Method, device and equipment for changing original installation information and detecting installation information
An original technology of installing information, applied in the computer field, can solve problems such as user loss and system attack, and achieve the effects of improving detection rate, simple implementation, and wide application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
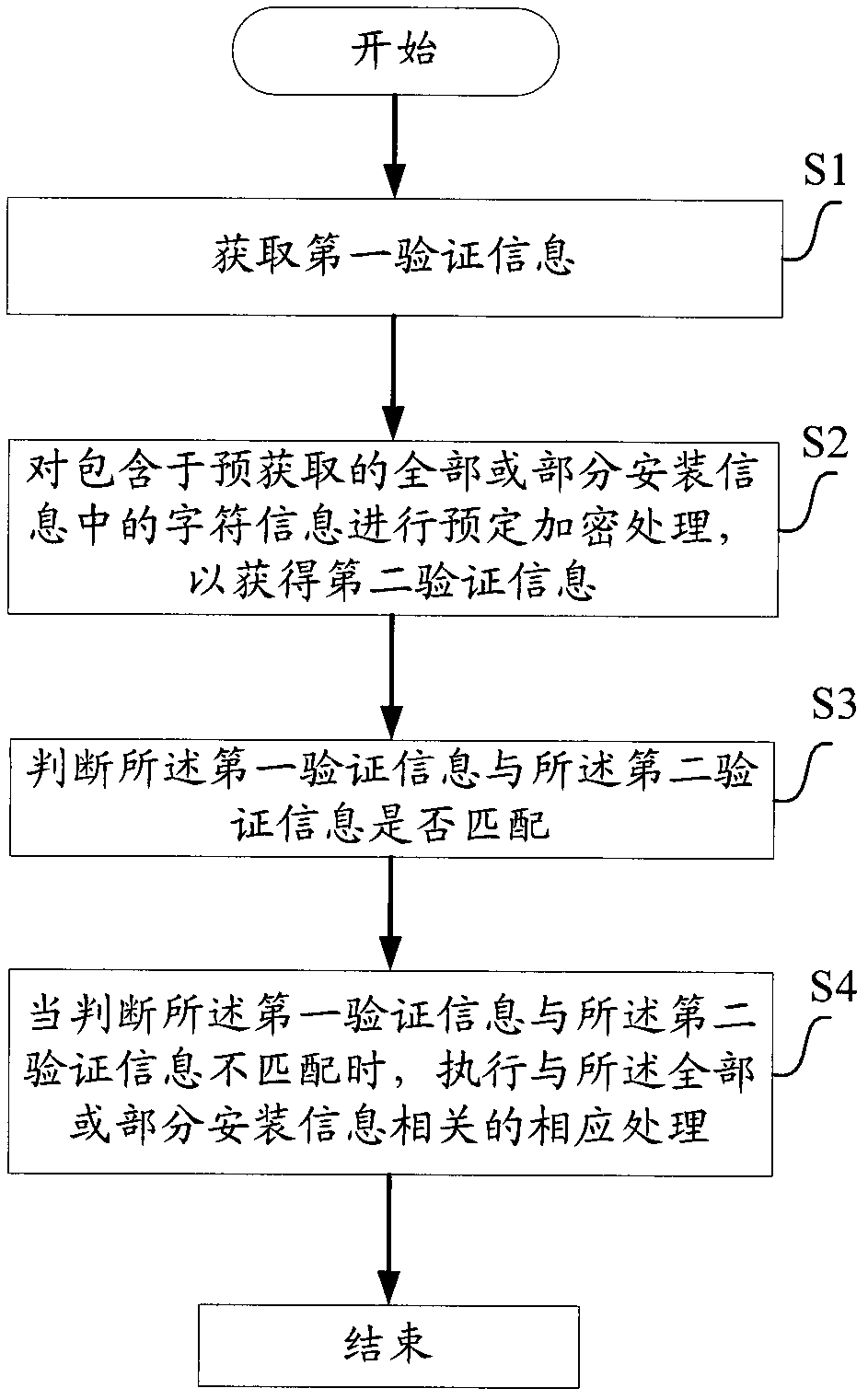
[0027] The present invention will be described in further detail below in conjunction with the accompanying drawings.
