Safety control method for accessing wireless network and terminal
A wireless network and security control technology, applied in the field of communication, can solve problems such as complex operations and achieve the effect of reducing information interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
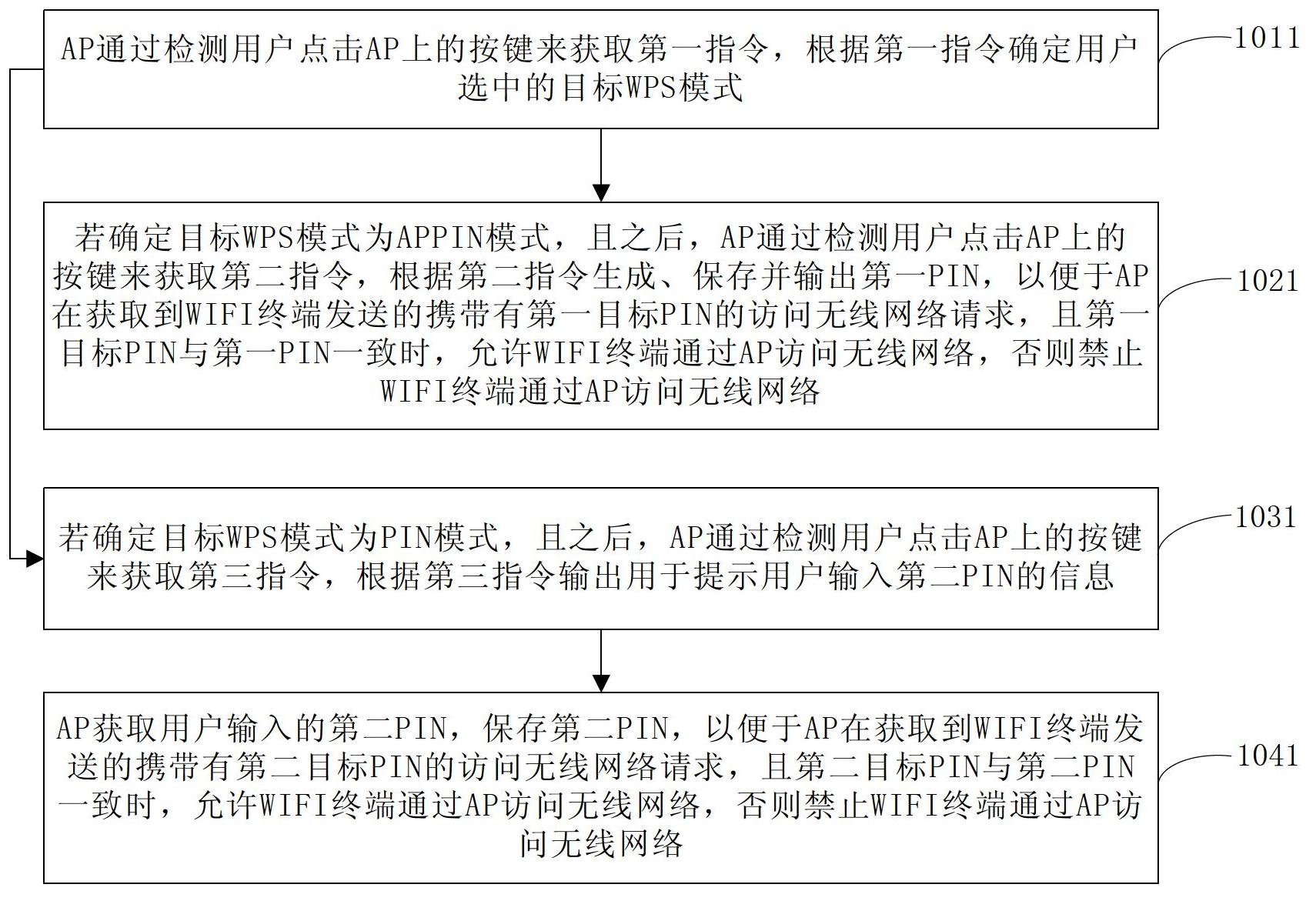
[0044] See figure 1 , The flow chart of a security control method for accessing a wireless network provided by this embodiment, the specific implementation process includes the following steps:
[0045] 101: The AP obtains the first instruction, and determines the target WIFI protection setting WPS mode according to the first instruction.
[0046] Optionally, the AP in this embodiment may be a WIFI wireless router.
[0047] 102: If it is determined that the target WPS mode is the AP PIN mode, and then, the AP obtains the second instruction, generates, saves, and outputs the first PIN according to the second instruction, so that the AP receives the first target PIN sent by the WIFI terminal When the request to access the wireless network is requested, and the first target PIN is consistent with the first PIN, the WIFI terminal is allowed to access the wireless network through the AP, otherwise the WIFI terminal is prohibited from accessing the wireless network through the AP.
[0048] ...
