Computer system and its confidential method
A computer system and computer technology, applied in computing, instruments, electrical digital data processing, etc., can solve the problem that the power-on password cannot achieve the computer security function, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
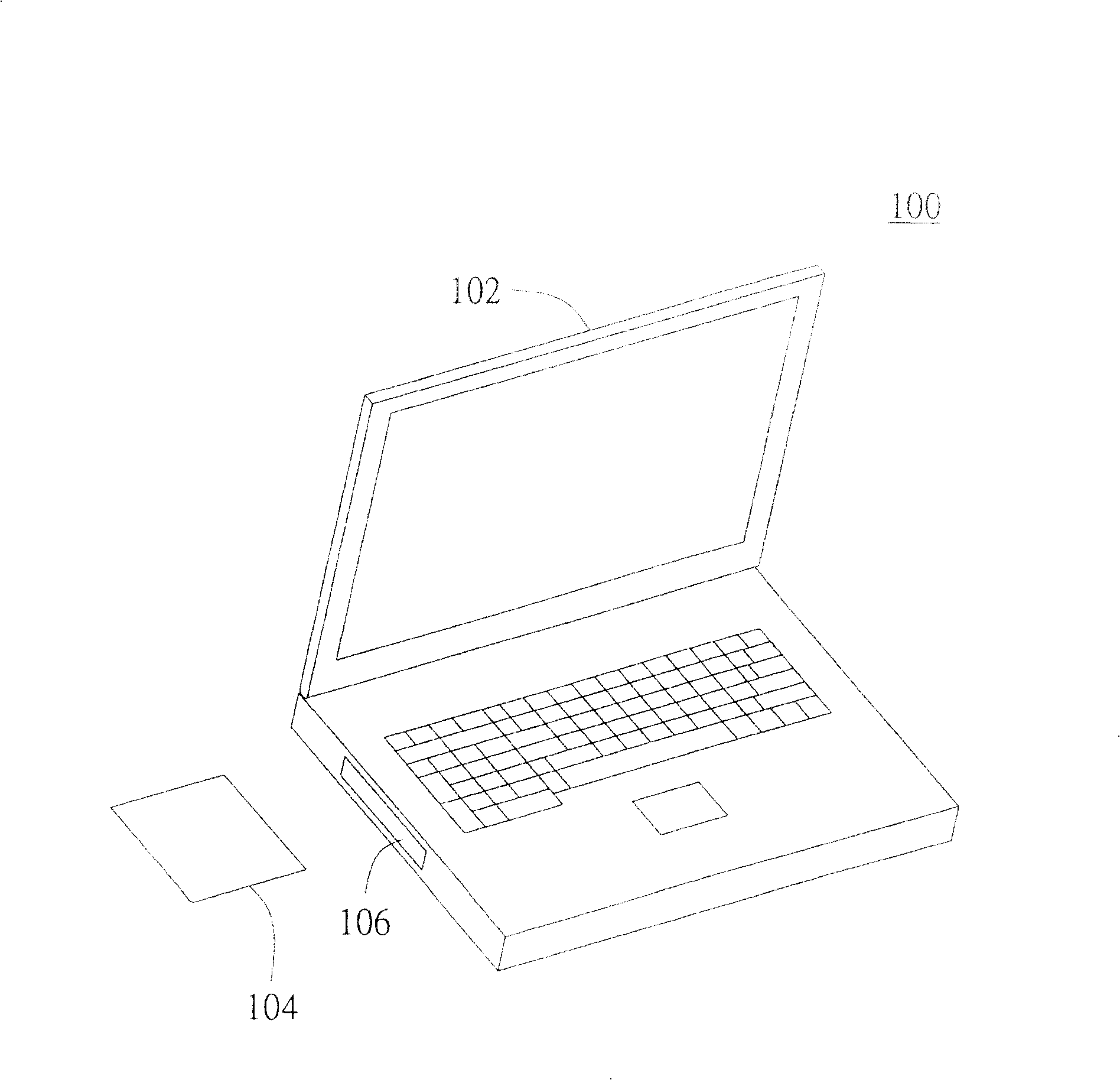
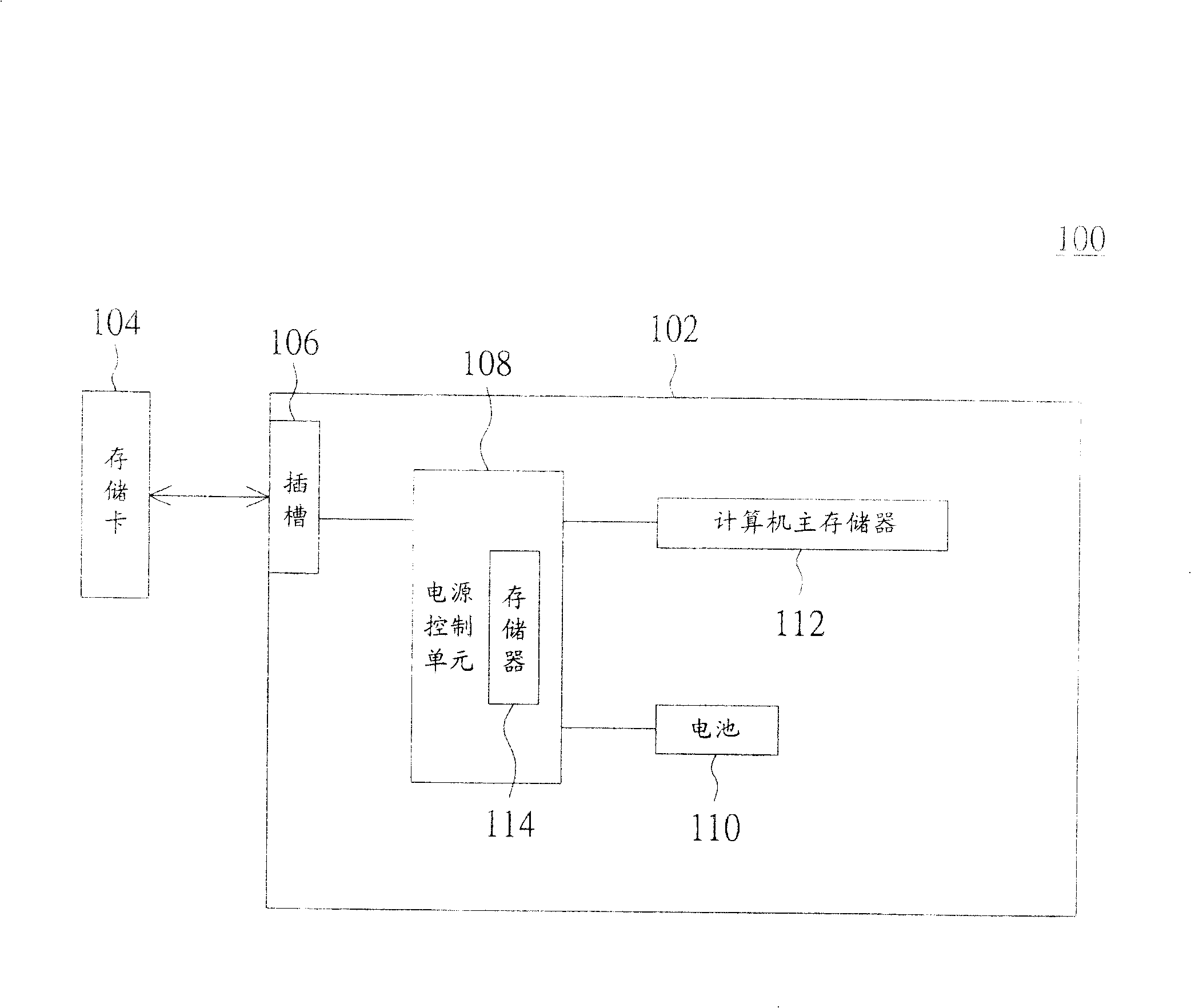
[0022] The invention provides a perfect computer security method. By storing the basic input / output system (Basic Input / Output System, hereinafter referred to as BIOS) in a plug-in memory or designing it as a memory card, and designing a corresponding slot on the host computer, the plug-in card The flash memory or memory card can be selectively separated or connected with the computer host. In this way, when the plug-in memory card or memory card is pulled out of the computer host, the computer host cannot be booted up or wake up from the power saving mode because there is no BIOS, thereby achieving a more complete computer security method .
[0023] Please refer to figure 1 , which shows a schematic diagram of a computer system according to a preferred embodiment of the present invention. The computer system 100 is, for example, a general desktop computer (DESKTOP), a server (SERVER), a barebones system, a notebook computer (NOTEBOOK), or a personal digital mobile device. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com