Product source tracing scheme based on PKI (Public Key Infrastructure) and two-dimensional codes
A technology of two-dimensional codes and two-dimensional code information, which is applied in the field of product traceability solutions based on PKI and two-dimensional codes, and can solve problems such as the impossibility of determining input values
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
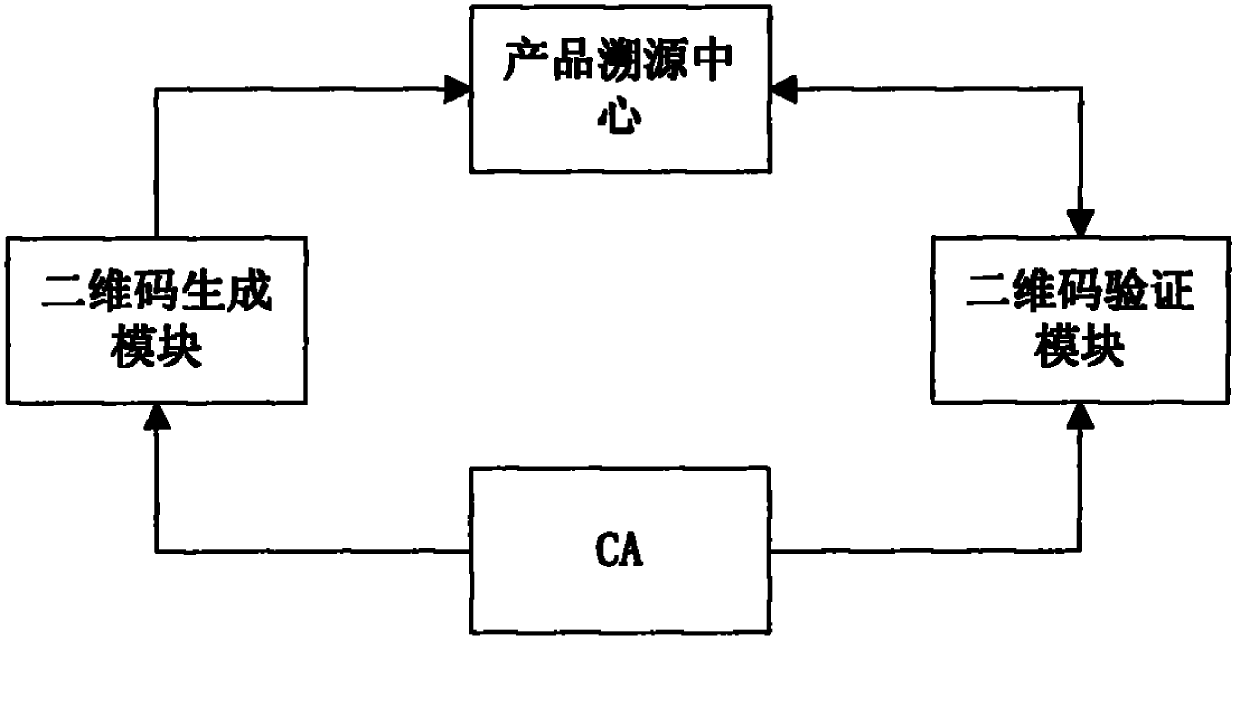
[0018] Through the technical solution of the invention, users can easily confirm whether the product they purchased is produced by the manufacturer marked on the package. The scheme is implemented by taking the mobile phone as the carrying platform of the two-dimensional code verification module as an example. The specific implementation scheme is as follows:
[0019] (1) The manufacturer's CA system applies, and the CA system provides the private key and the corresponding digital certificate. The private key is stored in the USB KEY physical device and provided to the manufacturer.
[0020] (2) The manufacturer inputs the plaintext of the manufacturer and its product information (referred to as product information) to the two-dimensional code generation module, and the generation module will generate the following two sets of data: the ciphertext of the product information encrypted by the private key and the HASH value of the product information, or Product information plain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com