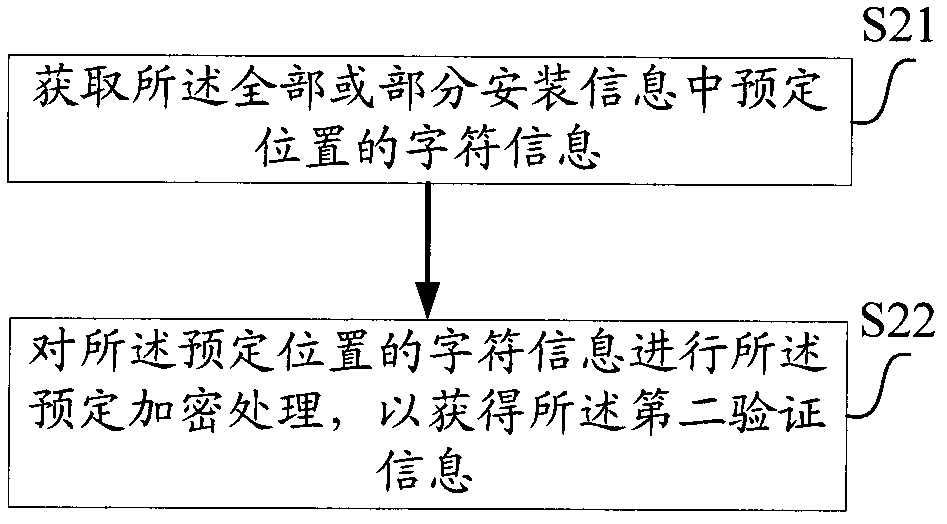
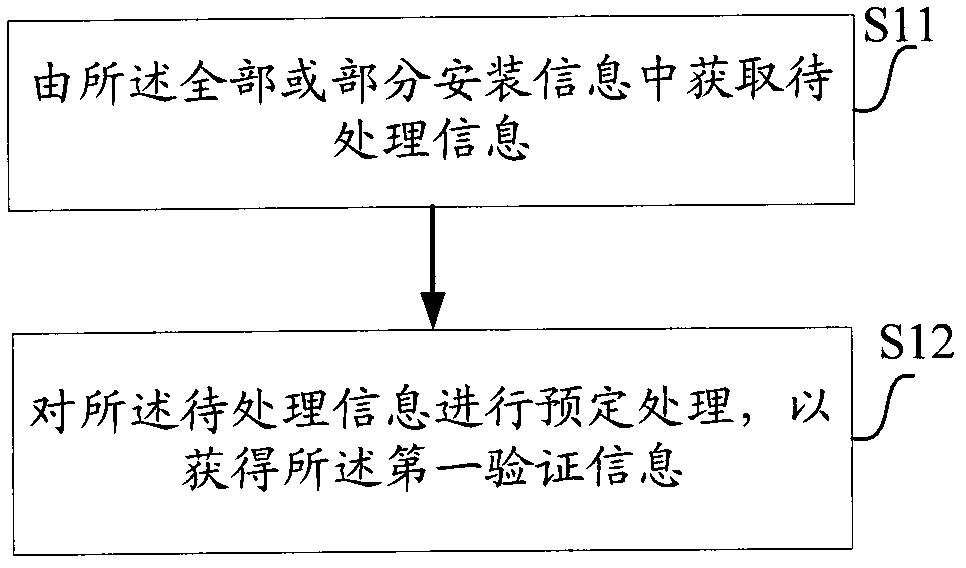
[0028] figure 1 A flowchart showing a method for detecting tampered installation information according to one aspect of the present invention. Among them, the method of adding verification information in the original installation information of the present invention is mainly realized by modifying the device; the method of detecting tampered installation information of the present invention is mainly realized by the detection device. This detection device includes but not limited to: 1) devices such as application modules, operating systems, processing controllers, etc. that have been installed in the first computer equipment and can implement the solutions of the present invention before performing the steps of the present invention; The installation information carried in and installed to the device in the first computer device. In the present invention, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com