Trojan horse detection method based on Trojan horse virus type classification modeling
A detection method and Trojan horse technology, applied in electrical components, transmission systems, etc., can solve problems such as the failure of Trojan horse detection technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment example
[0025] Implementation case: Trojan horse inspection
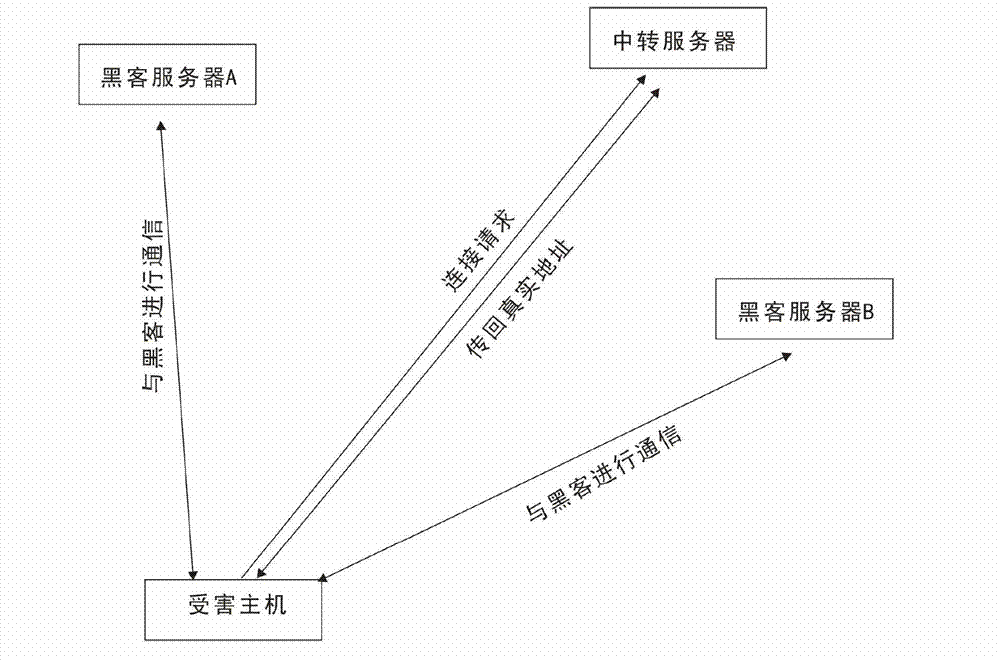
[0026] Trojan A is a Trojan with a good anti-kill effect. Use the method of driving encrypted communication to perform a rebound connection with the external host using the transit server B. Therefore, when the machine is infected with such a Trojan horse, the Trojan horse can escape the detection of mainstream antivirus software and Trojan horse inspection tools based on signatures because of the anti-virus protection. Because the Trojan horse uses the drive encryption method during the communication process, it means that no matter whether it is the local collection of data packets or the network IDS (Intrusion Detection System), it is impossible to parse out those data packets that are the data packets sent and received by the Trojan horse, that is, It is impossible to determine which machines the Trojan horse interacts with.
[0027] The working flow chart of Trojan A is roughly as follows figure 2 Shown: In this pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com