Method and system for smart phone user identity identification
A user identification, smart phone technology, applied in electrical components, wireless communication, network data management and other directions, can solve the problems of cumbersome and inconvenient operation, and achieve the effect of convenient and simple implementation and simplify the user identification process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The embodiments of the present invention will be described in detail below with reference to the accompanying drawings, wherein the following embodiments are given to provide a comprehensive and thorough understanding of the present invention, but not to limit the present invention.
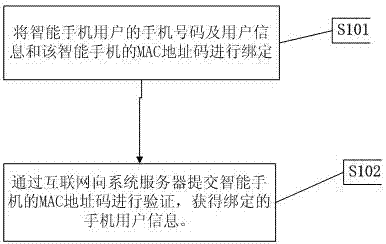
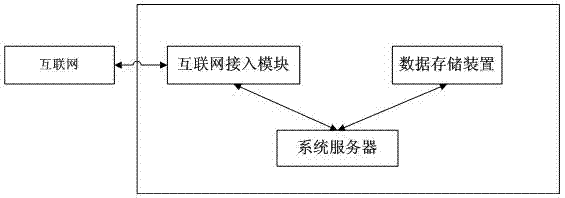
[0017] Such as figure 2 As shown, the smart phone user identification system of the present invention is composed of a system server, a data storage module and an Internet access module; the system server is electrically connected to the data storage module, and the system server is electrically connected to the Internet access module, and connected to the the Internet. Submit the MAC address code of the smart phone to the system server through the Internet for verification, and obtain the bound mobile phone user information. Wherein the system server, the data storage module and the Internet access module are all prior art.
[0018] Such as figure 1 Shown, smart phone user identificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com