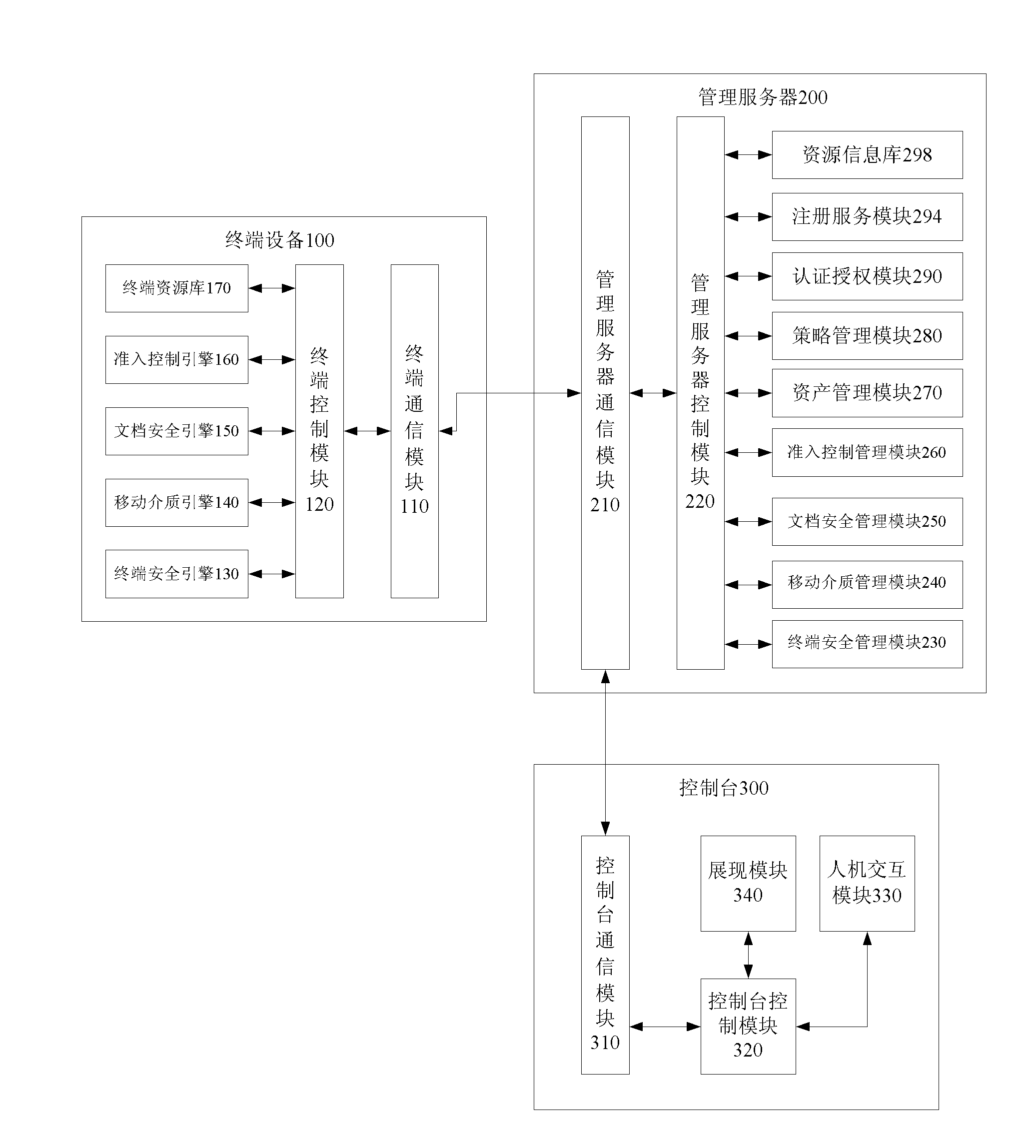Method for managing intranet security based on cooperative mode
A security management and intranet technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as large network traffic usage, impact on normal business systems, and restrictions on security management efficiency, so as to improve performance and efficiency. Avoid single point of failure and reduce network traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
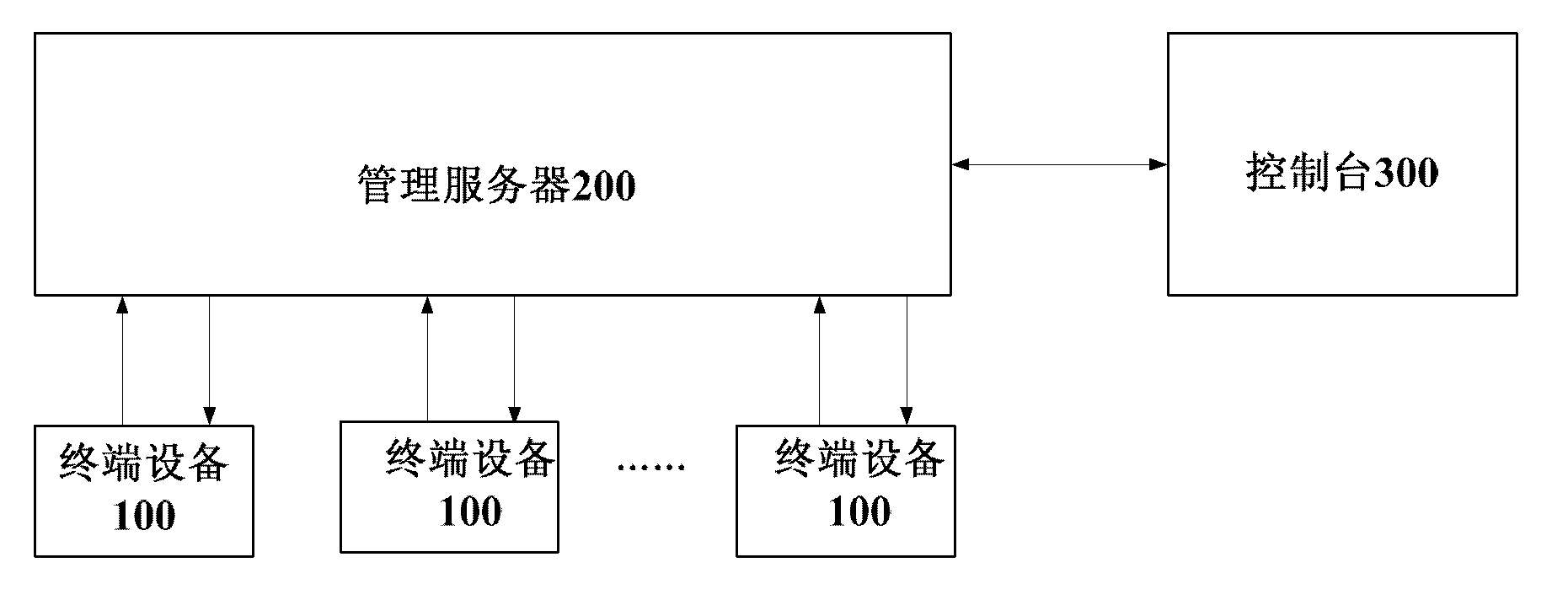
[0027] figure 1 It is a schematic diagram of the deployment of the intranet security management system, such as figure 1 As shown, the collaboration-based intranet security management system involved in the present invention includes: multiple terminal devices 100 , a management server 200 and a console 300 .
[0028] An agent program is installed on each terminal device 100 of multiple terminal devices, which can accept the security policy from the management server 200, and implement functions such as document security management, mobile media management, user behavior supervision, and data encryption and decryption according to the security policy. The security information is reported to the management server 200 . Specifically, the terminal device 100 has functions such as information collection, security policy execution, data encryption and decryption, document security management, mobile media supervision, and user behavior supervision by executing an agent program.
