Method and device for upgrading secret key
A key update and key technology, applied in the field of communication network security, can solve the problems of relying on certificates, untimely key revocation, and heavy workload of certificate maintenance and management, and achieve the effect of enhancing security and improving convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
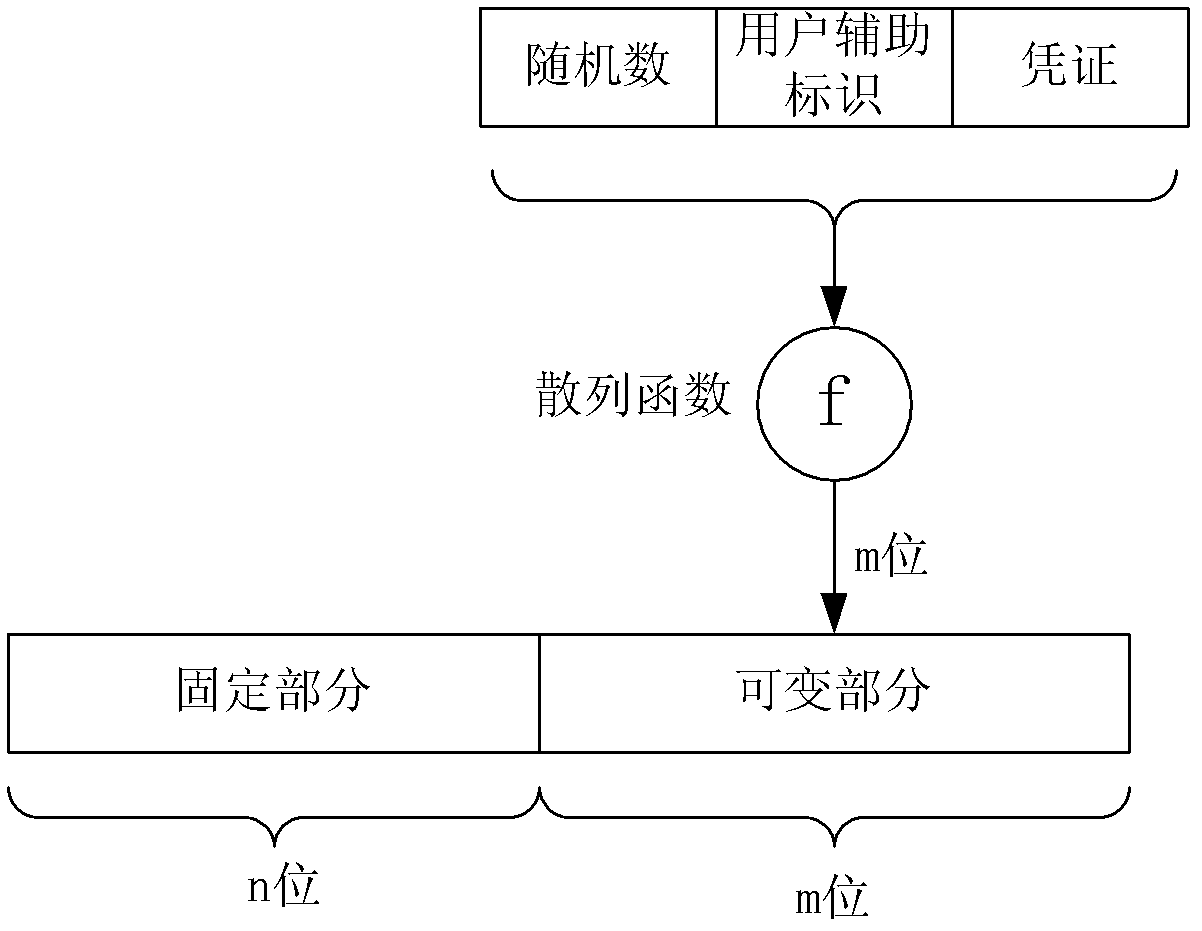
[0057] In this embodiment, the user ID is defined as a fixed part and a variable part, and the revocation of the key is completed by changing the variable part of the user ID. The variable part is calculated by hashing the intermediate parameters and intercepted from the result of the hash operation according to the length of the variable part. The variable part can also be a random value intercepted according to the length of the variable part, or for The random value is hashed, and is intercepted from the result of the hash according to the length of the variable part.
