Three-party authentication method and device as well as intelligent card supporting two-way authentication
A two-way authentication and three-party authentication technology, applied in the field of smart cards, can solve the problems of poor binding effect, easy cracking, low security, etc., and achieve the effect of ensuring specificity and security, ensuring security, and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
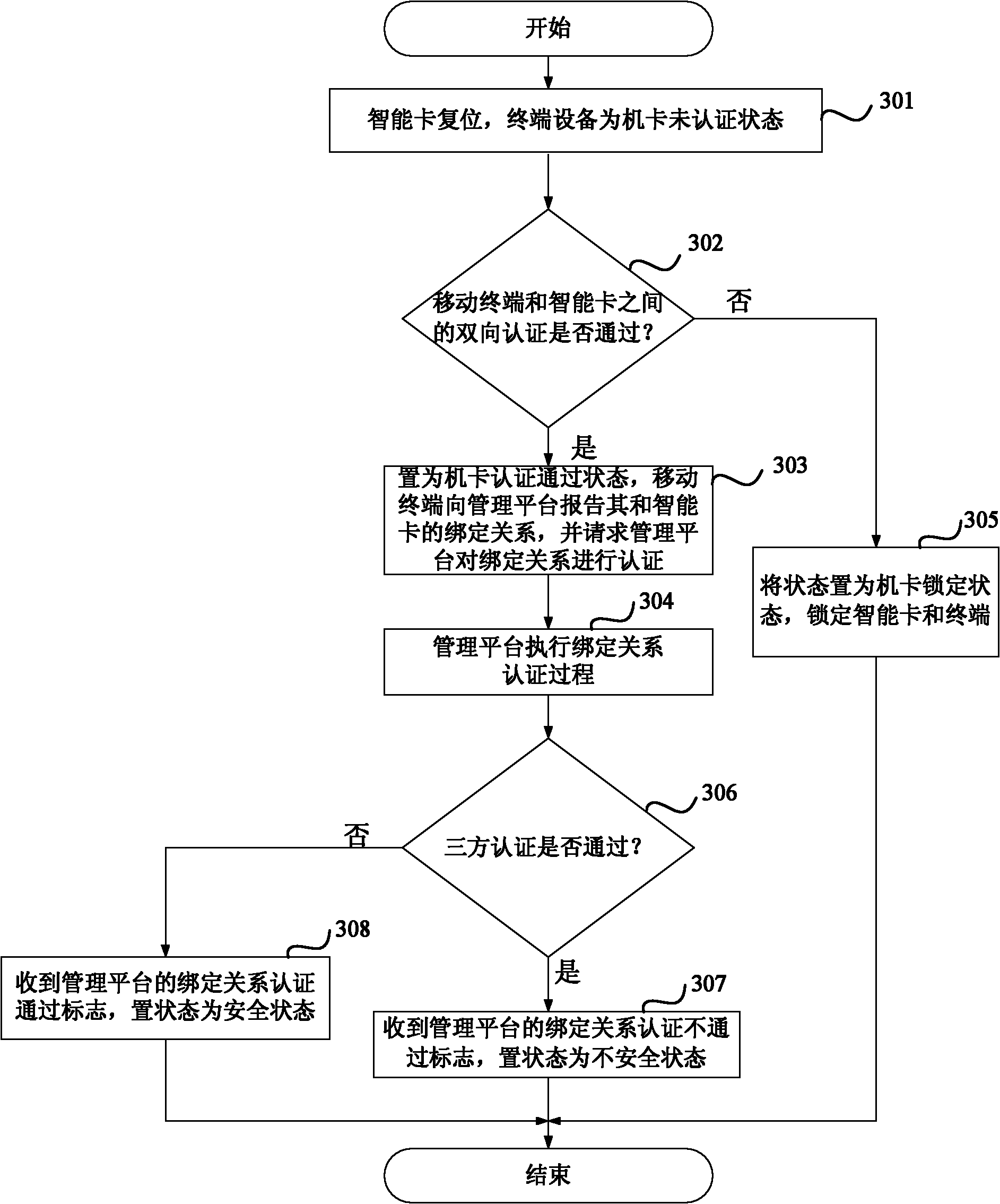
[0138] Such as Figure 7 As shown, the terminal, the smart card, and the management platform of this embodiment successfully perform the three-party authentication process, which mainly includes:
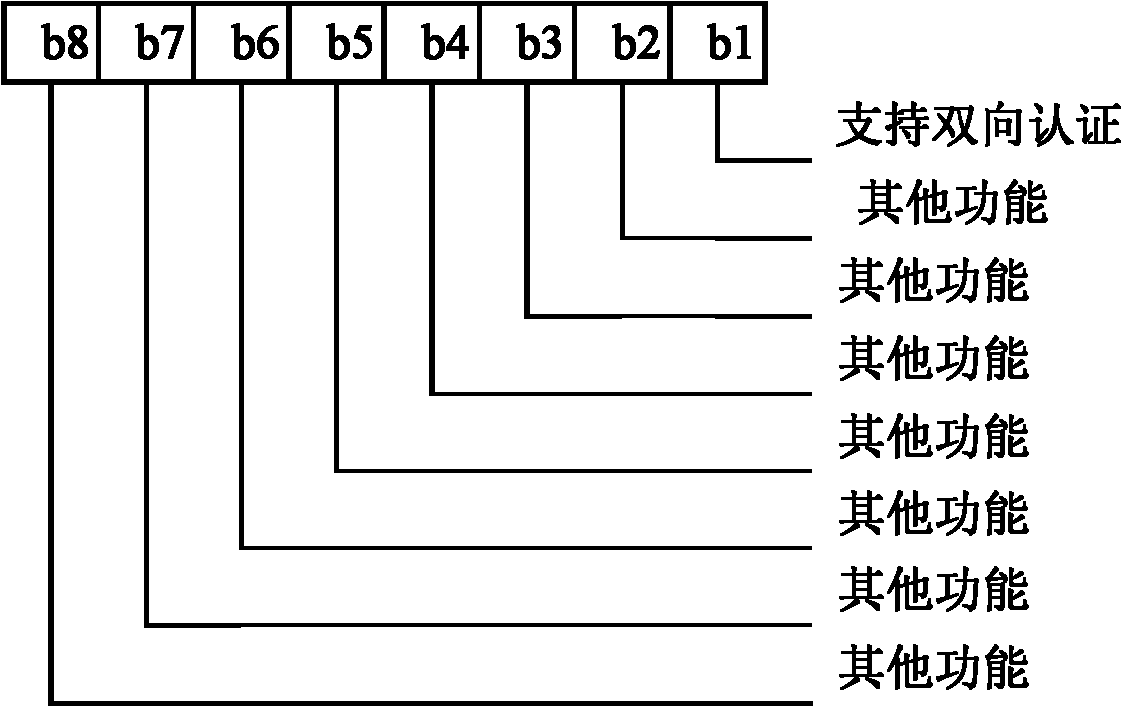
[0139] Step 701, the Internet of Things terminal is turned on, and after the smart card is reset, the terminal executes the ProfileDownload process, and the terminal sends a TERMINAL PROFILE command to the smart card, where bit1 in the 40th byte of the TERMINAL PROFILE command is 1, which means that the terminal and the smart card need to perform bidirectional certified.
[0140] Step 702: After receiving the command, the smart card judges that the corresponding bit in the TERMINAL PROFILE command is 1, and executes a two-way authentication process between the mobile terminal and the smart card.
