Detection method and system of rebound type Trojan
A detection system and Trojan horse technology, applied in the field of malicious code discovery, can solve the problems of not being able to find known malicious code malicious code well, and unable to detect malicious code, so as to overcome the inability to detect malicious code and cut off the connection in time to protect the host. safe effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the above-mentioned purposes, features and advantages of the present invention more obvious and easy to understand, the technical solutions in the present invention will be further detailed below in conjunction with the accompanying drawings illustrate.
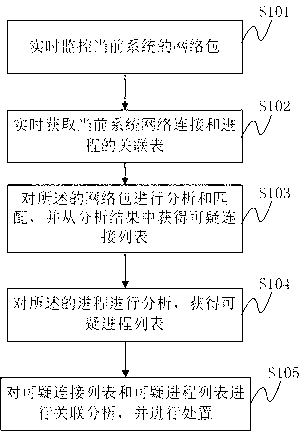
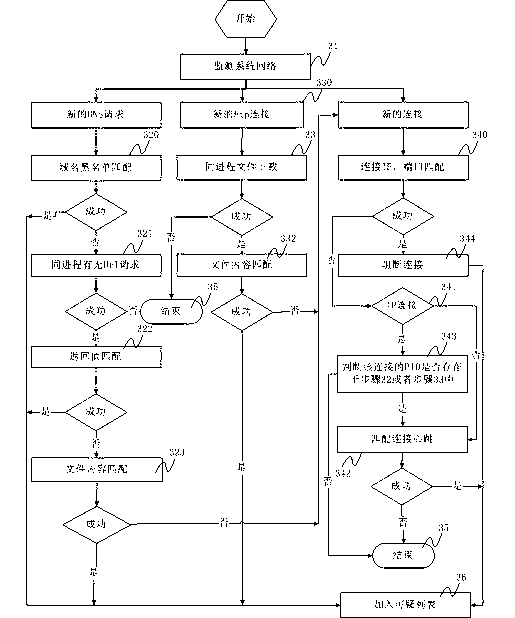
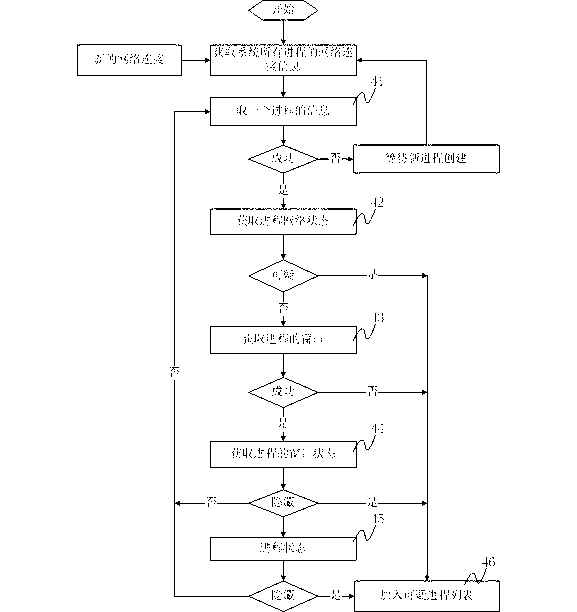
[0073] The present invention proposes a malicious code discovery solution based on the rebounding Trojan online mode and the operating environment of the host, that is, the control Trojan is discovered by analyzing the network behavior and process status of the host.
[0074] The malicious code discovery method of the present invention based on the rebound Trojan online mode and the host operating environment specifically includes the steps of real-time monitoring system network, real-time acquisition of current network connection and process association steps, network packet ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com