Method and equipment for negotiating internet key exchange (IKE) message
A packet negotiation and device technology, applied in the field of communication, can solve the problems of IPsec tunnel oscillation, network disconnection, network congestion, etc., and achieve the effect of alleviating the phenomenon of network oscillation or network disconnection, and reducing the probability of oscillation or network disconnection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The specific embodiments of the present invention will be described in further detail below in conjunction with the drawings and embodiments. The following examples are used to illustrate the present invention, but not to limit the scope of the present invention.
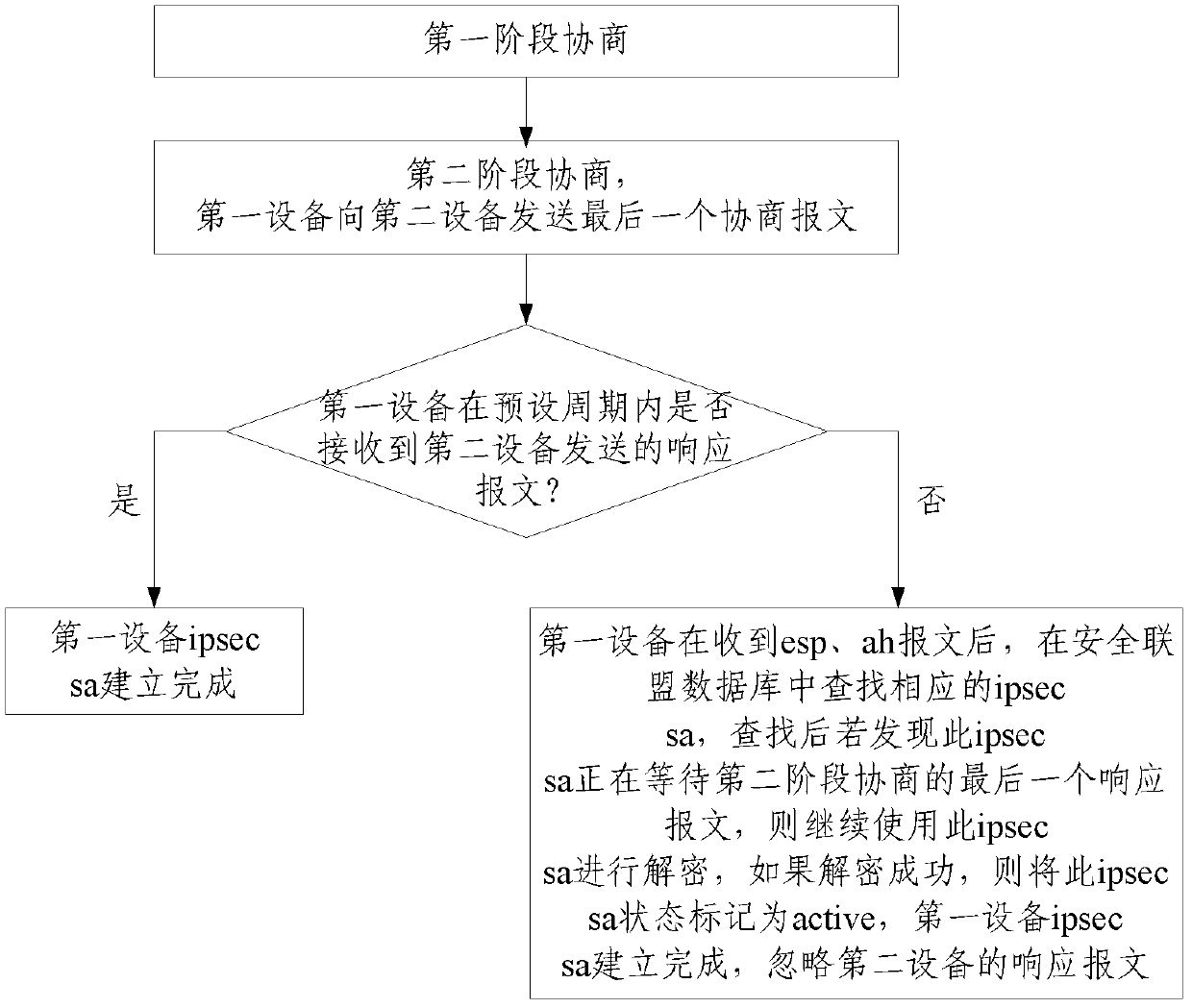
[0030] The Internet Key Exchange (IKE) process is divided into the first stage of negotiation and the second stage of negotiation. The first stage of negotiation is divided into main mode and aggressive mode. The second stage of negotiation is fast mode negotiation. After the first stage of negotiation, IKE sa will be established. Its purpose is to perform identity authentication and provide protection for the second phase of exchange. The purpose of the second phase of exchange is to generate ipsec sa under the protection of the first phase of sa. ipsec sa is the material that directly protects the data flow. Provided for use by ESP / AH, where one IKE sa can protect and generate multiple ipsec sa.
[0031] In the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com