[0058] Intermediate parameters include: random value, user auxiliary ID, and credentials.
[0059] The hash operation refers to calculation by using a hash function, for example, a message digest MD5 (Message Digest) or a secure hash algorithm (Secure Hash Algorithm, SHA-1).
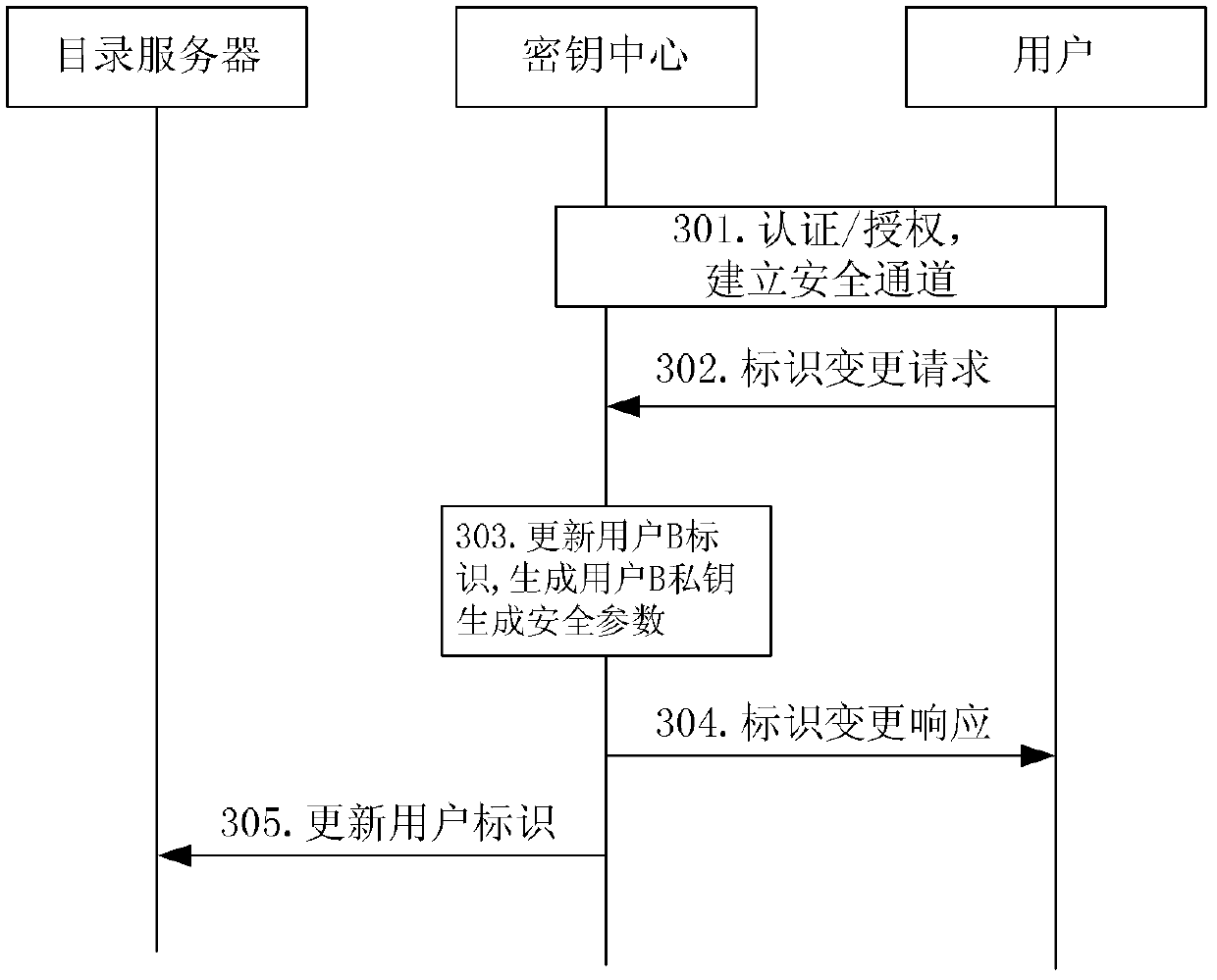
[0060] After the user's key is revoked, the following mechanism is used to notify other users of the key revocation result.
[0061...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com