DDoS attacker tracing method based on autonomous system
An autonomous domain and marking method technology, applied in the field of network security, can solve problems such as implementation difficulties, and achieve the effects of simple implementation, low computational load and path reconstruction consumption, and good scalability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further elaborated below in conjunction with specific examples.
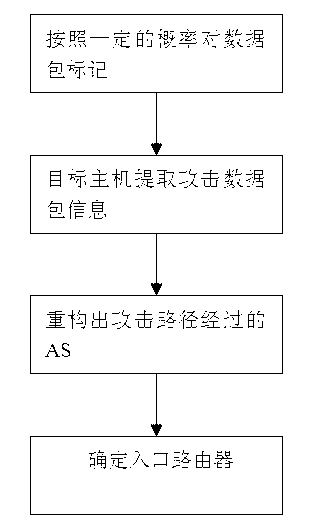
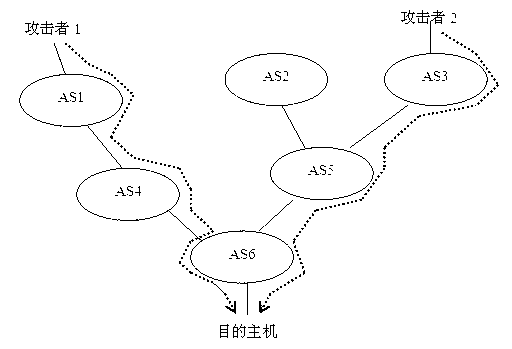
[0031] Such as figure 1 As shown, firstly, the ingress router marks the data packets with a certain probability, then the target host extracts the attack data packets, performs path reconstruction to obtain the AS through which the attack path passes, and finally confirms the ingress router.
[0032] one. Selection of Marking Probability
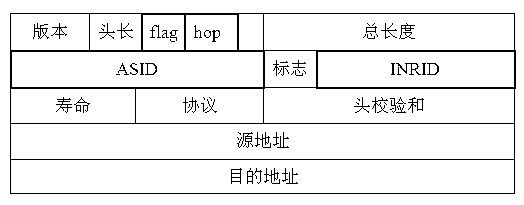
[0033] Assume that an attack path passes through d ASs, and the ingress router on each AS marks the data packet with probability p, then the probability of each data packet passing through d nodes to be marked is at least dp(1-p) d-1 . According to the uneven probability coupon collector problem, the maximum number of packets required to reconstruct the attack path is: . Therefore, the number of data packets required for path reconstruction is related to path length d and marking probability p, and selecting an appropriate marking pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com