Method and system for improving safety of electronic wallets
An electronic wallet and wallet technology, applied in the field of information security, can solve the problems of no provision, system crash, and no use of public cryptography system security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] [Example 1] Card signature
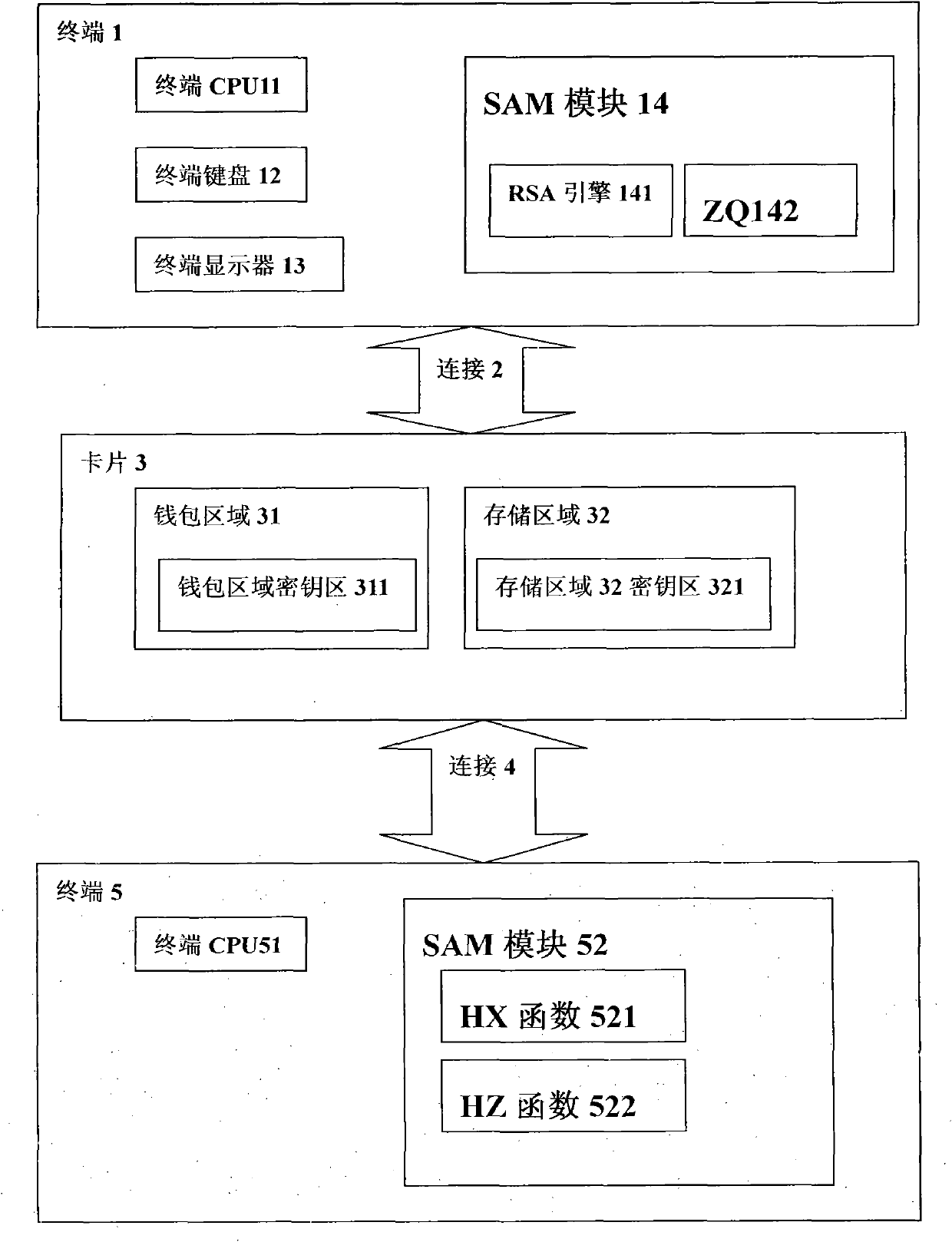
[0034] In the first embodiment of the present invention, in order to identify the card, generally there will be an identification in the card, for example, the MifareS50 card has a globally unique serial number. Of course, the card issuance of the application system also needs to write personal information, card issuer information, card issue time information, etc. These information can also become identification data, called ID, that is, the data that distinguishes the card from other cards.
[0035] The system selects the asymmetric encryption algorithm RSA and the key pair (S1, S2); sign the ID with RSA S1 (ID) and stored in the data area of the card. When the terminal is used, first read out the ID of the card and the ID signature RSA stored in the card S1 (ID), the terminal calculates RSA S2 (RSA S1 (ID)) to get the ID and compare it with the read ID. When they match, the terminal can confirm the validity of the card.
[0036] ...
Embodiment 2
[0039] [Example 2] No signature
[0040] The core of the present invention is to adopt the method of storing the depreciation key (consumption key) in the electronic wallet, and further providing protection to the depreciation (consumption key). When using an electronic wallet, different operations are performed according to credit collection and non-credit collection. According to the second embodiment of the present invention, a method for enhancing the security of an electronic wallet, we can use the Mifare S50 card for illustration.
[0041] Each Mifare S50 card has a globally unique ID number and 16 storage areas, numbered from 0 to 15. Each storage area has two passwords: a value-added password and a value-decreased password. When the devaluation password authentication is passed, the data in the storage area can be devalued, and when the value-added password is verified, the data in the storage area can be value-added.
[0042] The electronic wallet system using Mifa...
Embodiment 3
[0050] [Example 3] signature
[0051] According to the third embodiment of the present invention, a method for a safe electronic wallet, there are value-added function HX, depreciation function HZ, enhancement function ZQ, electronic wallet identification ID, asymmetric encryption algorithm RSA and key pair (S1, S2) here. ), user PIN code. We choose area 1 as the storage area for the balance in the electronic wallet. Area 2 is an area for storing depreciation keys.
[0052] In this way, the value-added password is HZ(ID); the consumer password is HX(ID); the enhanced password is ZQ(ID); calculate RSA S1 (ID, HX(ID)) and stored together with the PIN code in an area protected by the enhanced password ZQ(ID).
[0053] When used in a credit terminal, the terminal generally has a depreciation function HX; the terminal first reads out the identification ID number of the electronic wallet, and calculates HX(ID), and uses HX(ID) and the consumption key in the electronic wallet for ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com