Data backup method and device
A data backup and data update technology, applied in the field of data processing, can solve problems such as system logic errors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
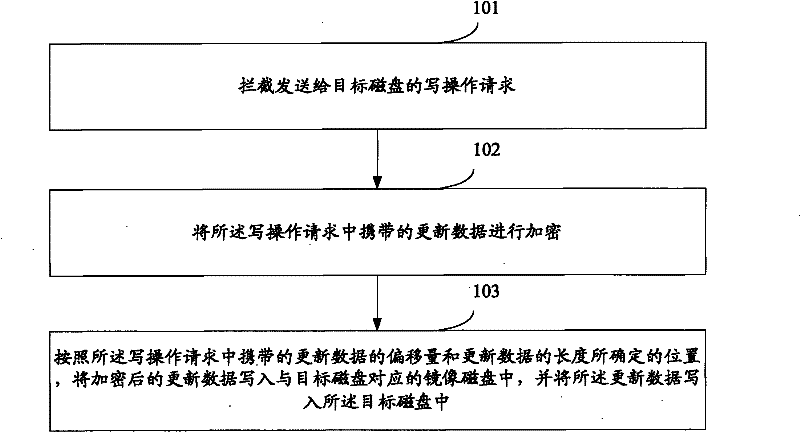
[0026] see figure 1 , which is a flowchart of an embodiment of a data backup method of the present invention, the method includes the following steps:
[0027] Step 101: intercepting the write operation request sent to the target disk;
[0028] Step 102: Encrypt the update data carried in the write operation request;
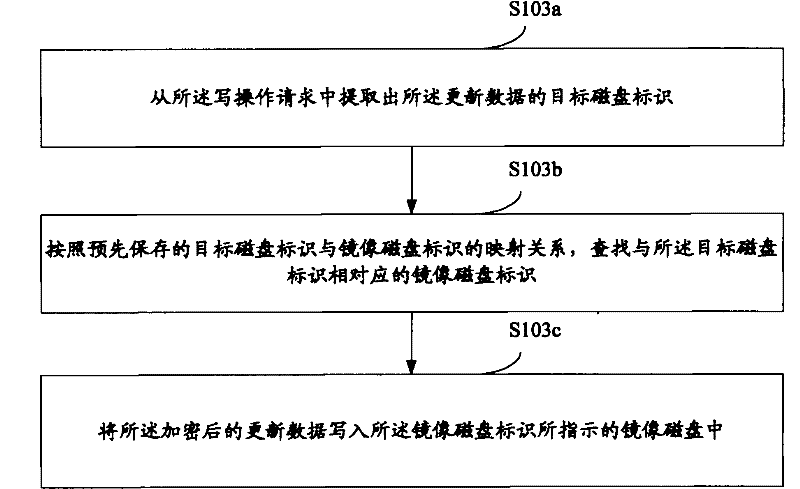
[0029] Step 103: According to the position determined by the offset of the update data carried in the write operation request and the length of the update data, write the encrypted update data into the mirror disk corresponding to the target disk, and write the updated Data is written into the target disk.
[0030] It can be seen from the above embodiments that when intercepting the write operation request sent to the target disk, the update data carried in the write operation request is encrypted, and when the offset and update data carried in the write operation request are used After the position determined by the length of the target disk, on the one hand...
Embodiment 3
[0047] see Figure 5 , which is a flowchart of another embodiment of a data backup method of the present invention, the method includes the following steps:
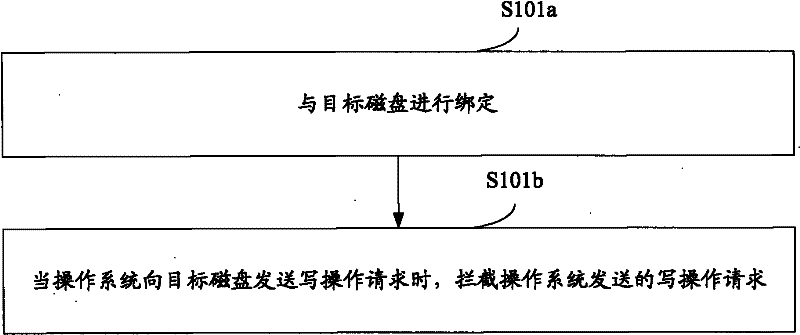
[0048] Step 501: Intercept the write operation request sent by the operating system to the target disk;
[0049] Step 502: Determine whether the target disk has a corresponding mirror disk, if yes, go to step 503, if not, go to step 505;
[0050] For example, a registry entry may be created, in which it is indicated whether each target disk has a corresponding mirror disk. Alternatively, it is also possible to determine whether the target disk has a corresponding mirror disk according to the registry entries that store the mapping relationship between each target disk identifier and the mirror disk identifier described in Embodiment 1. If the target disk identifier has a corresponding If there is no mapped mirror disk ID, it is determined that the target disk indicated by the target disk ID has a corresponding mirror d...
Embodiment 4
[0058] see Figure 6 , which is a flowchart of another embodiment of a data backup method of the present invention, the method includes the following steps:
[0059] Step 601: Intercept the write operation request sent to the target disk;
[0060] Step 602: Determine whether the user who is currently backing up the data currently has the authority to update the backup data in the mirrored disk, if yes, go to step 603, if not, end the process;
[0061] Wherein, judging whether the user currently has the right to update the backup data in the mirror disk includes: judging whether the user has the right to update the backup data in the mirror disk, and if so, further judging whether the user has the right to update the backup data in the mirror disk at the current moment. If there is permission to update the backup data in the disk, go to step 603; otherwise, end the process.
[0062] For example, a permission information table can be created, which includes whether each user h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com