Authentication method and authentication system for page visiting
An authentication method and page technology, applied in the field of communication, can solve the problems of high cost, shortening the validity of tokens, and the system has no time to handle other affairs, and achieve the effect of enhancing page security authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
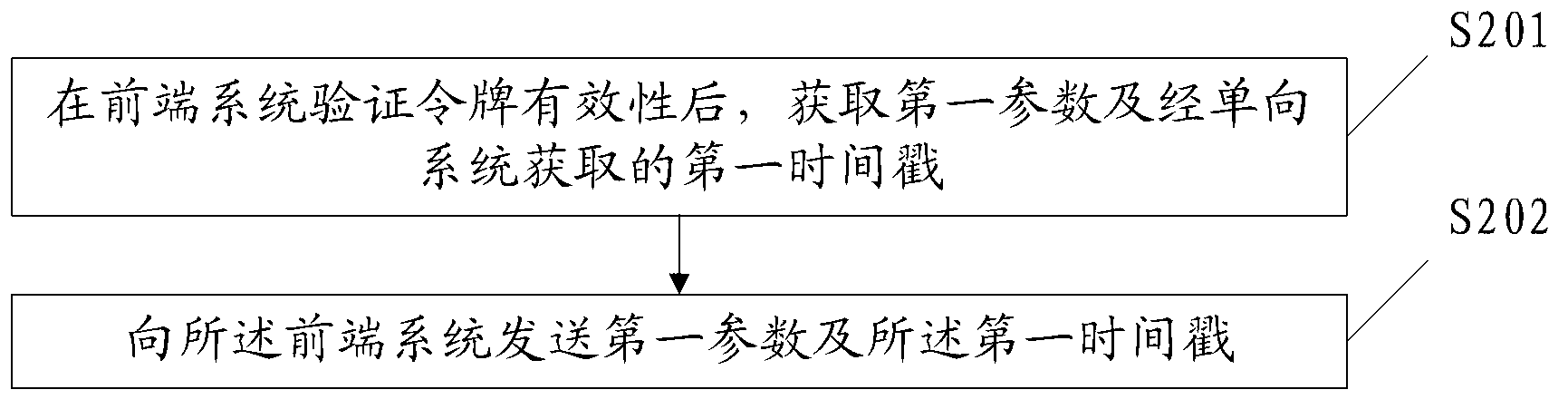
[0062] like figure 1 As shown, the first embodiment of the page authentication method provided by the present invention, the method includes:
[0063] Step S101: After verifying the validity of the token, receive the first parameter sent by the top box and the first time stamp obtained through the one-way system, the one-way system is a clock system shared by the authorized set-top box and the front-end system;
[0064] The storage unit of the front-end system contains the validity information of the set-top box token. When the set-top box sends a request for accessing the home page interface, it sends the token to the front-end control system. The front-end system checks in its own storage unit according to the token sent by the set-top box. Whether it contains the token information, if it contains the token information, and the token information is within the valid time limit, it means that the token is valid.
[0065] The first parameter sent by the receiver top box, said ...
no. 2 example
[0082] like image 3 As shown, it is the second embodiment of the page authentication method provided by the present invention, the method includes:
[0083] Step S301: After verifying the validity of the token, the first encrypted user password and the first time stamp obtained through the one-way system sent by the receiver set-top box are the authorized set-top box and the front-end system Shared clock system;
[0084] After verifying the validity of the token, the set-top box sends the encrypted first user password and the first time stamp obtained in the one-way system to the front-end system through the transmission network.
[0085] Step S302: when the preset condition is met, obtain the current second time stamp via the one-way system;
[0086] The preset conditions include:
[0087] there is no timestamp in the storage unit consistent with said first timestamp; or
[0088] empty condition.
[0089] When the preset condition is an empty condition, the front-end sy...
no. 3 example
[0102] Such as Figure 5 As shown, it is a third embodiment of a page verification method of the present invention, including:
[0103] Step S501: After verifying the validity of the token, receive the first encrypted first data sent by the set-top box, the start-up time of the set-top box, and the first time stamp obtained through the one-way system, the one-way system is A clock system shared by the authorized set-top box and the front-end system;
[0104] After verifying the validity of the token, the set-top box sends the encrypted first data to the front-end system through the transmission network. The first data includes the first user password, the start-up time of the set-top box and the first time stamp, and The first timestamp obtained in .
[0105] Step S502: when the preset condition is met, obtain the current second time stamp via the one-way system;
[0106] The preset conditions include:
[0107] there is no timestamp in the storage unit consistent with said...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com