Anti-theft system and method for data card
A data card and data technology, applied in the field of communication, can solve the problem of data card being stolen, and achieve the effect of preventing theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
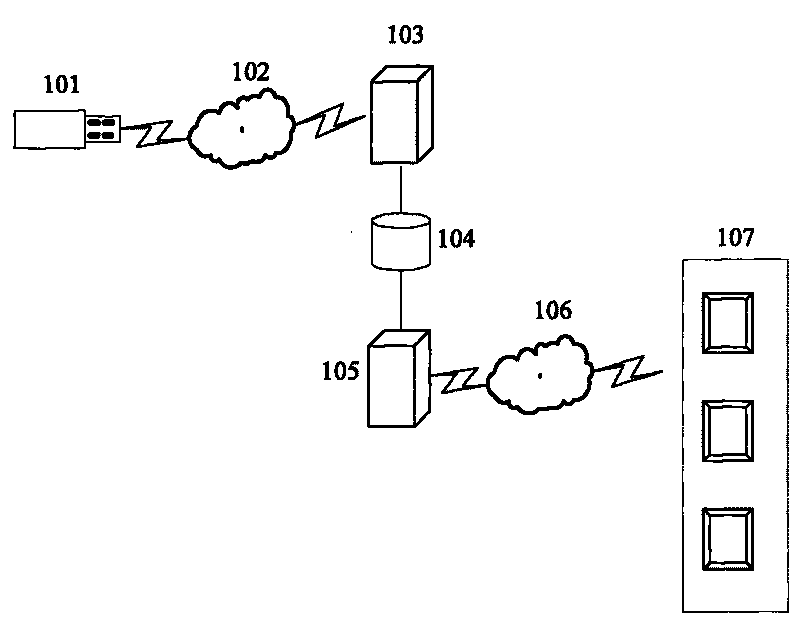
[0042] figure 1 Shown is a schematic view of the use environment of the data card anti-theft system in Embodiment 1 of the present invention, including a data card 101, a wireless network 102, an identity authentication server 103, a database 104, a user information maintenance server 105, a wired or wireless network 106, and Various terminals 107 that can access the Internet.
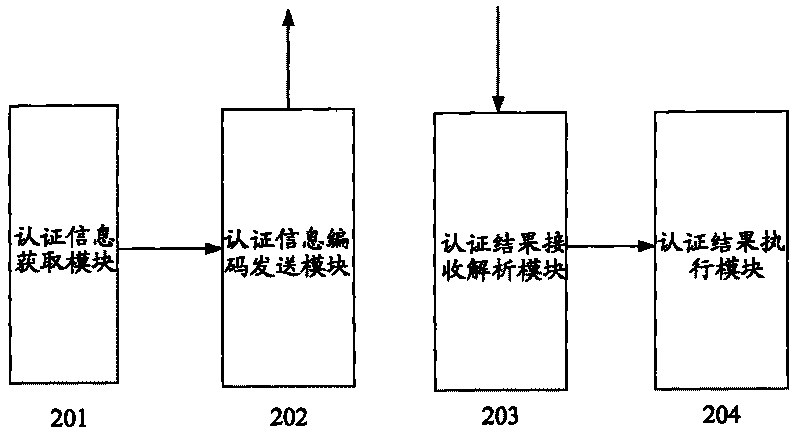
[0043] figure 2 Shown is a schematic structural diagram of the terminal side of the data card anti-theft system according to Embodiment 1 of the present invention. The terminal side mainly includes four functional modules: an authentication information acquisition module 101, an authentication information encoding sending module 102, an authentication result receiving and analyzing module 103, The authentication result execution module 104 .
[0044] The authentication information acquisition module 201 is used to obtain the authentication information of the data card currently used, which can inclu...
Embodiment 2
[0056] Figure 7 It is a flow chart of the user information maintenance server side of the data card anti-theft system according to Embodiment 2 of the present invention. Further explanations are given below according to the illustrations:
[0057] The first step is to obtain user login information (step 701), determine whether the user exists (step 702), if not, prompt the user whether to register a new user (step 703), if the user selects no, then exit (step 704), if The user selects registration, then registers new user, prompts the user to bind data card information and SIM card information (step 706), then updates to database (step 707), if the user already exists, then enters user function selection interface (step 705), Judge the service selected by the user (step 708), if the user chooses to report the loss of the data card, then update the status of the data card under the user name to report the loss (step 709), and update the data in the database (step 710). If the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com