Method for improving penetration rate and stability of STUN-P2P through universal plug-n-play (UPnP)
A STUN-P2P, penetration rate technology, applied in the field of network multimedia, can solve the problems of default support, limited scope of application, and inability to establish P2P data links at the playback end, so as to improve stability, success rate, and practicality sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
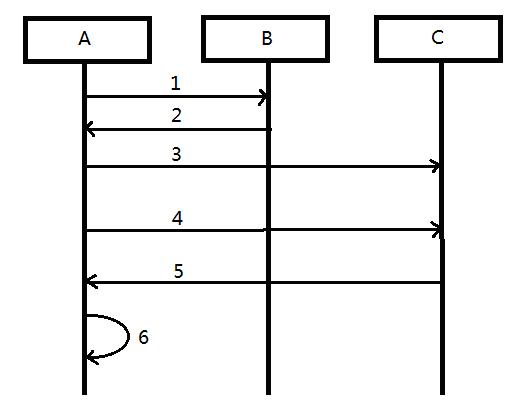
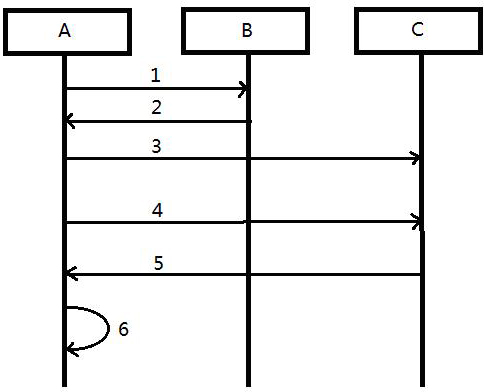
[0018] The invention consists of a UPnP port mapping client running on a network device node, a customized STUN client running on a network device node (which can accept specified NAT port mapping), and a control program. see figure 1 , the concrete steps of the present invention are as follows:
[0019] Step 1: Map client A to NAT through node UPnP port B Initiate a port mapping request.
[0020] Step 2: If the port mapping request is successful, feedback that UPnP has successfully established port mapping on the NAT to the node. If the feedback data cannot be obtained, proceed to step 4, and connect to the STUN server C to obtain the port.
[0021] Step 3: Pass the established port mapping above to the STUN client to optimize the STUN client and establish connections such as heartbeat messages with the STUN server. The STUN client here is the key point. The optimized STUN client can accept the specified NAT port mapping, can quickly map valid ports, and get connected to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com