Security level authentication method and system
A technology of security level and security verification, applied in transmission system, image communication, selective content distribution, etc., can solve problems such as inability to uniformly manage third-party systems, business systems without unified definition, and domain security, etc., to achieve system Unified management, reduced workload, and easy integration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
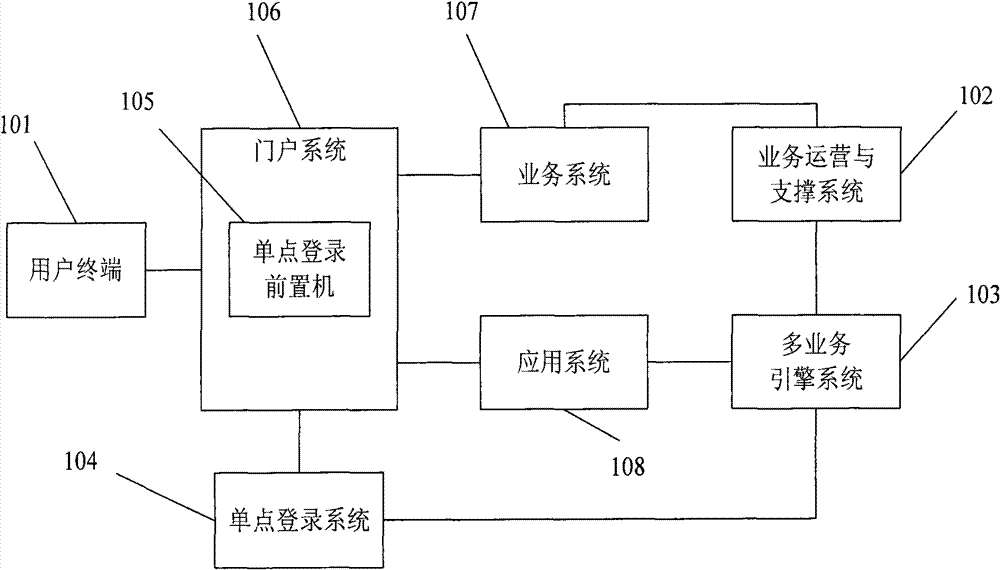
[0050] figure 1 It is a system structure diagram of security level authentication in the specific embodiment of the present invention. like figure 1 As shown, the security level authentication system includes a user terminal 101, a business operation and support system 102, a multi-service engine system 103, a single sign-on system 104, a single sign-on front-end processor 105, a portal system 106, a business system 107 and an application system 108.
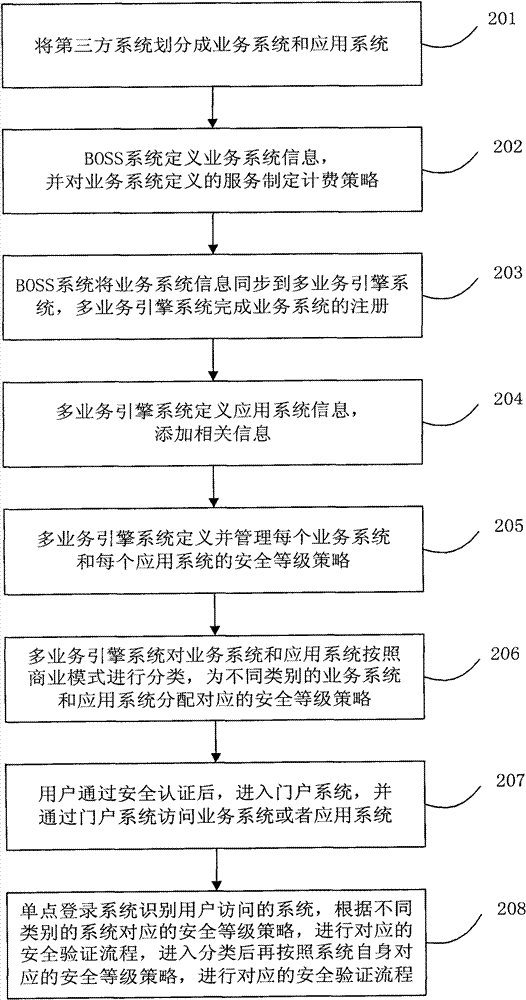
[0051]The user terminal accesses the business system or application system through the portal system, the business operation and support system defines the business system information, formulates the billing policy for the services defined by the business system, and synchronizes the business system information to the multi-service engine system, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com