Method and system of data routing
A data routing and data row technology, applied in the field of data routing methods and systems, can solve problems such as packet discarding and failure to identify fixed network private IP addresses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0077] In this process, when the RG is in the routing mode, taking the GRE tunnel as an example, the RG and X-MAG communicate the dynamic negotiation information of the GRE tunnel through the EAP authentication message exchange, including: GRE Key, and trigger the X-MAG to send the mobile core The network element initiates the PMIP / GTP tunnel establishment process. The GRE tunnel is just one of the tunnel types, and it can also be applied to other types of dynamic negotiation of Layer 3 tunnels that require the cooperation of control signaling.
[0078] Such as Figure 5 As shown, this process specifically includes:
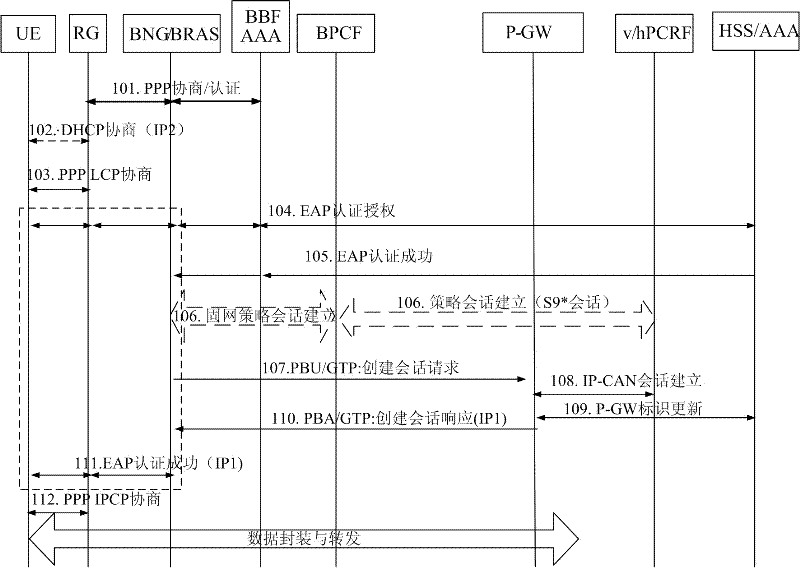
[0079]Step 501: PPP negotiation and authentication process between RG and BNG / BRAS; and optionally, DHCP negotiation process between UE and RG. During DHCP negotiation, RG assigns an IP address to UE, usually a private network IP. The BNG / BRAS may initiate the establishment of a fixed network policy session with the Broadband Policy Control Function (BPCF).
...
Embodiment 2
[0103] The difference between this process and the first embodiment is that the RG and X-MAG use DHCP messages or PMIP messages to transmit tunnel negotiation information, and at the same time trigger X-MAG to initiate a PMIP tunnel establishment process to mobile core network elements.
[0104] Such as Figure 6 As shown, the process of this embodiment mainly includes:
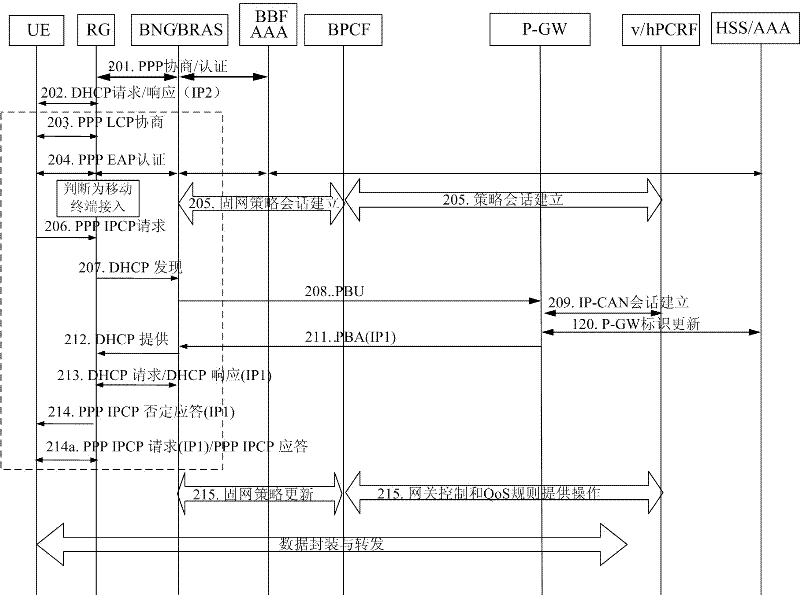
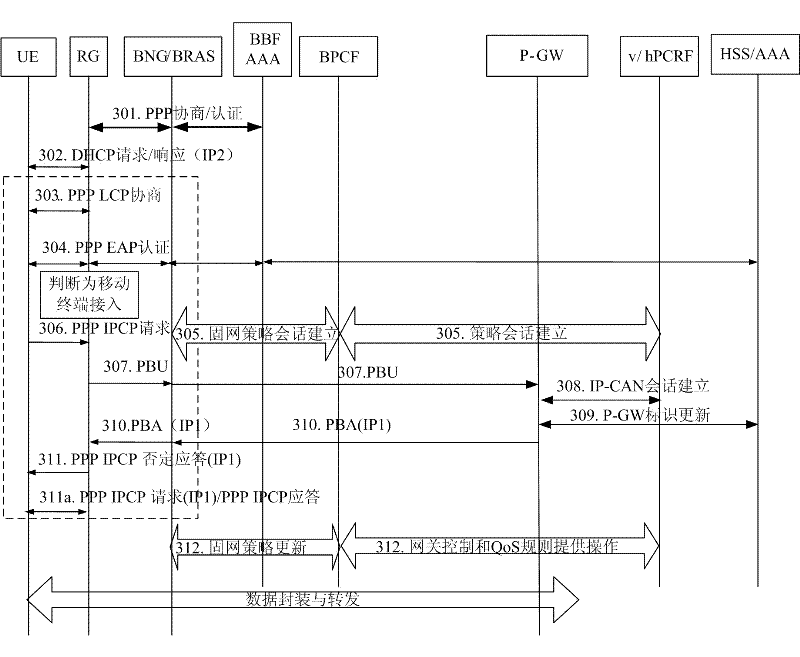
[0105] Step 601: UE, RG and BNG / BRAS perform fixed network IP address allocation process interaction; if the UE is a mobile terminal, then the UE and RG complete the PPP LCP negotiation and EAP authentication process.
[0106] Step 602: After completing the EAP authentication, the UE sends a PPP IPCP request message to the RG.
[0107] Step 603: After the RG receives the PPP IPCP request message, if the UE is a mobile terminal user, it constructs a DHCP discovery or PBU message locally and sends it to the X-MAG. The message needs to be extended to carry downlink GRE Key information.
[0108] Among them, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com