Document encryption and decryption method, device and system
A technology for encrypting keys and documents, applied in the field of information security, can solve the problems of low security performance and achieve high security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
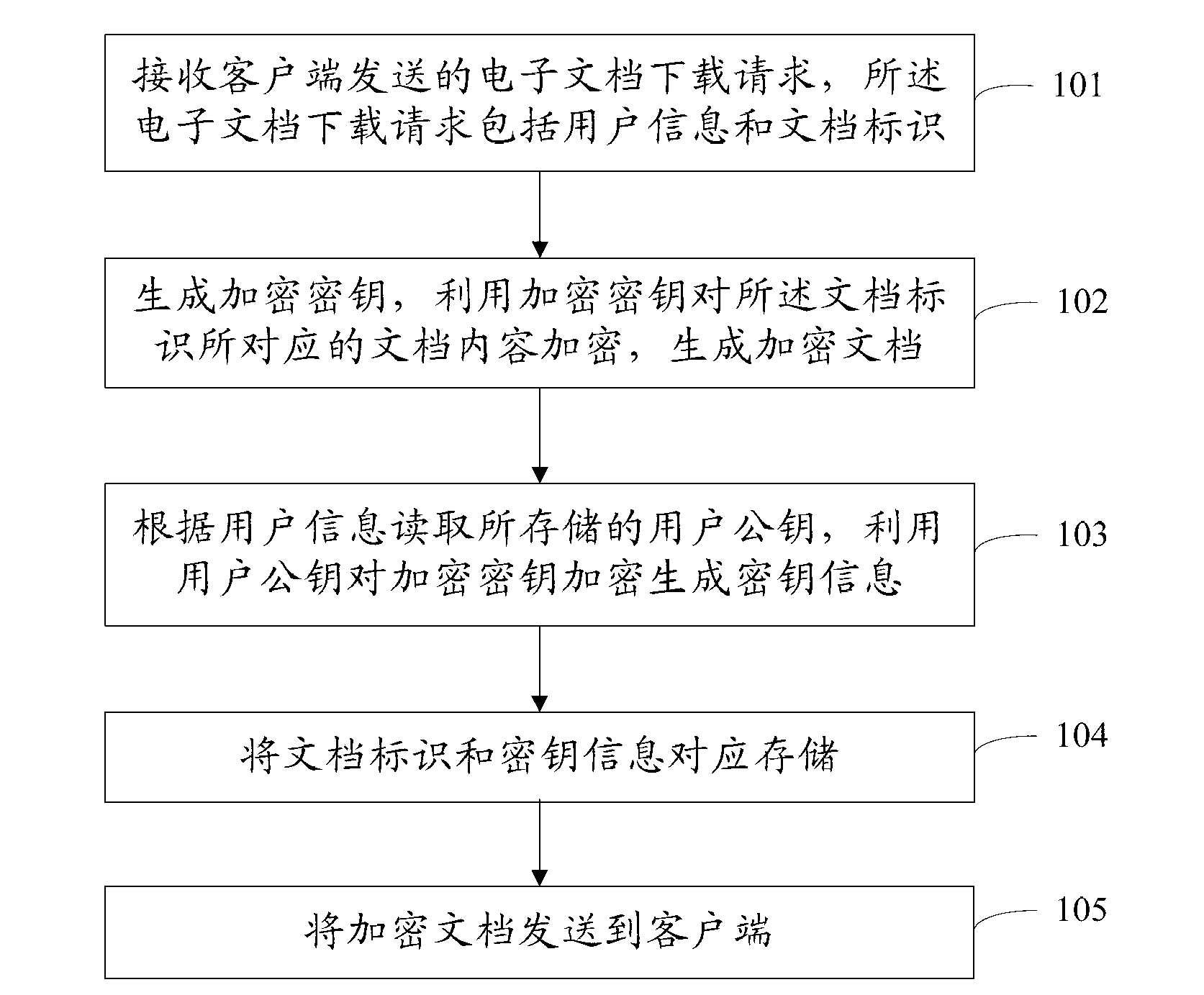
[0079] figure 1 It is a schematic flow chart of Embodiment 1 of a document encryption method of the present invention, including:
[0080] Step 101: Receive an electronic document download request sent by a client, where the electronic document download request includes user information and a document identifier.
[0081] When the user needs to read the electronic document, the client sends an electronic document download request to the server. The user information includes the user's login name and login password. The document identifier can be any one or more of document label, document name and document type. Electronic documents can be PDF documents, WORD documents and TEXT documents, etc.
[0082] Step 102: Generate an encryption key, use the encryption key to encrypt the content of the document corresponding to the document identifier, and generate an encrypted document.
[0083] The encryption key is an encryption key randomly generated when the server receives an e...
Embodiment 2
[0093] figure 2 It is a flow chart of Embodiment 2 of a document encryption method of the present invention. Compared with Embodiment 1, Embodiment 2 also includes registration and authentication, specifically including:
[0094] Step 201: Receive a user registration request sent by a client, where the user registration request includes user information.
