Method for estimating the scale of malicious code infected hosts based on dns cache detection
A malicious code and host technology, applied in the field of network communication security, can solve problems affecting data integrity, security risks, privacy protection, etc., and achieve the effect of easy deployment and implementation, and strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings.
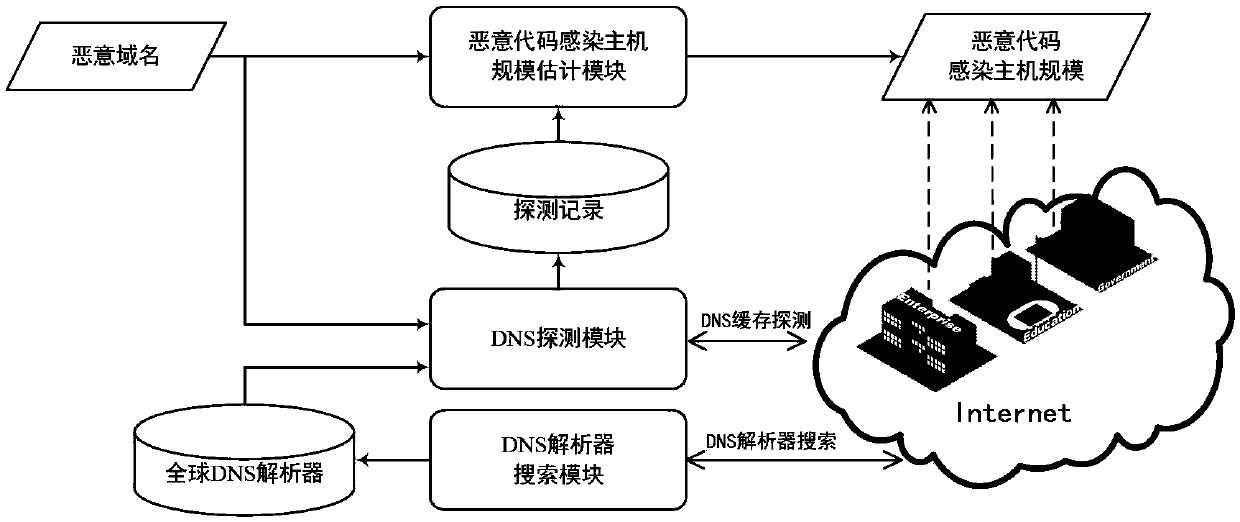
[0015] see figure 1 As shown, the system architecture for estimating the scale of malicious code-infected hosts in specific regions based on DNS cache detection (such as geographic regions, countries, provinces, cities, etc.) mainly includes a DNS resolver search module, a DNS detection module, and a malicious code-infected host scale estimation module.
[0016] In the following, the principles and processes of each module are introduced in detail.
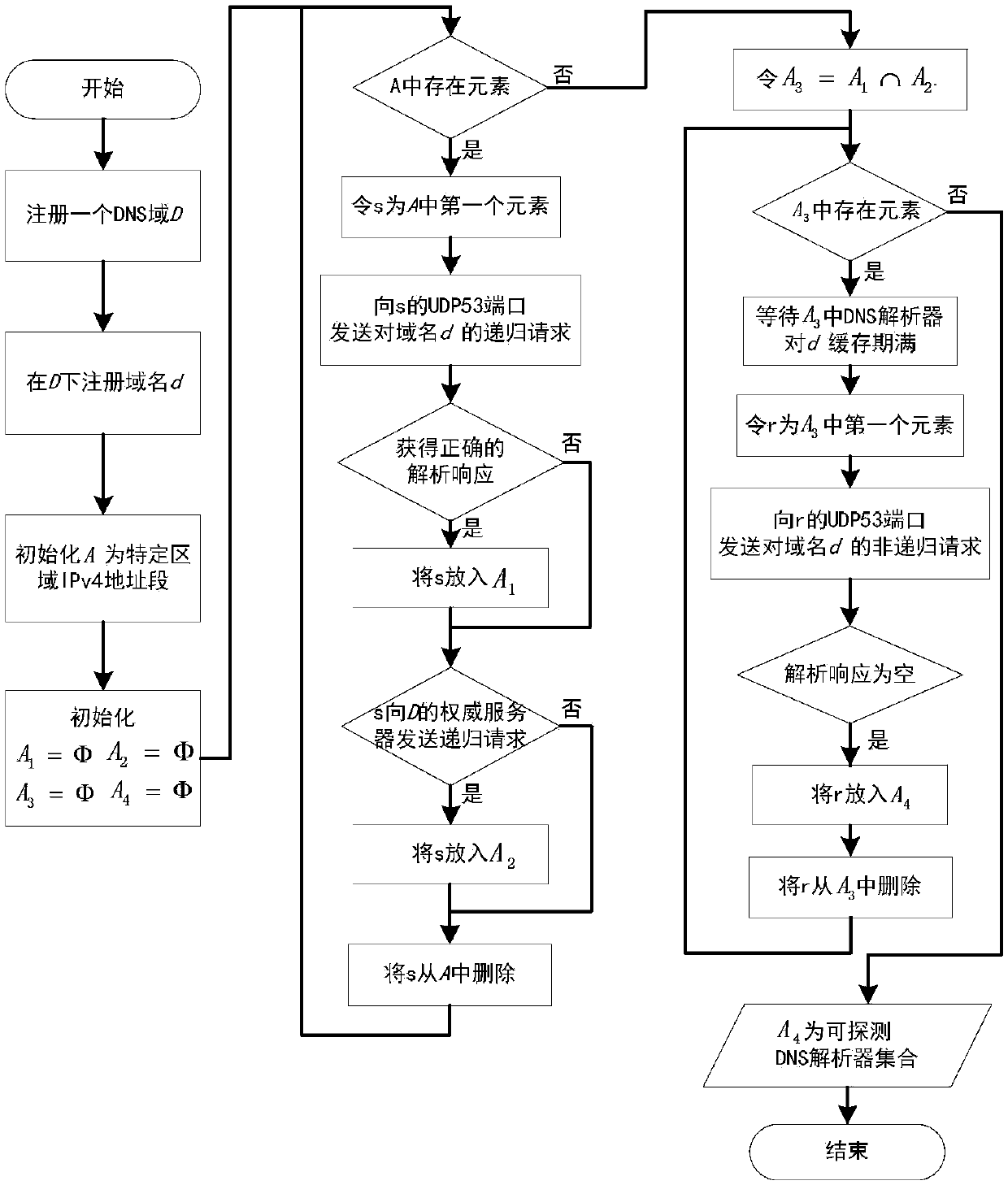
[0017] Such as figure 2 As shown, the DNS resolver search module uses the following steps to search for a DNS resolver that can be used as a probe within a specific area.
[0018] (1) Register a DNS domain, and register the domain name d under the DNS domain. Domain name d is not
[0019] Public domain name, that is, existing web applications cannot request this domain name.
[0020] (2) S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com