unlocking key for unlocking;
[0090] Step 2: use the key: a, the CPU controller 21 is in the mode of waiting for the input key;
[0091] b. The user inputs and confirms the key through the key input device 3, and the system judges the key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com