A Distributed Access Control Method for Cloud Computing
An access control and distributed technology, applied in the field of cloud computing security, can solve problems such as attacks and data leakage, and achieve the effect of reducing the burden and avoiding denial of service attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
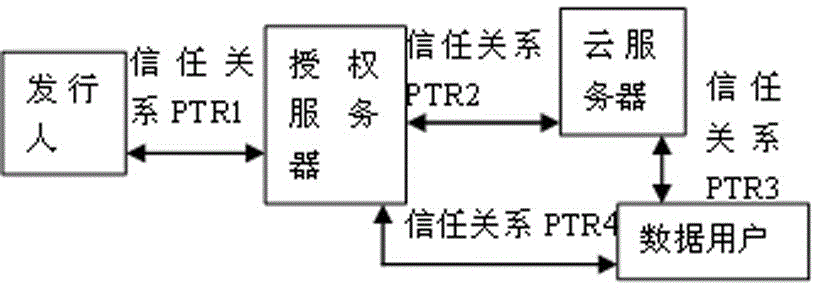
Method used
Image
Examples
Embodiment 1
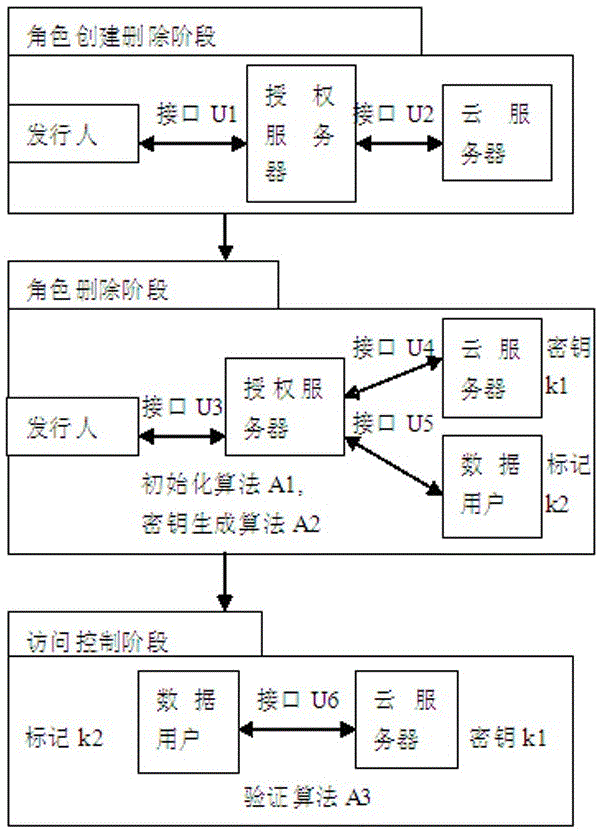
[0054] In this embodiment, the stage of role creation and deletion is completed. The purpose of this phase is to: create and delete files and their associated roles. Including but not limited to the following steps (expressed in a table):
[0055]
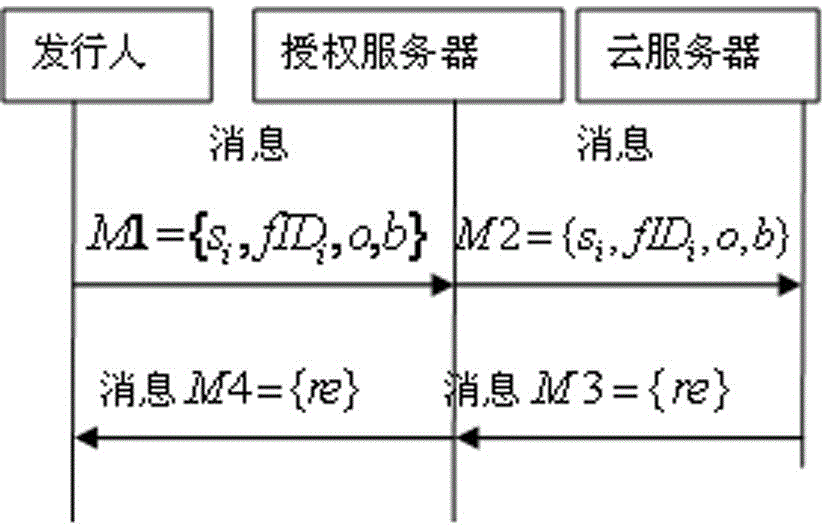
[0056] The role creation and deletion stages are as follows image 3 shown.
[0057] The steps in Embodiment 1 are described as follows:
[0058] (1) Step 100: Issuer (S represents the collection of all issuers) put ,in ( represents the set of all filenames) is the filename, is the operation type (note that means a file creation operation, file delete operation) to the authorization server AS, and is a 3-bit integer that represents the allowed roles of the file. The definitions are shown in the table below.
[0059]
[0060] (2) Step 102: When receiving , the authorization server AS passes it to the cloud server CS.
[0061] (3) Step 104: When receiving When, the cloud server CS according to the oper...
Embodiment 2
[0064] This embodiment defines the role assignment phase. The purpose of this stage is to realize the assignment of roles to data users. Including but not limited to the following steps (expressed in a table):
[0065]
[0066] The role assignment stages are as follows Figure 4 shown.
[0067] The steps and flow chart in embodiment two are described as follows:
[0068] (1) Step 108: Authorization server AS creates a elliptic curve , then create your own private key (in denotes the residual class ring modulo n), and the corresponding public key . After the creation is successful, the authorization server AS passes the and elliptic curves The parameters of the parameter are sent to the cloud server CS to realize the initialization of the cloud server CS, and then the cloud server CS returns a success value to the authorization server AS.
[0069] (2) Step 110: When the issuer In order to access the file and wish to assign a character When allocating ...
Embodiment 3
[0073] This embodiment defines the access control phase. The purpose of this stage is: to realize the access control to the files on the cloud server CS. Including but not limited to the following steps (expressed in a table):
[0074]
[0075] The stage flow of this embodiment is as follows Figure 5 shown.
[0076] The steps of the stage flow chart in embodiment three are described as follows:
[0077] (1) Step 116: Be a data user want to access the file When , it will form the corresponding notation of the important characteristic parameters Send to the cloud server CS.
[0078] (2) Step 118: The cloud server CS receives the token The pairing function is used for verification to ensure that the role of the data user DU is assigned by the authorization server AS, and then the cloud server CS sends a challenge value to the data user DU.
[0079] (3) Step 120: When the data user DU receives the challenge value, use the hash function to calculate a signature , ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com