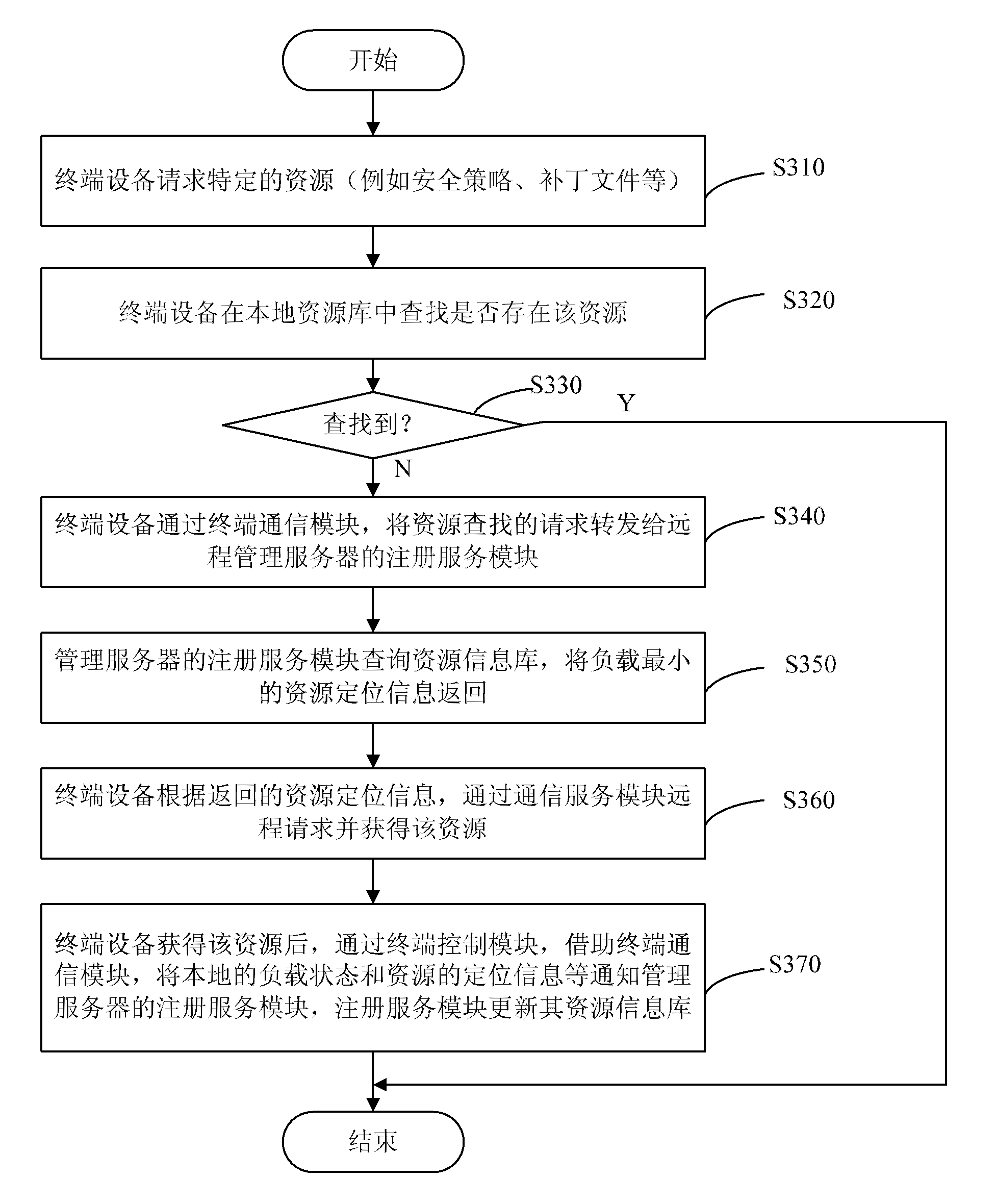
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com