APT (advanced persistent threat) detection method and system
An advanced persistent threat and detection method technology, applied in the transmission system, digital transmission system, electrical components, etc., can solve the problems of missed detection, unmatched data, difficult detection of bypass monitoring, etc., to achieve good performance and accuracy, The effect of improving the detection ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
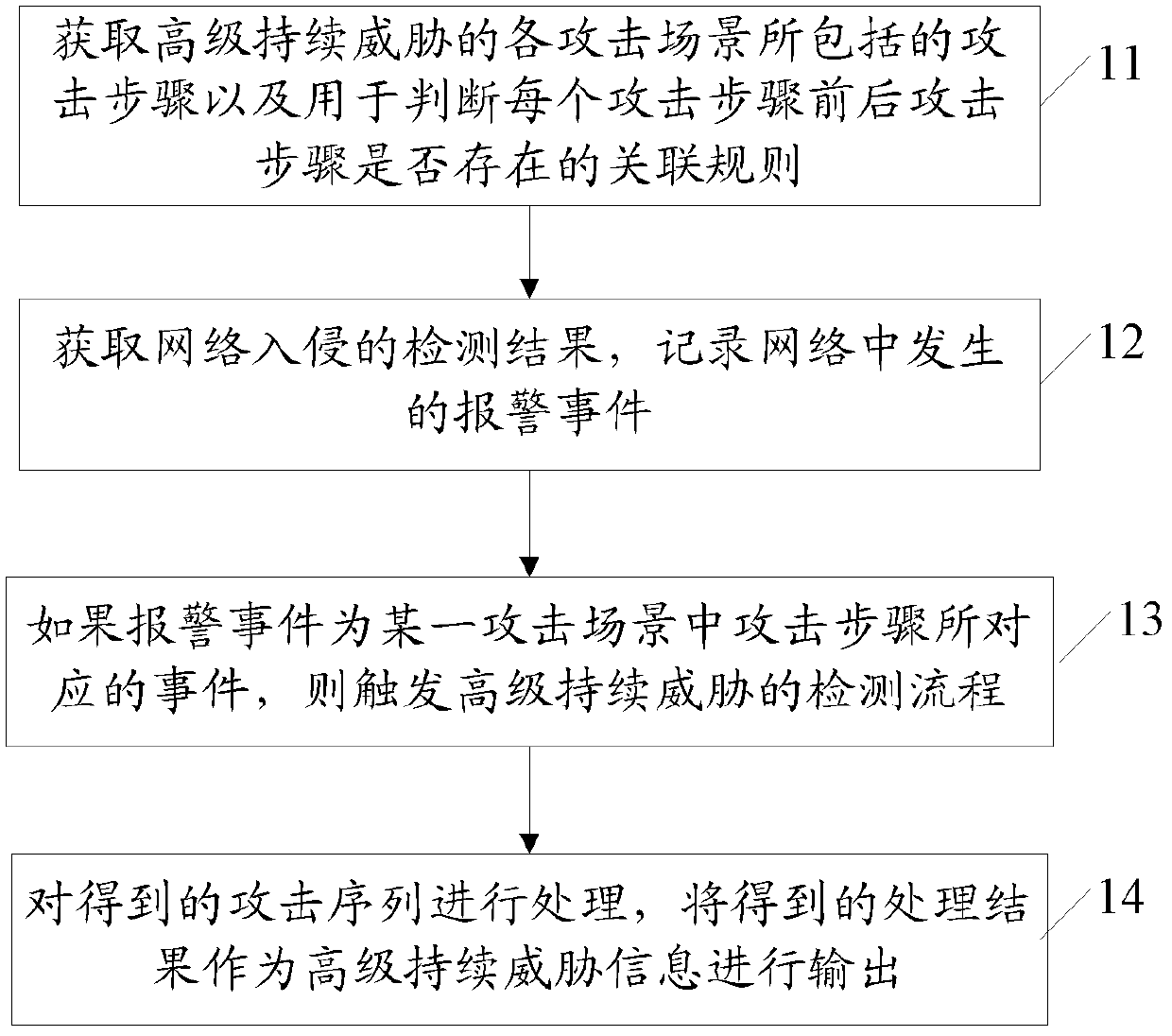
[0063] Step 101: Obtain the attack steps of each attack scenario set by the user and the association rules for judging whether the attack steps before and after each attack step exist, wherein each attack step corresponds to a plurality of different events for realizing the attack step.
[0064] Step 102, perform intrusion detection in real time, and acquire alarm events occurring in the network.
