Method and system for safely guiding operating system of user
An operating system and secure boot technology, applied in the field of information security, can solve the problems of insufficient security, easy to be cracked, and insufficient security for users, and achieve the effect of ensuring secure boot.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in detail below through specific implementation examples in conjunction with the accompanying drawings.
[0021] Such as figure 1 , which is a schematic diagram of the normal computer startup process.
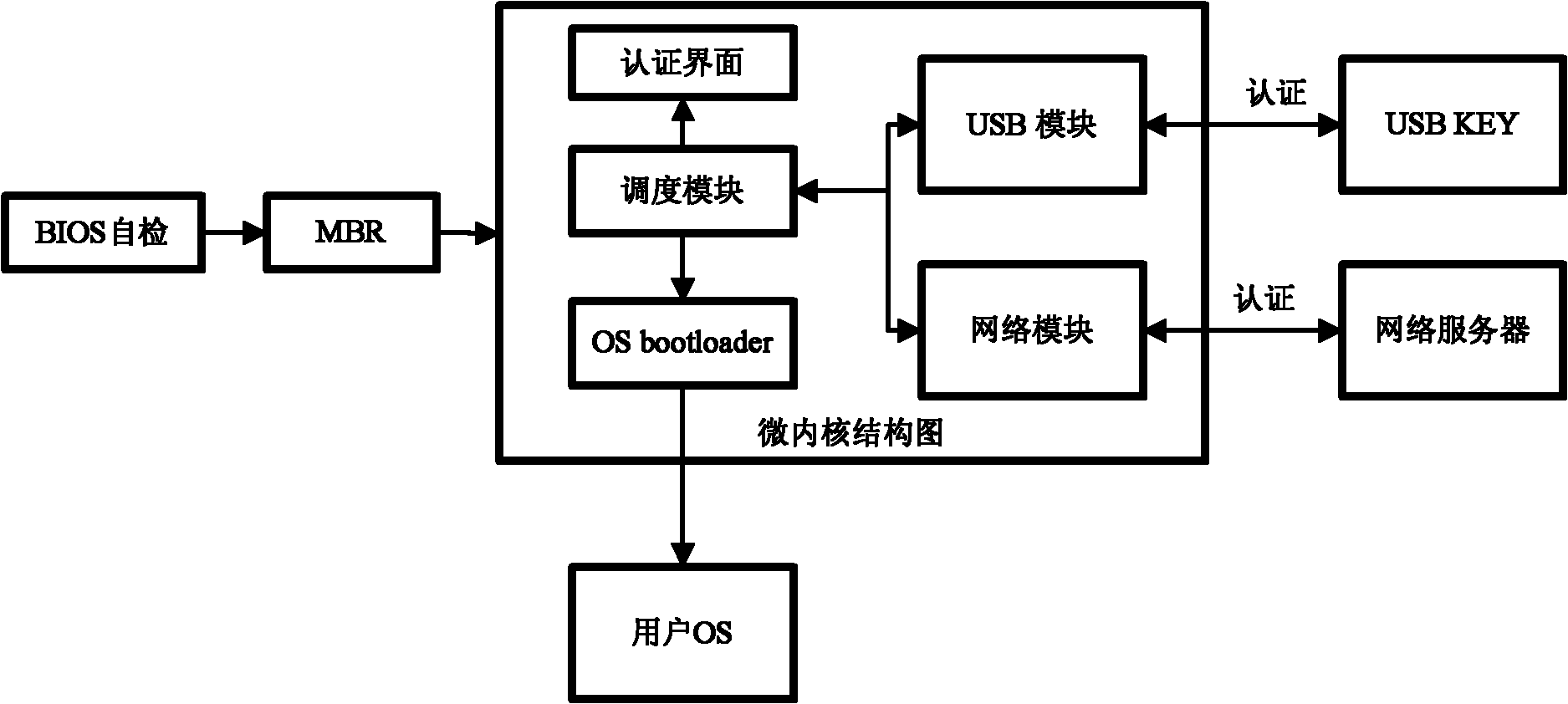
[0022] Such as figure 2 , is a schematic diagram of the startup process of the computer used in the present invention. It is different from the normal one in that the microkernel is run before the user's operating system is guided, and the authentication operation is performed. After the authentication is successful, the user's operating system is then guided.
