Trusted Boot Method Based on Authentication Policy File and Hardware Information Collection
An authentication strategy and boot-up technology, applied in digital data authentication, computer security devices, instruments, etc., can solve the problems of fixed authentication process, lack of local authentication capabilities of terminal equipment, difficulty in meeting flexible and changeable authentication requirements, etc., to achieve guaranteed safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
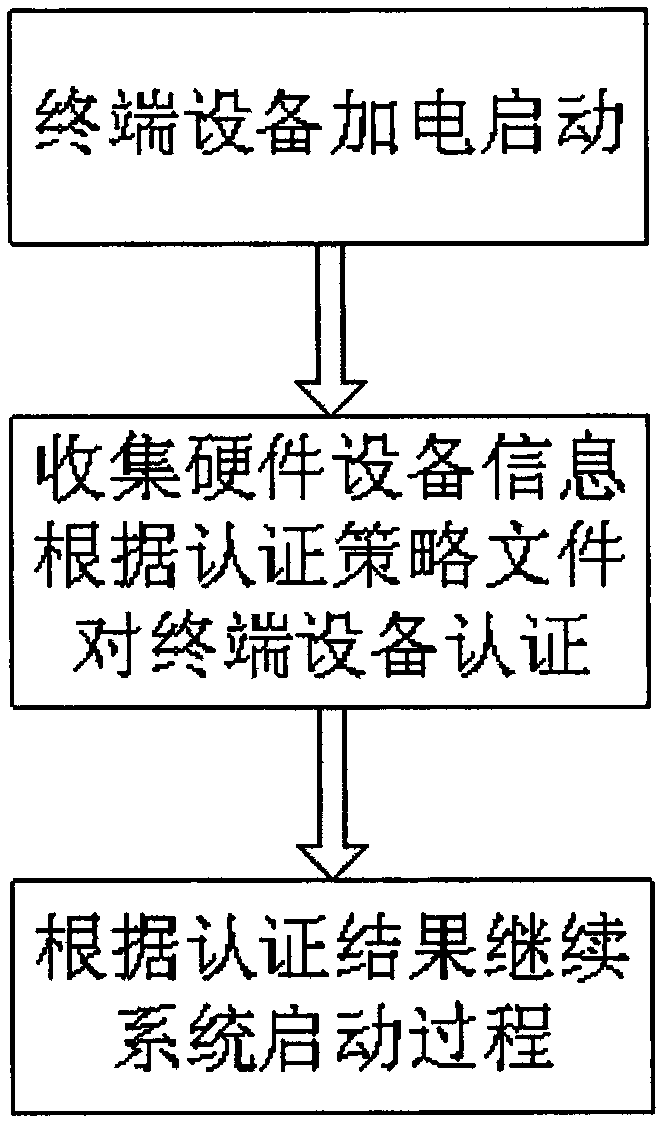
[0039] The invention is a credible booting method based on authentication policy files and hardware information collection. Configure authentication policy files for terminal devices in a trusted environment, and save them in the terminal security area. The verification value of the hardware device item, the specific process of a trusted boot is as follows:
[0040] (1) The terminal equipment is powered on and started, and the terminal equipment usually refers to a computer.
[0041] (2) Collect hardware device information, and authenticate the terminal device according to the configured authentication policy file. The authentication steps include:
[0042] 2.1) Read the authentication policy file, if there is no authentication policy file, go to step 2.7), if there is an authentication policy file, go to step 2.2).
