A publicly verifiable cloud data possession verification method
A verification method and public verification technology, applied in the field of cloud computing security, can solve problems such as security threats, dishonesty, and data loss, and achieve the effect of low storage complexity and low computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
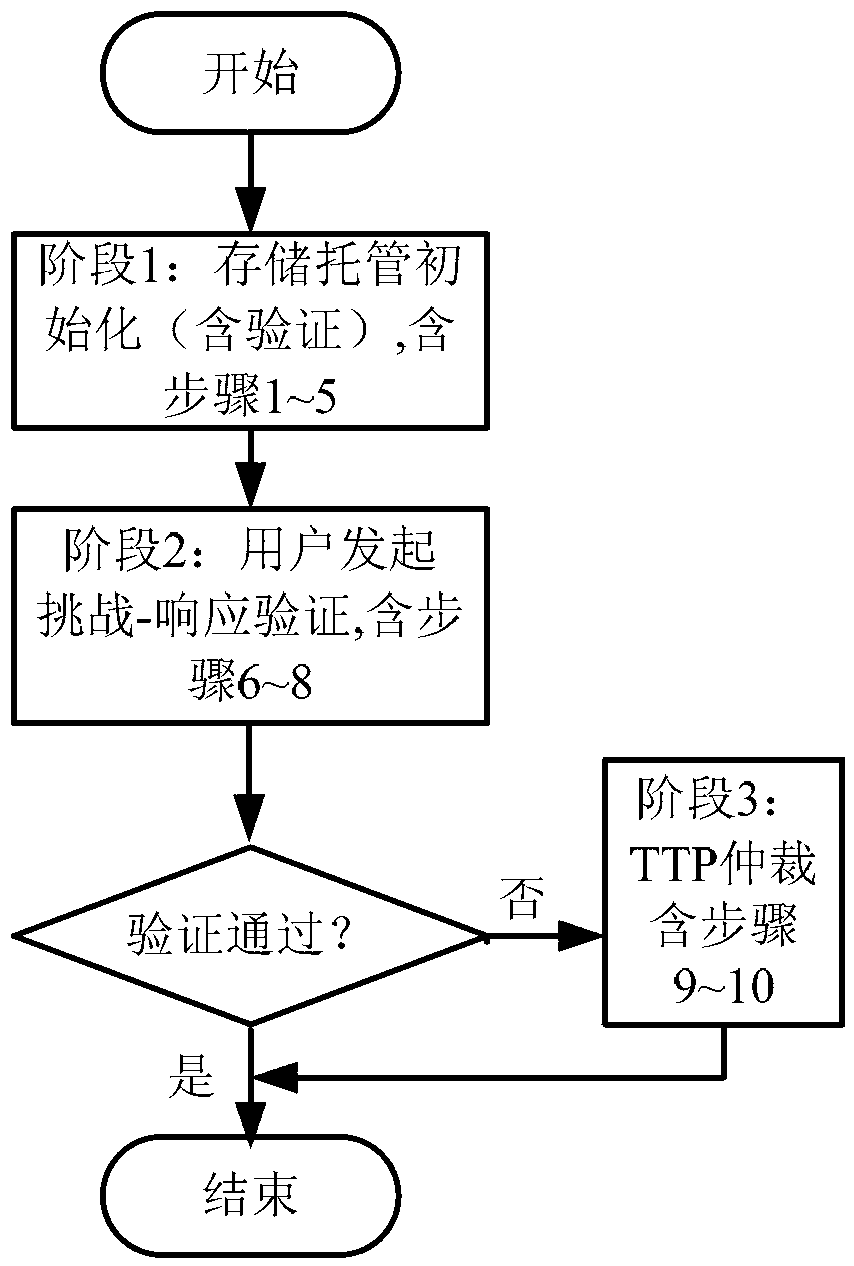
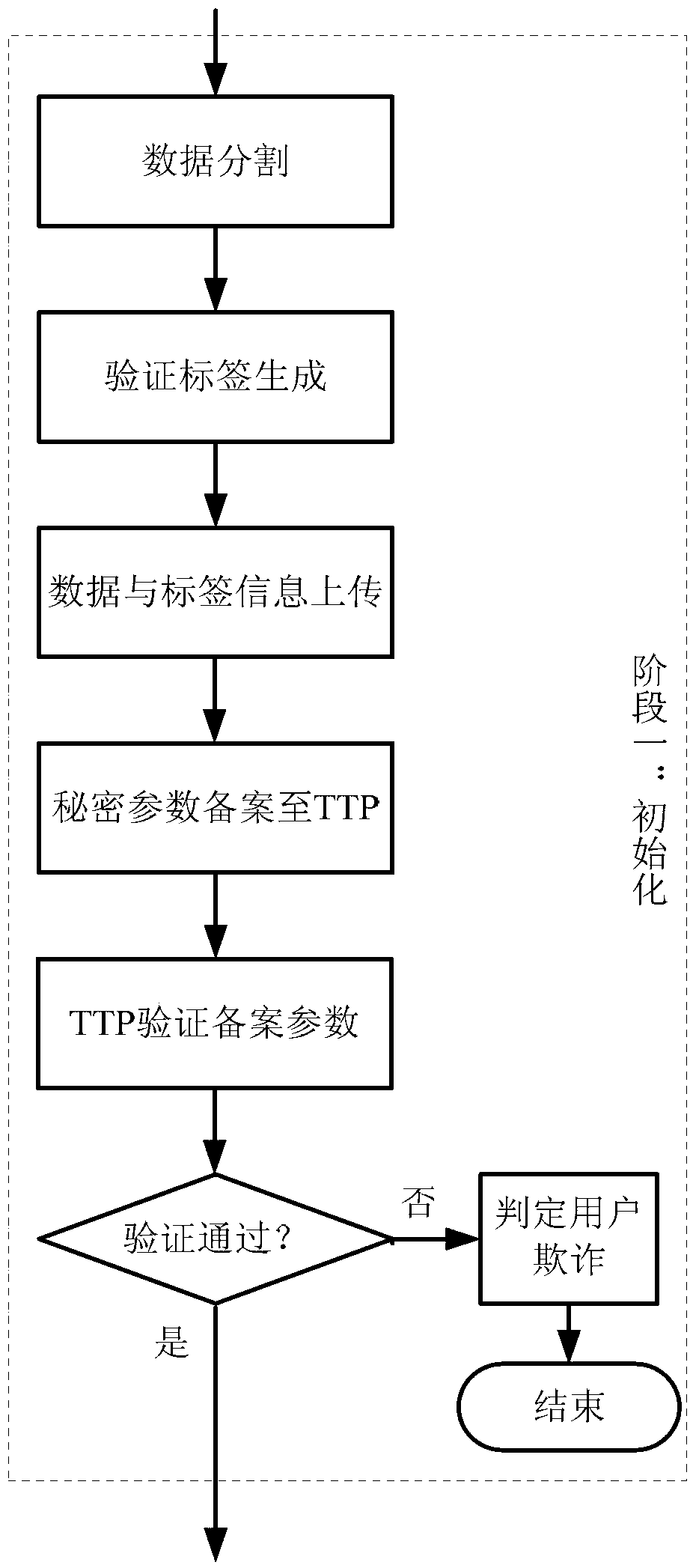
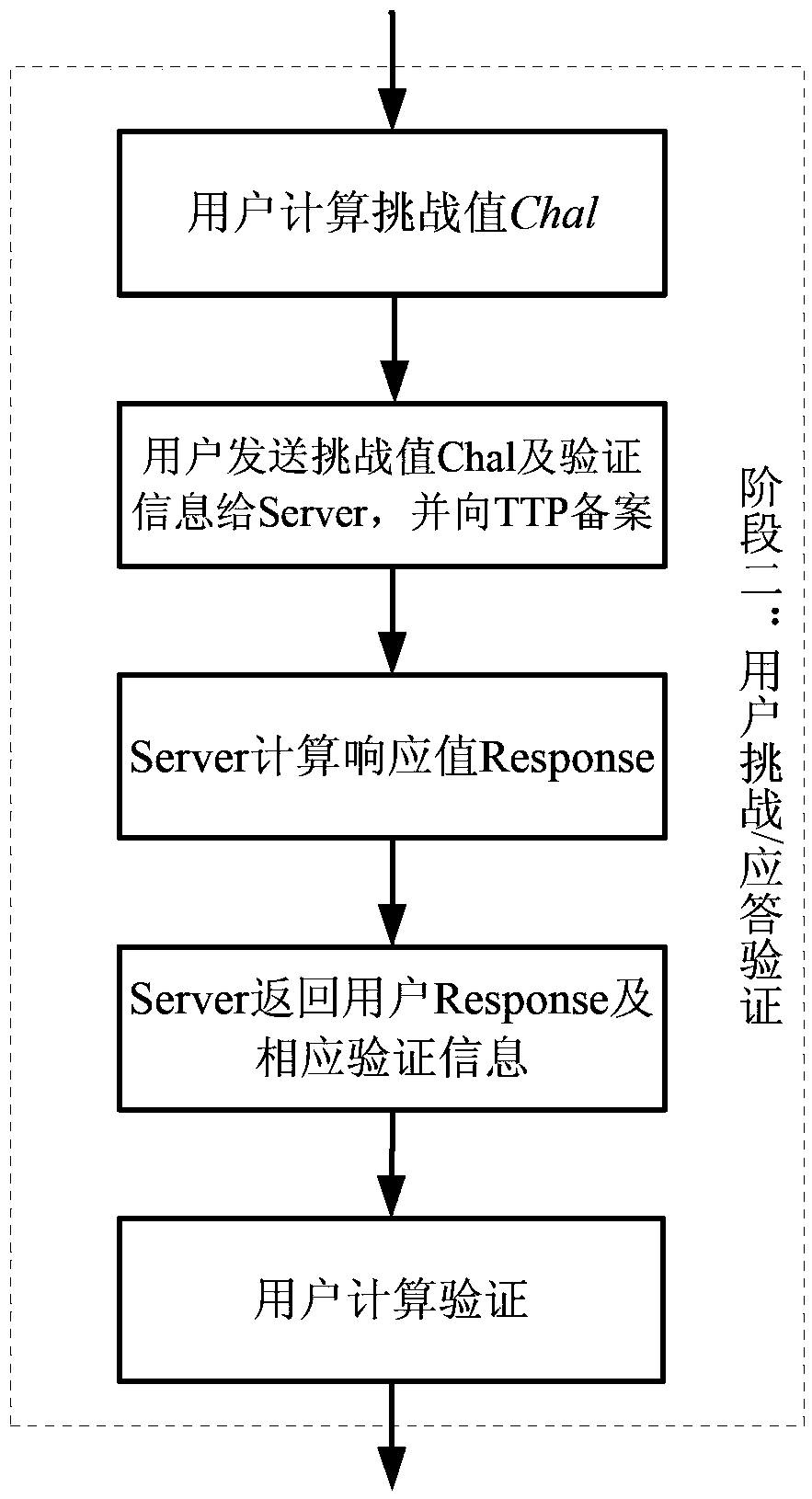
[0055] The described integrity verification method will be described in detail below in conjunction with the accompanying drawings, see Figure 1-8 shown. Figure 5 It is a system block diagram of the present invention; Figure 6 It is the data preprocessing flowchart of the present invention, Figure 7 It is a flow chart of an integrity verification process, Figure 8 For Challenge Information I 1 , evidence information I 2 data structure diagram.
[0056] Main symbols and algorithm explanations:
[0057] (1) represents the original user data, which is divided into n data blocks, f i is the i-th data vector block.
[0058] (2) E() and D() are the encryption algorithm and decryption algorithm of the Paillier cipher algorithm respectively, k 1 is its public key, k 2 is its private key, N is the modulus, and the paillier encryption algorithm satisfies the property of additive homomorphism.
[0059] (3) G is the elliptic curve E P The generator of (a, b), where the lar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com