System and method for fingerprint encryption and decryption
An encryption, decryption, and fingerprint technology, applied in the field of communication security, can solve the problems of all-round protection of all information without proposing a more humanized solution, so as to achieve the effect of enhancing security and ensuring communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
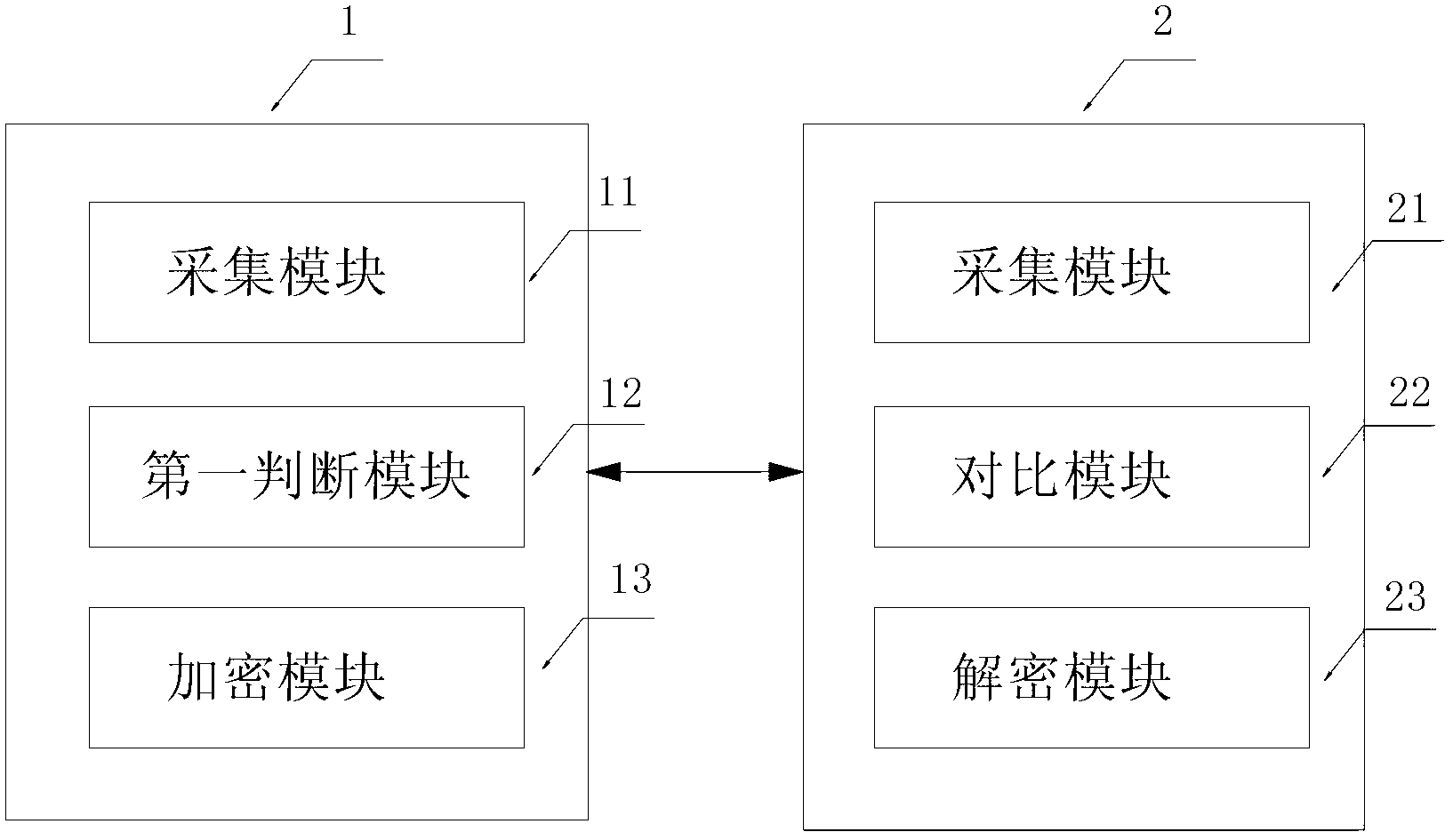
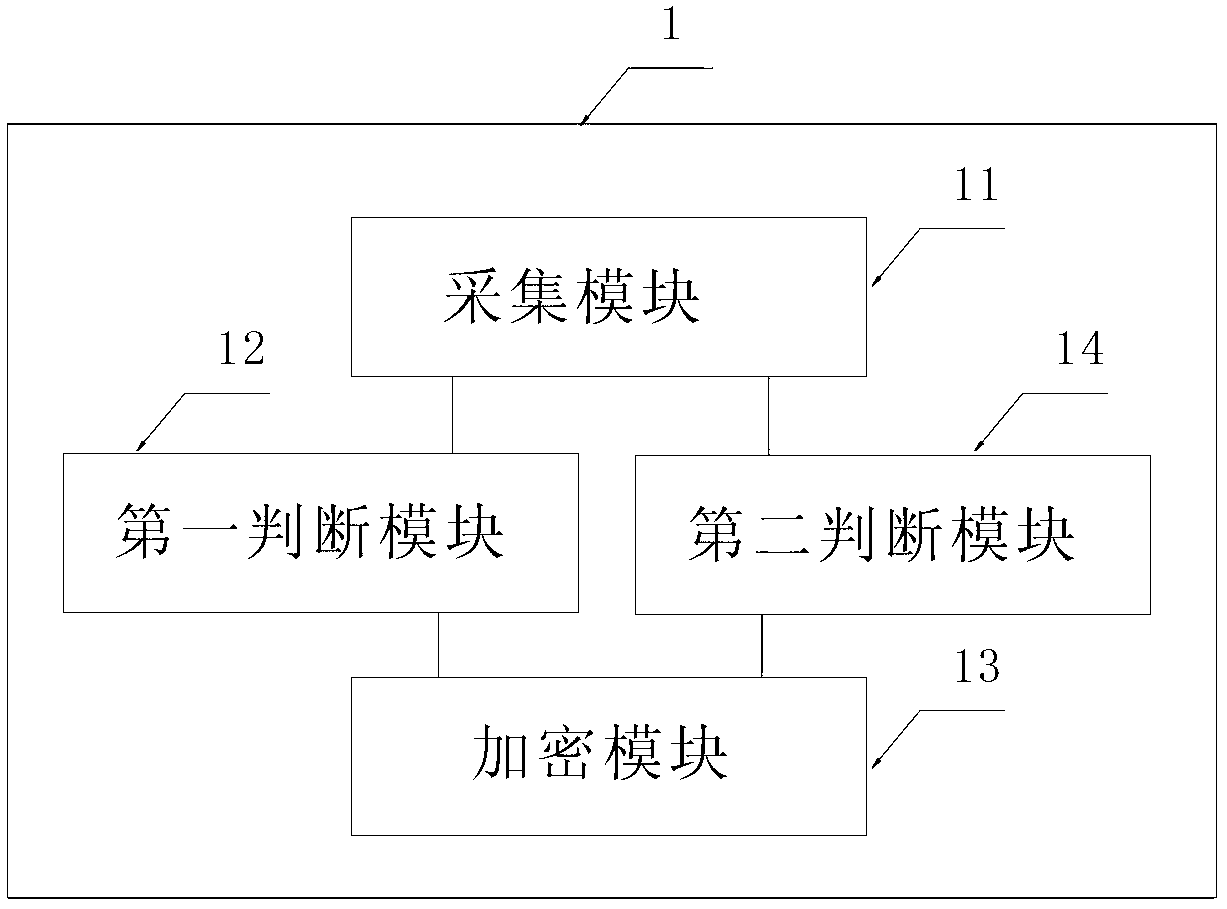
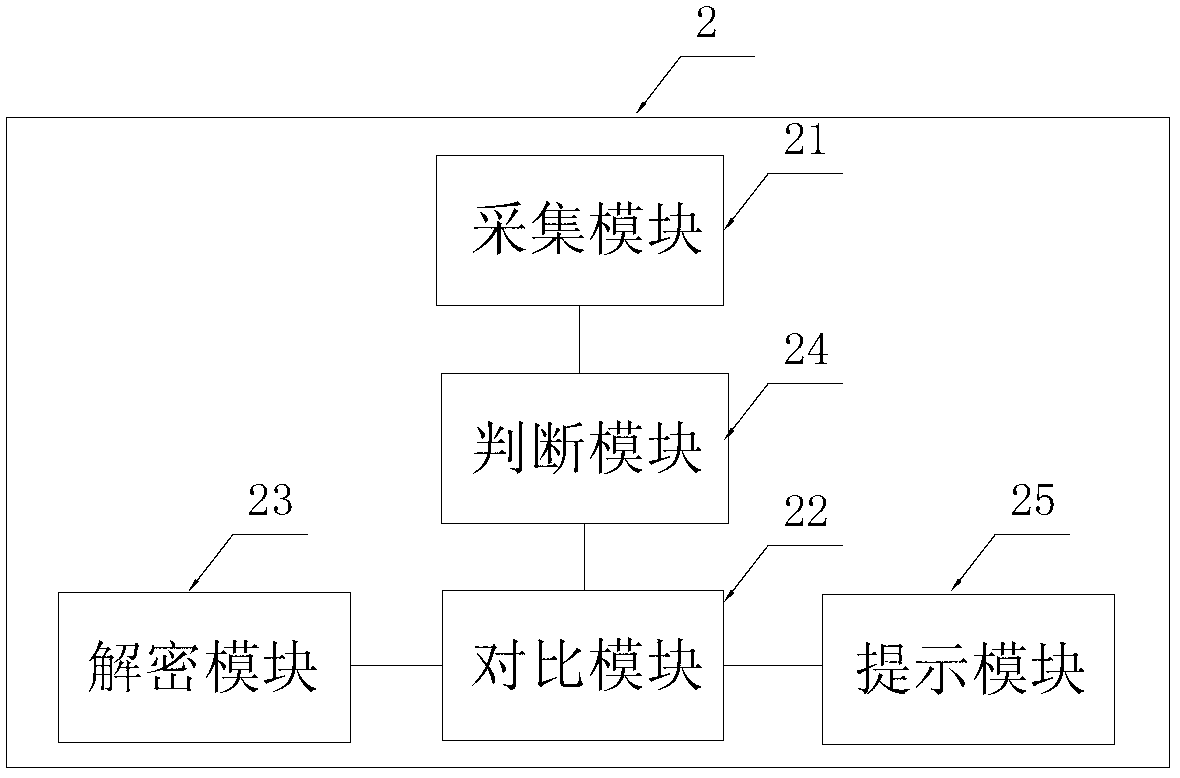
[0045] see figure 1 , which is the fingerprint encryption and decryption system described in this embodiment. It includes a first mobile phone 1 and a second mobile phone 2 with a fingerprint identification device. The first mobile phone 1 is used as a sending terminal, and the second mobile phone 2 is used as a receiving terminal. In this embodiment, a mobile phone with a fingerprint reader is taken as an example. The first mobile phone 1 for sending messages, files or folders includes a collection module 11 , a first judgment module 12 and an encryption module 13 . The fingerprint reader of the first mobile phone 1 is actually a collection module 11 for collecting user fingerprints. The collected fingerprints are stored in the first mobile phone 1 . Through some software programs that can utilize bluetooth and wifi to transmit messages or functional modules integrated in the mobile phone, together with the mobile phone with the fingerprint reader, the system of the presen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com