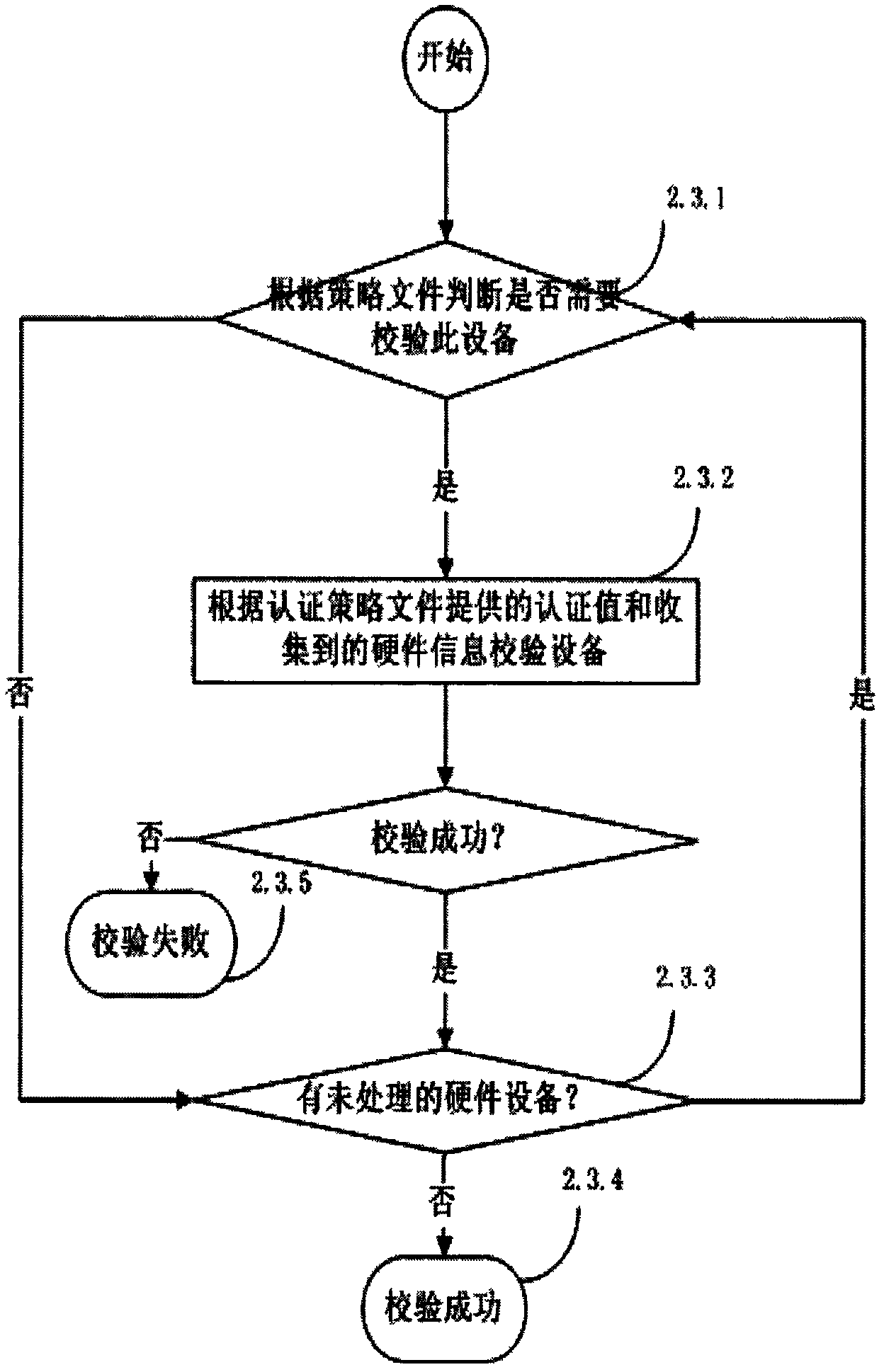
[0043] The authentication policy file is pre-configured, and the policy file specifies the hardware equipment items that the terminal needs to authenticate, th...
Embodiment 2
[0062] The trusted boot method based on authentication policy files and hardware information collection is the same as that in Embodiment 1.
[0063] The concrete realization of the present invention is described in conjunction with the specific development example under the linux operating system CentOS 5.3 (kernel version: 2.6.18).