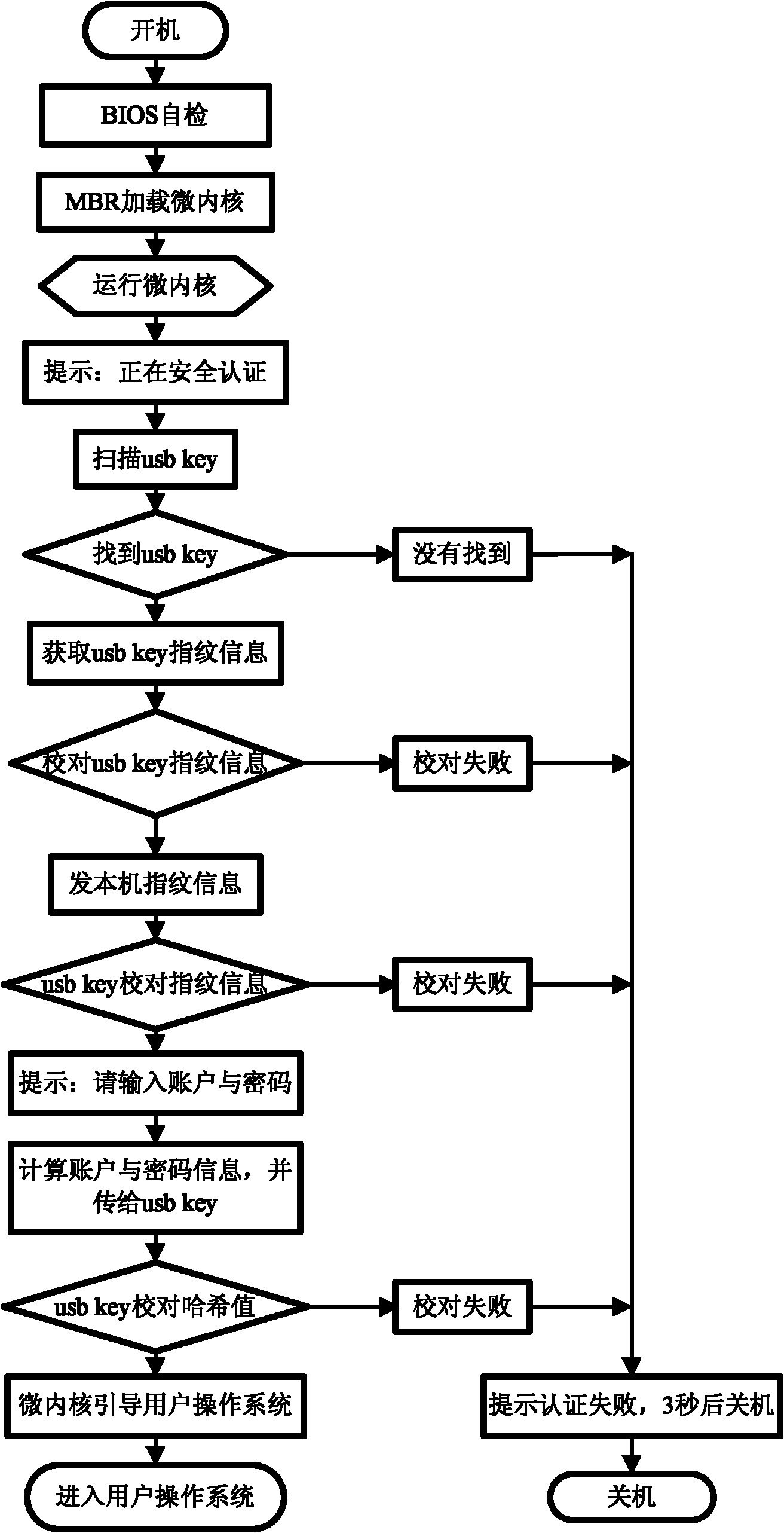
[0023] According to different authentication devices, it is divided into network server authentication version and usb key authentication version. For detailed workflow, see image 3 (usb key authentication version) and Figure 4 (web server certified version). The working process is described in detail below.
[0024] The installation process steps are as follows:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com