Security data transmission method based on compressive sensing theory
A technology of secure data and compressed sensing, applied in the field of secure data transmission, can solve problems that have not been applied to ensure the security of data transmission, reduce the number of data transmission, etc., and achieve the effect of perfecting confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
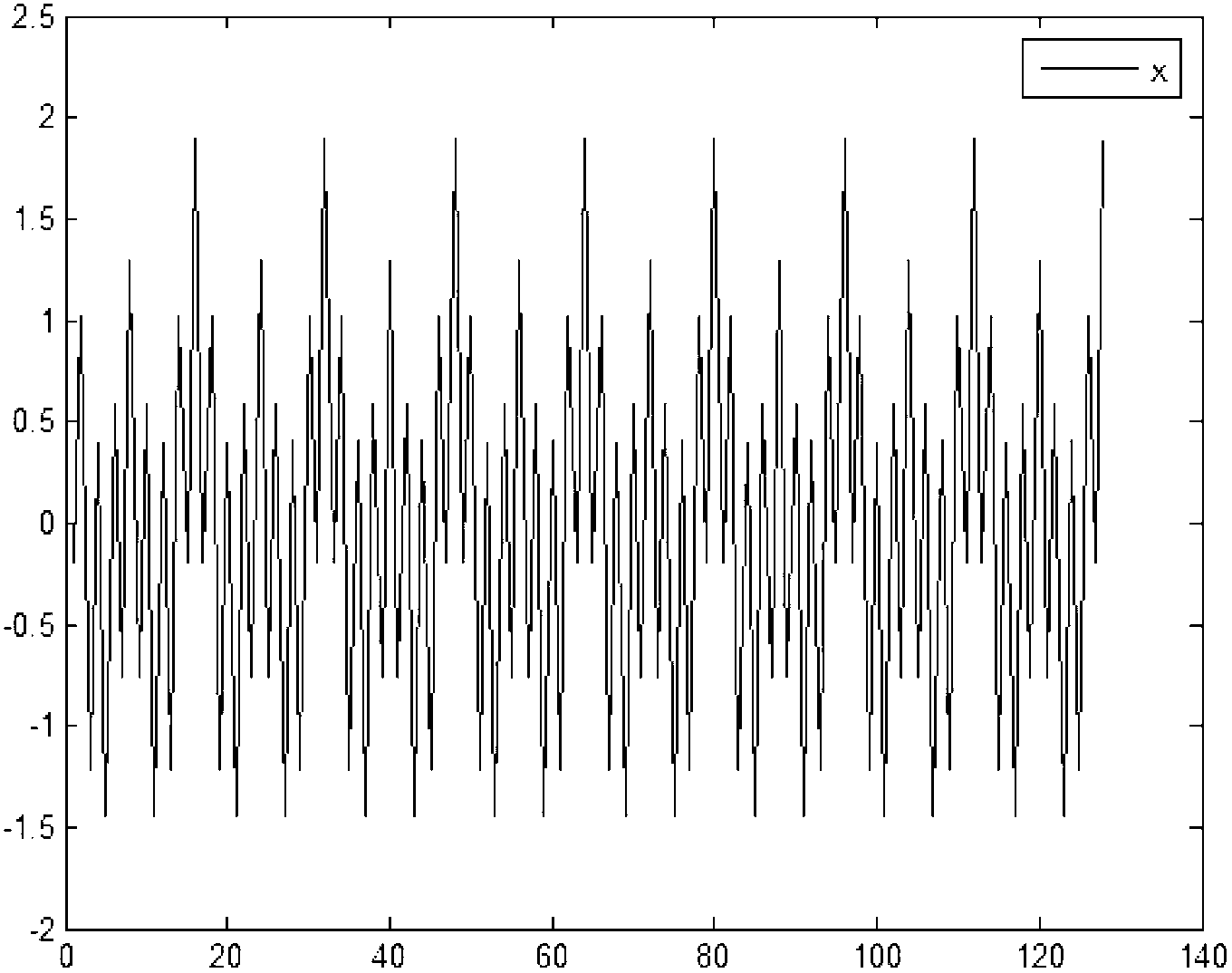
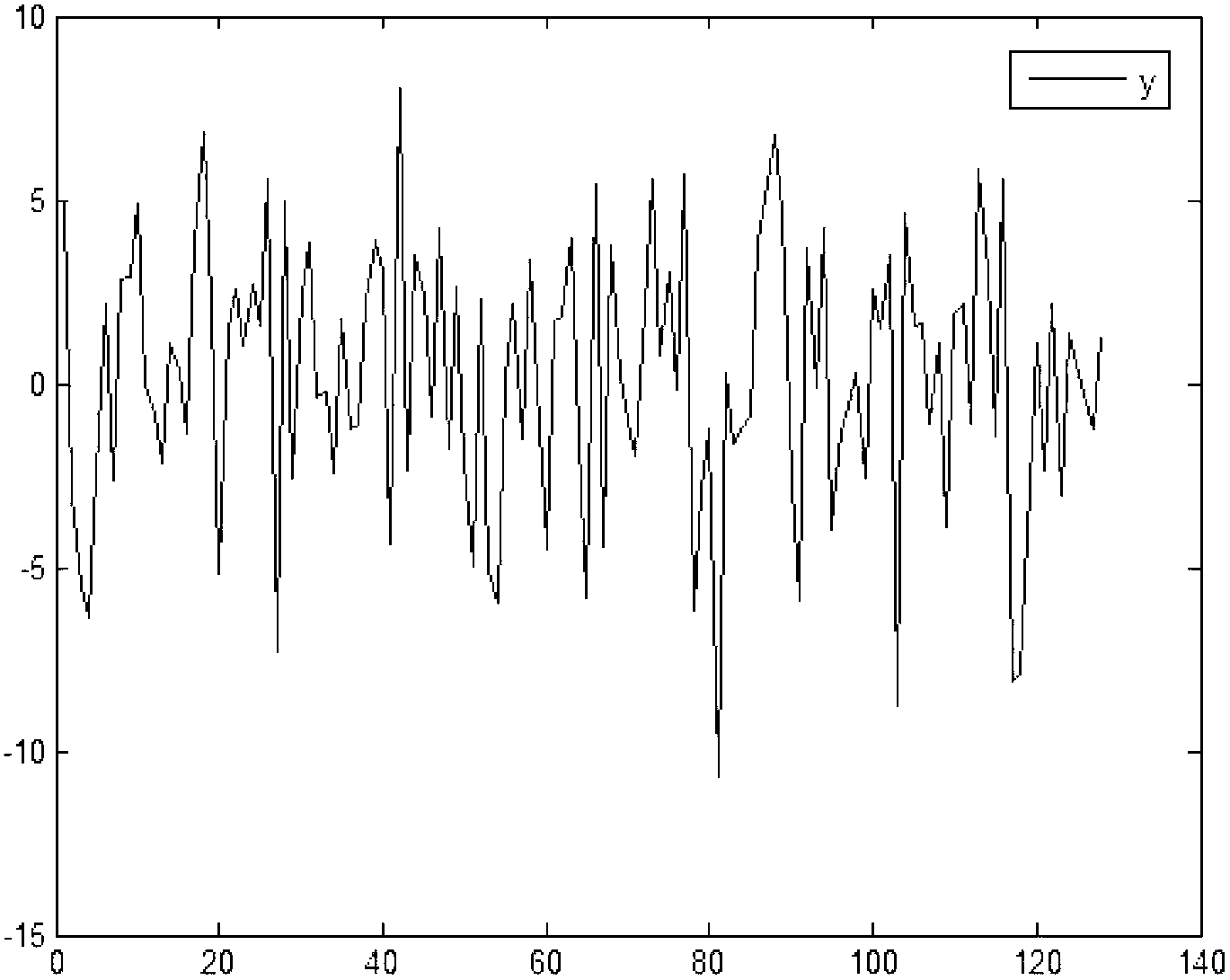
[0027] The present invention includes two stages of data encryption at the source end and data decryption at the destination end during specific implementation. The data in this example are superimposed by the following four signals: 0.3cos100πt, 0.6cos200πt, 0.1cos400πt and 0.9cos800πt, where t is the sampling time. Let m=128, n=32, s=7, k=41 in this example.