[0065] Step 103, if the alarm event is an event corresponding to an attack step in a certain attack scenario, trigger the APT attack state detection process, specifically including:
[0066] If the alarm event is an event corresponding to the initial attack step in the attack scenario, the event in the current network is directly saved as a new attack sequence corresponding to the attack scenario;
[0067] If the alarm event is not the event corresponding to the initial attack step, it is judged whether there is a relationship between the alarm event in the saved attack sequence and...
Embodiment 2
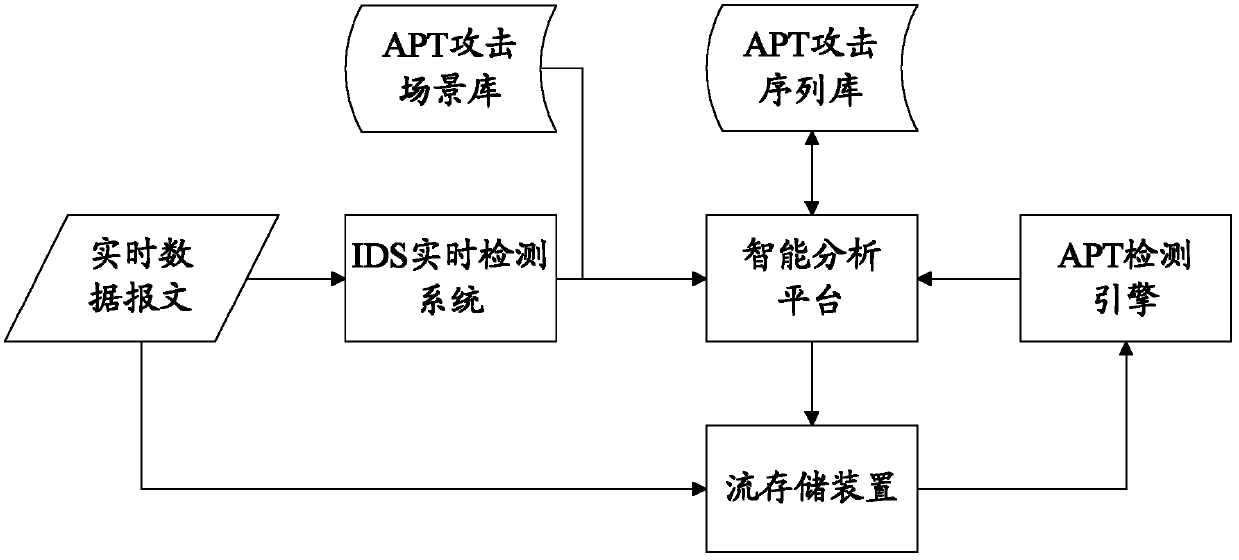
[0071] Different from Embodiment 1, the initial state of the alarm event is not a certain ATP attack pattern sequence, and it cannot be accurately related to the next state of a certain ATP attack sequence in the stored APT attack sequence library, then perform the following operations:
[0072] The ATP detection engine loads the latest and most comprehensive attack signatures and analysis strategies to perform in-depth data detection on historical data. Specifically:
[0073] Step 201. When any two attack steps are associated with the same attack step, merge the arbitrary two attack steps into an associated relationship;
[0074] In the following, uppercase letters represent the attack steps, and lowercase letters represent the events corresponding to the attack steps. For example, attack step A, the event corresponding to the attack step is a.
[0075] For merging between attack steps, for example:
[0076] When attack step A is associated with attack step B, and attack st...
Embodiment 3
[0087]If adopting the method for embodiment two to process this attack sequence is related to the existing attack sequence, then increase a new attack sequence entry in the ATP attack sequence storehouse;
[0088] If the generated new attack sequence is unique (that is, the attack pattern in the output result is unique), such as (A+B+C+D+E: "a+b+*+d+e"). At this time, there is a related attack sequence (A+B+C+D+E: "a+b") in the stored ATP attack sequence library, and the stored attack sequence is replaced with a new attack sequence.
[0089] If there is a relevant attack sequence in the ATP attack sequence library stored at this time, such as (A+B+C+D+E: "a+b+*+*+e"; A+B+X+D+E: "a +b+*+*+e"); then update the stored attack sequence to (A+B+C+D+E: "a+b+*+d+e") and delete the unmatched attack pattern (A+B +X+D+E: "a+b+*+*+e").
[0090] If the generated attack sequence is (A+B+C+D+E: "*+*+c+d+e"), there are related attack sequences in the currently stored ATP attack sequence dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com