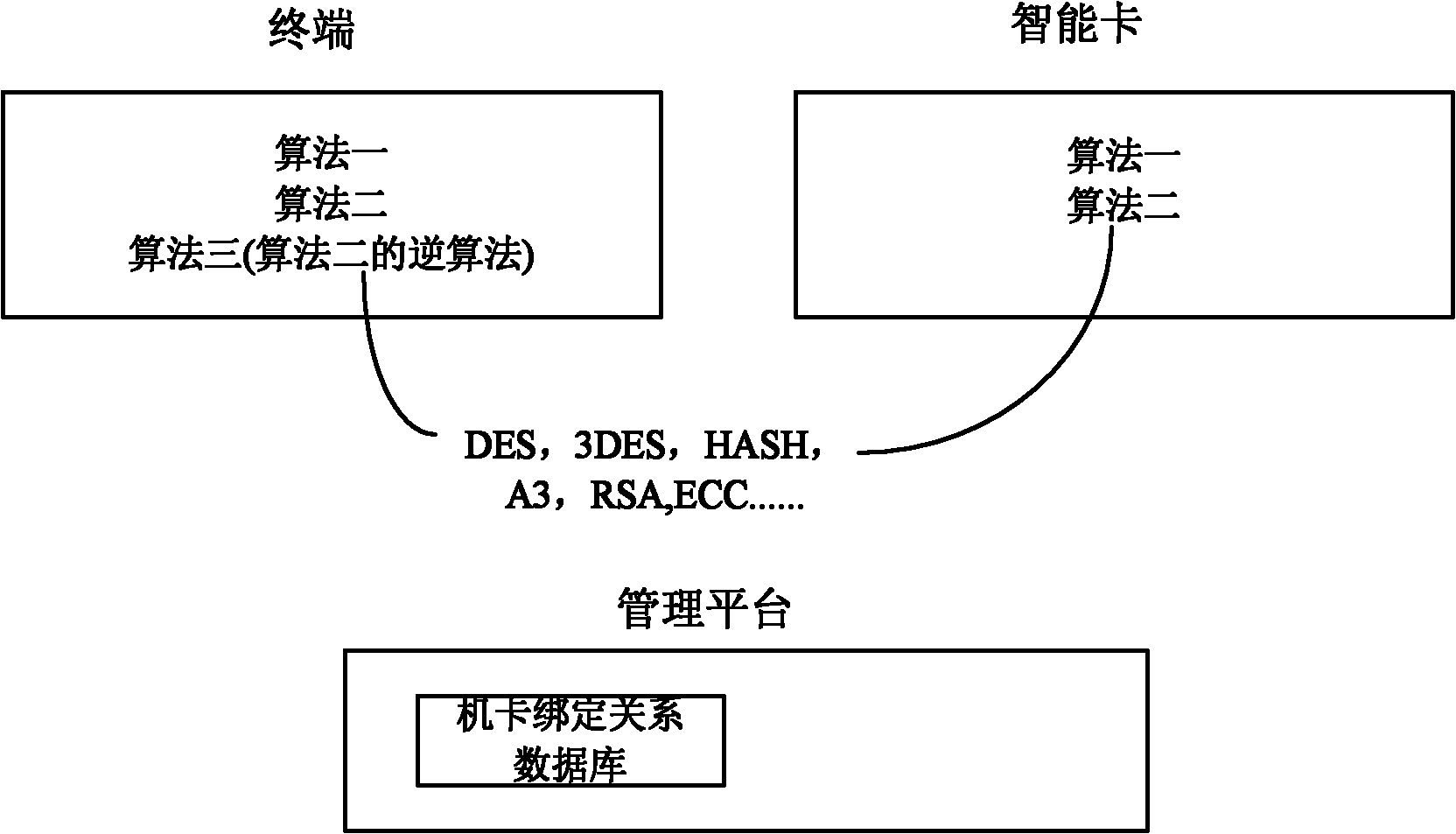
[0141] Specifically, in this embodiment, random numbers and IMSI are used as authentication information. Algorithm 1 and Algorithm 2 are respectively stored in the smart card and the term...
Embodiment 2
[0154] Figure 8 For the terminal, smart card, and management platform in the embodiment of the present invention, the process of three-party authentication failure, such as Figure 8 As shown, the process mainly includes:
[0155] In step 801, the terminal is turned on, and after the smart card is reset, the terminal executes the Profile Download process, and the terminal sends a TERMINAL PROFILE command to the smart card, wherein bit7 in the 50th byte of the TERMINAL PROFILE command is 1, which means that two-way authentication between the terminal and the smart card is required.
[0156] Step 802, after receiving the command, the smart card judges that the corresponding bit in the TERMINAL PROFILE command is 1, and therefore executes a bidirectional authentication process between the mobile terminal and the smart card.
[0157] Specifically, in this embodiment, IMSI is used as the authentication information. Algorithm 1 and Algorithm 2 are respectively stored in the smart ...
Embodiment 3
[0166] Figure 9 For the terminal, smart card, and management platform in the embodiment of the present invention, the process of three-party authentication failure, such as Figure 9 As shown, the process mainly includes:
[0167] In step 901, the terminal is turned on, and after the smart card is reset, the terminal executes the Profile Download process, and the terminal sends a TERMINAL PROFILE command to the smart card, wherein bit1 in the 62nd byte of the TERMINAL PROFILE command is 1, which means that two-way authentication between the terminal and the smart card is required.
[0168] Step 902, after receiving the instruction, the smart card judges that the corresponding bit in the TERMINAL PROFILE instruction is 1, so the two-way authentication process between the mobile terminal and the smart card is executed.
[0169] Specifically, in this embodiment, random numbers and IMSI are used as authentication information. Algorithm 1 and Algorithm 2 are respectively stored i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com