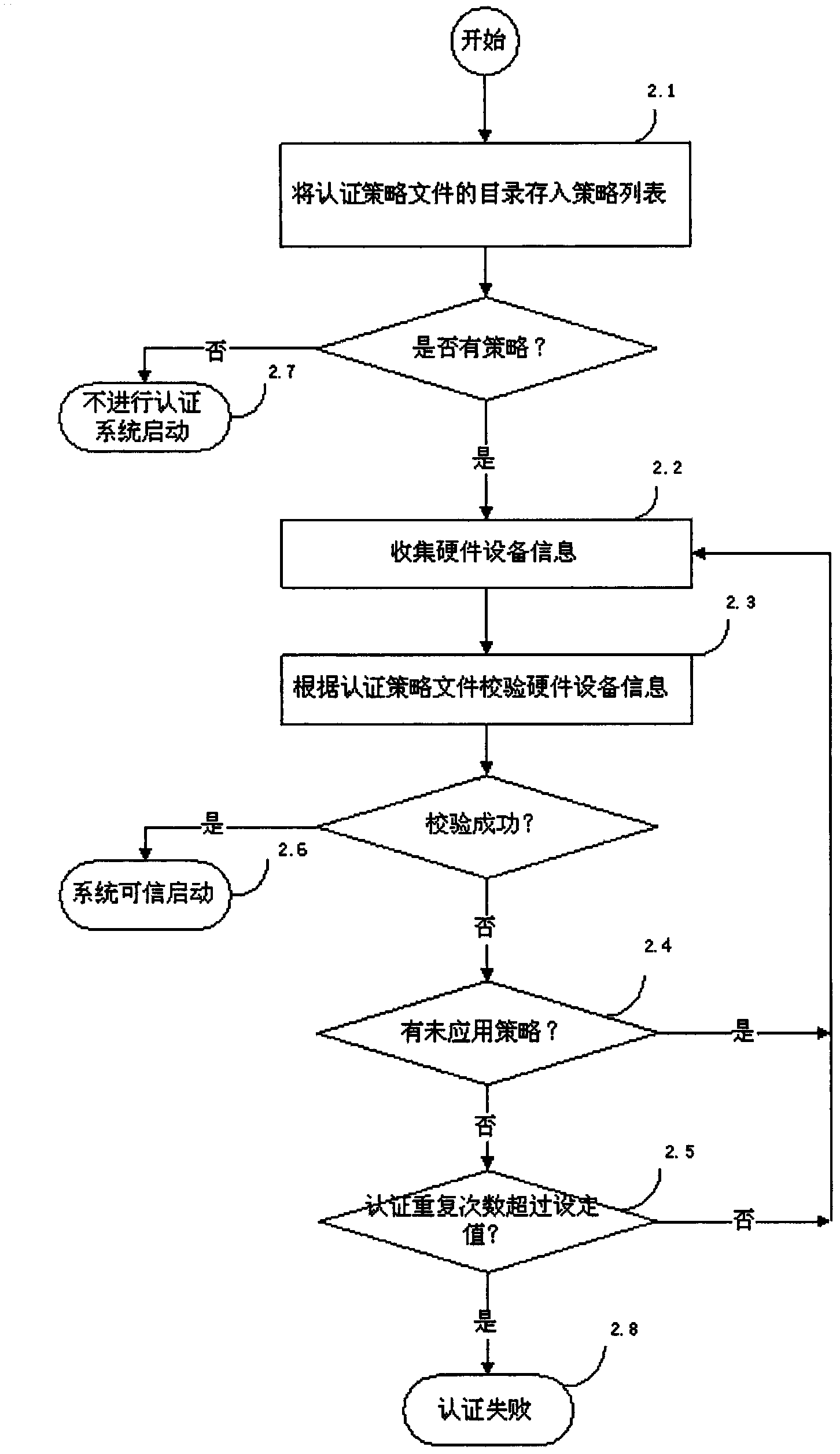
[0064] A specific terminal device authentication process is as follows: figure 2 As shown, the specific implementation is as follows:
[0065] 2.1) The authentication policy file is saved in / root / hw, read this file to obtain the authentication policy file, and store its directory address in the policy_dir_list of the policy file list, if there is no authentication policy file, go to step 2.7), if there is an authentication policy file Proceed to step 2.2).
[0066] 2.2) Collect hardware device information, respectively collect hardware device information of processor (CPU), PC, BIOS, motherboard (Motherboard), memory (MEM), USB, hard disk (H...
Embodiment 3
[0090] The trusted booting method based on authentication policy file and hardware information collection is the same as that in Embodiments 1 and 2.
[0091] The computer starts up with the correct hard disk, internal memory, and USB port removable storage device. After steps 2.1), 2.2), 2.3), and 2.6) the computer is authenticated successfully, and the operating system is trusted to start.
[0092] The computer uses the correct hard disk and memory and the wrong USB interface mobile storage device to start up. After steps 2.1), 2.2), 2.3), 2.4), and 2.5), the computer authentication fails, and the verification failure message is displayed: Lack of proper USB device .Consider change a correct one.
[0093] Operate according to the verification failure information: If the correct USB interface mobile storage device is replaced, the computer authentication is successful after steps 2.1), 2.2), 2.3), and 2.6), and the operating system can be trusted to start; if the correct USB ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com