Encryption key generation device
A technology for encrypting keys and generating devices, applied to secure communication devices and key distribution, can solve problems such as inability to guarantee hacker resistance, and achieve the effect of reducing the amount of information and improving management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 Embodiment
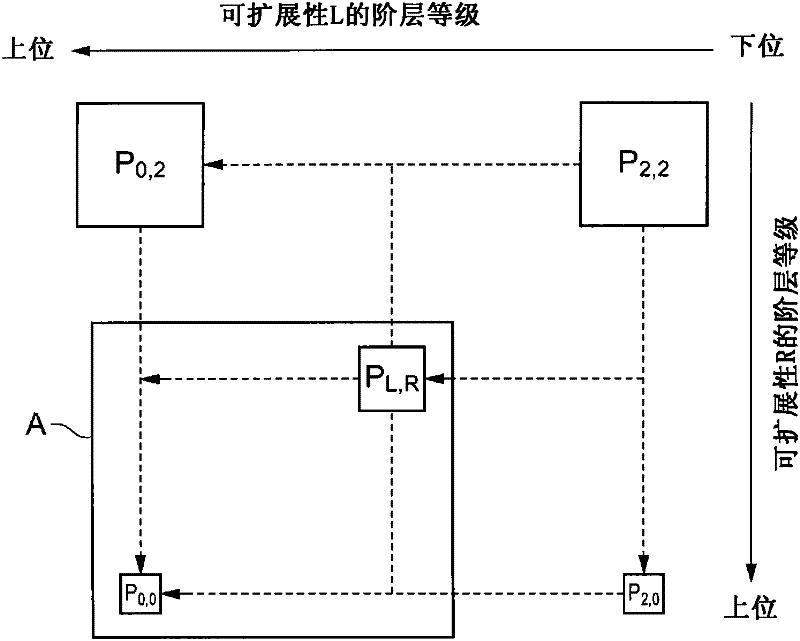
[0087] Next, the encryption key generation operation performed in the first embodiment of the encryption key generation device of the present invention will be described. Furthermore, the encryption key generation device of the first embodiment has Figure 7 The structure shown, more specifically by figure 2 The hardware structure shown in (a) is realized. In this first embodiment, the scalability as the access control object is set to scalability L (layer) and scalability R (resolution level), and the number of layers of scalability L is N L Set to 3, the number of levels of scalability R N R Set to 3. At this time, the packets of each level in the scalability L and R are made into a 3×3 matrix component P i,j (i=0, 1, 2; j=0, 1, 2) for processing. also, Figure 8 is a conceptual diagram for explaining the encryption key generation operation performed by the first embodiment of the encryption key generation device of the present invention ( Figure 7 operation of the ...
no. 2 Embodiment
[0107] Next, the encryption key generation operation executed by the second embodiment of the encryption key generation device of the present invention will be described. In addition, the encryption key generation device of the second embodiment also has the same Figure 7 The structure shown, more specifically by figure 2 The hardware structure shown in (a) is realized. In this second embodiment, the scalability as the access control object is set to scalability L (layer) and scalability R (resolution level), and the number of levels of scalability L is N L Set to 3, the number of levels of scalability R N R Set to 2. At this time, the packets of each level in the scalability L and R are as a 3×2 matrix component P i,j (i=0, 1, 2; j=0, 1) are processed. also, Figure 10 is used to describe the encryption key generation operation performed in the second embodiment of the encryption key generation device of the present invention ( Figure 7 A conceptual diagram of the o...
no. 3 Embodiment
[0121] Next, the encryption key generation operation performed by the encryption key generation device according to the third embodiment of the present invention will be described. In addition, the encryption key generation device of the third embodiment also has the same Figure 7 The structure shown, more specifically, consists of figure 2 The hardware structure shown in (a) is realized. In this third embodiment, the scalability as the access control object is set to scalability L (layer) and scalability R (resolution level), and the number of layers of scalability L is N L Set to 4, the number of layers of scalability R N R Set to 3. At this time, the packets of each level in the scalability L and R are as a 4×3 matrix component P i,j (i=0, 1, 2; j=0, 1, 2, 3) are processed. also, Figure 12 is used to describe the encryption key generation operation performed in the third embodiment of the encryption key generation device of the present invention ( Figure 7 A conc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com