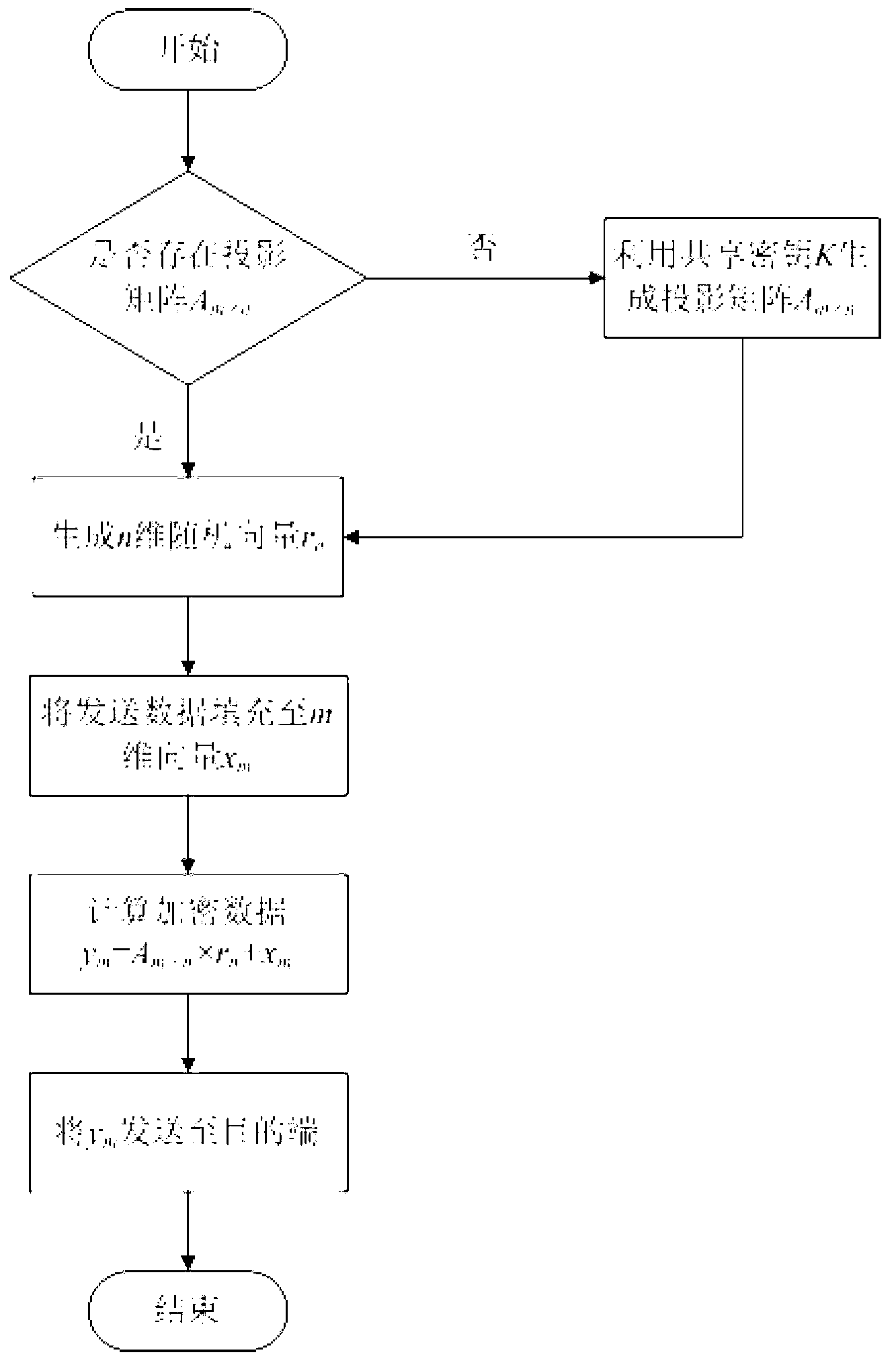
[0028] First, the source performs data encryption, which is implemented according to the following specific steps:
[0029] 1) The source judges whether there is a projection matrix A 128×32 , if it does not exist, go to step 2), otherwise go to step 3);
[0030] 2) The source uses the shared key K as a seed to generate the projection matrix A 128×32 , in this example
[0031] A 128 × 32 = - 0.0503 0.1644 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com