Identity recognition method for computer system
A computer system and identification technology, applied in the computer field, can solve the problems of password security decline, loophole theft, etc., and achieve the effect of safe use permission requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
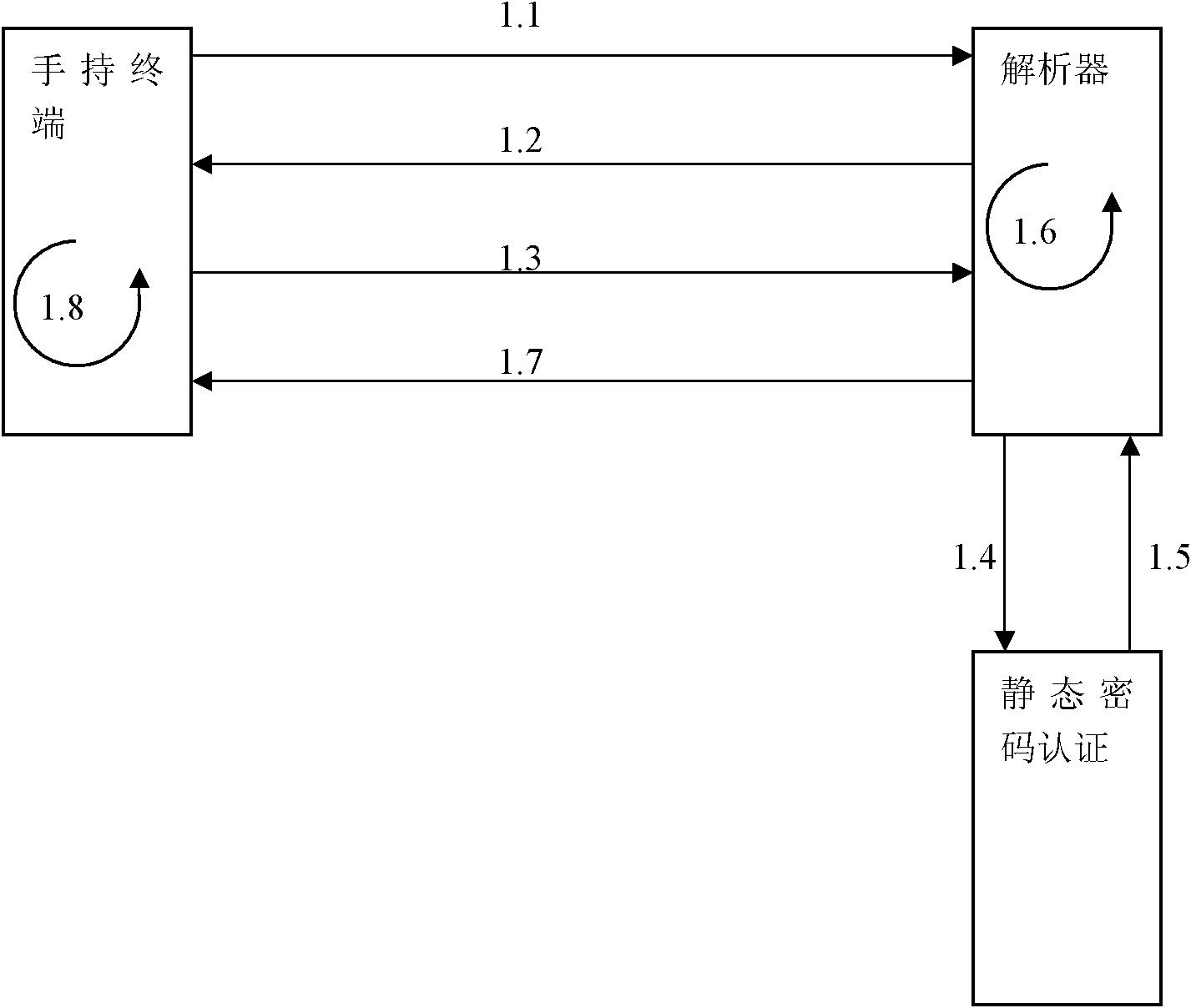
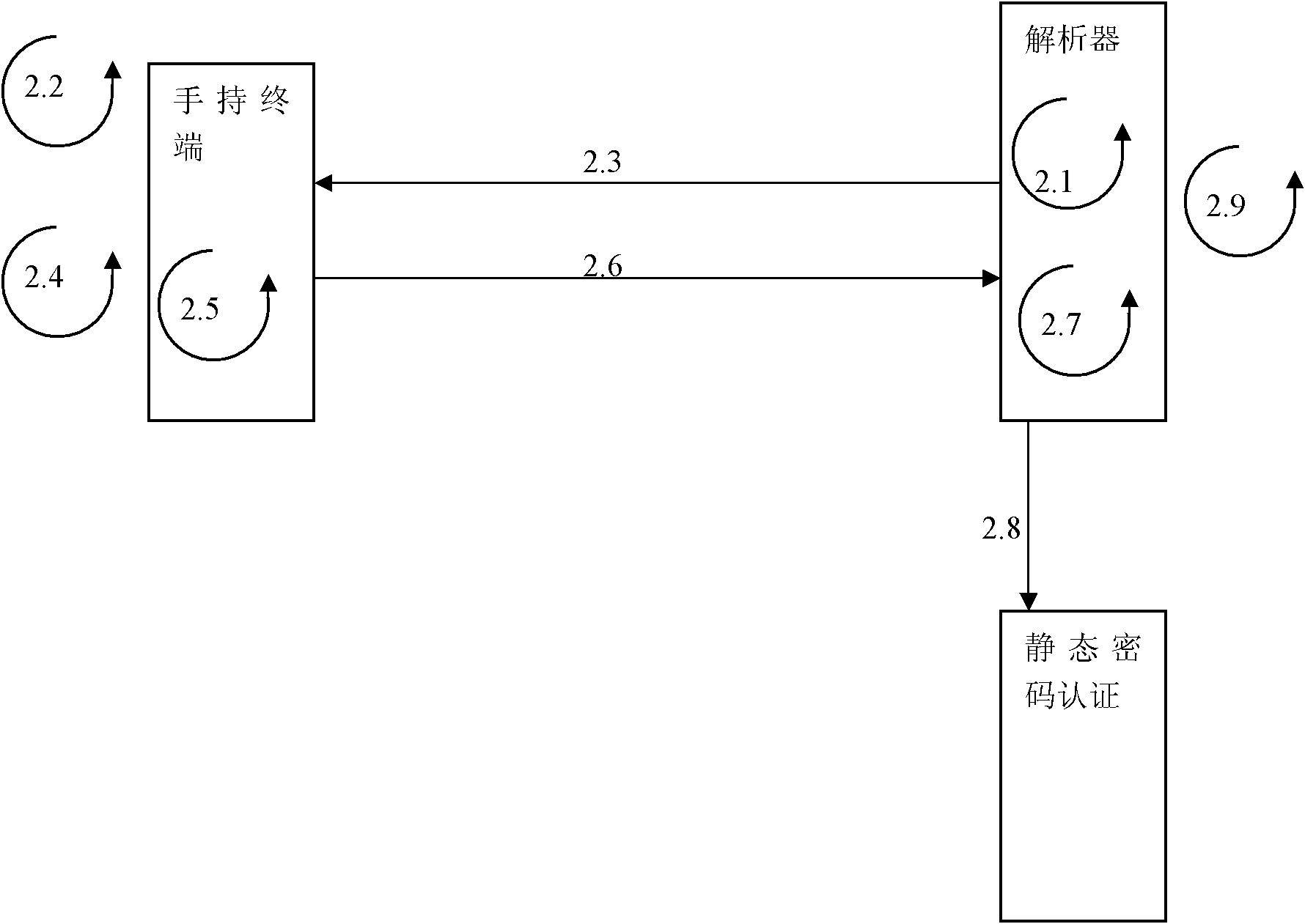
[0044] see Figure 1~4 .
[0045] The present invention comprises the following steps:
[0046] 1) Formulate an exchange protocol for encrypted information, write user information into a handheld terminal with a predetermined encryption and decryption mechanism, bind the handheld terminal to the system, establish a mapping between user information and the system host, and transfer the necessary Relevant information is stored in the system host and handheld terminal at the same time;
[0047] 2) The system host publicizes the first encrypted information, which includes the identity information of the system host;
[0048] 3) The handheld terminal obtains the first encrypted information, decrypts it using a predetermined decryption mechanism, obtains the identity information of the system host, searches for the corresponding user information according to the identity information of the system host, and encrypts the user information to become the second encrypted information; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com