Embodiment 2
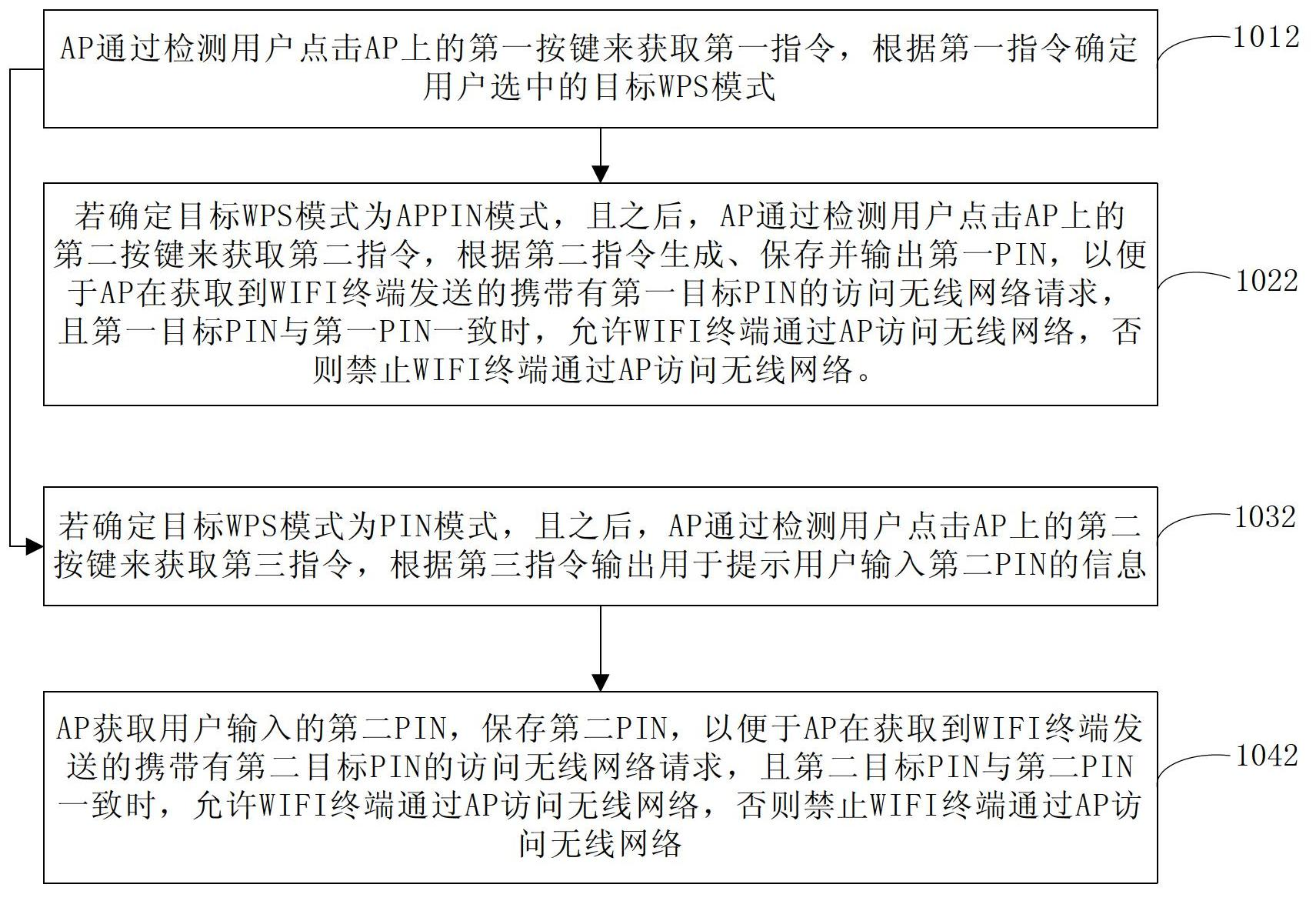
[0100] See Figure 4 , The flow chart of a security control method for accessing a wireless network provided by this embodiment, the specific implementation process includes the following steps:
[0101] 201: The WIFI terminal obtains the fourth instruction, generates and outputs a personal identification code PIN according to the fourth instruction, so that the user can input the PIN on the wireless access point AP to implement the WIFI protection setting WPS function.
[0102] This embodiment provides a security control method for accessing a wireless network. Through this embodiment, when configuring the WPS function, the WIFI terminal generates and outputs the personal identification code PIN according to the acquired fourth instruction, and the user will generate Enter the PIN to the AP to complete the configuration of the WPS function. Compared with the prior art, in the embodiment of the present invention, the user does not need to log in to the AP configuration interface on...
Embodiment 3
[0114] See Image 6 , The structural diagram of a wireless access point AP provided in this embodiment includes:
[0115] The obtaining module 601 is used to obtain the first instruction;
[0116] The processing module 602 is configured to determine the target WIFI protection setting WPS mode according to the first instruction after the acquiring module 601 acquires the first instruction;
[0117] The above-mentioned obtaining module 601 is further configured to obtain the second instruction after the processing module 602 determines that the target WPS mode is the AP PIN mode;
[0118] The generating module 603 is configured to generate the first personal identification code PIN according to the second instruction after the acquiring module 601 acquires the second instruction;
[0119] The storage module 604 is configured to store the first PIN after the generation module 603 generates the first PIN;
[0120] The output module 605 is configured to output the first PIN after the generati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com