[0095] The user can send a user registration request to the server through the client according to actual needs.
[0096] Step 202: Authenticate the user information, and randomly distribute the user public key and the user private key when the authentication is passed.
[0097] The server performs authentication, which may be performed according to user information such as user login name and login password. When the user has registration authority, use PKI technology to assign a set of user public key and user private key to the user.
[0098] Step 203: store the user information and the user public key correspondingly...
Embodiment 3
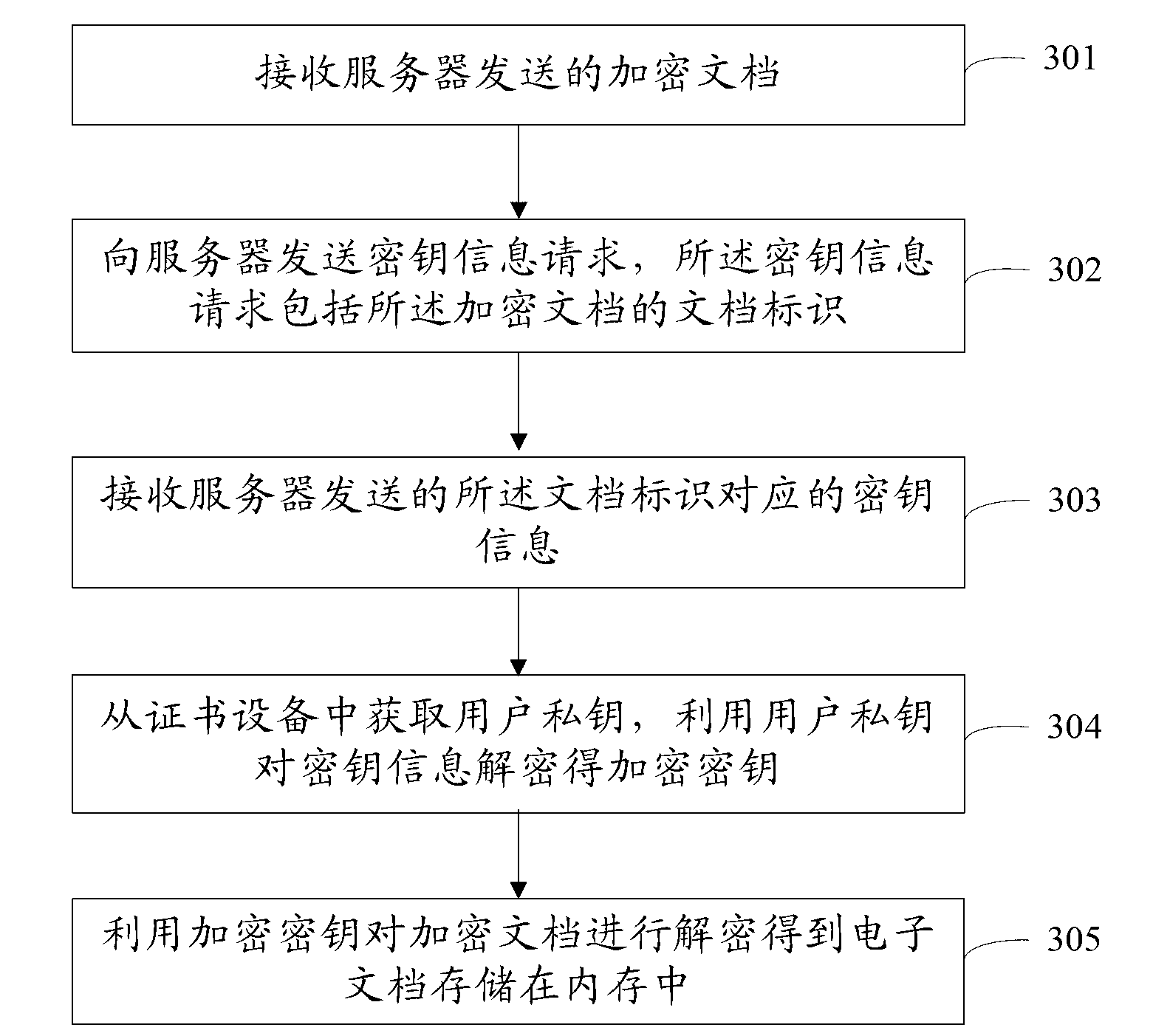
[0114] image 3 It is a schematic flow chart of Embodiment 3 of a document decryption method of the present invention, including:
[0115] Step 301: Receive the encrypted document sent by the server.
[0116] Step 302: Send a key information request to the server, where the key information request includes the document identifier of the encrypted document.
[0117] After receiving the encrypted document, the client sends a request to the server for obtaining key information of the encrypted document. The server stores the document identification of the electronic document and its corresponding key information.
[0118] Step 303: Receive the key information corresponding to the document identifier sent by the server.
[0119] The server searches for the key information corresponding to the document identifier according to the document identifier and sends it to the client.
[0120] Step 304: Obtain the user's private key from the certificate device, and use the user's priva...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com