Method and system for implementing trigger of intermediate charge
An intermediate charging and implementation method technology, applied in the field of communication, can solve the problem that there is no trigger intermediate charging, cannot meet the diversified requirements of triggering intermediate charging, and cannot effectively and flexibly realize the triggering and reporting of intermediate charging, etc. problem, to achieve the effect of control flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 3
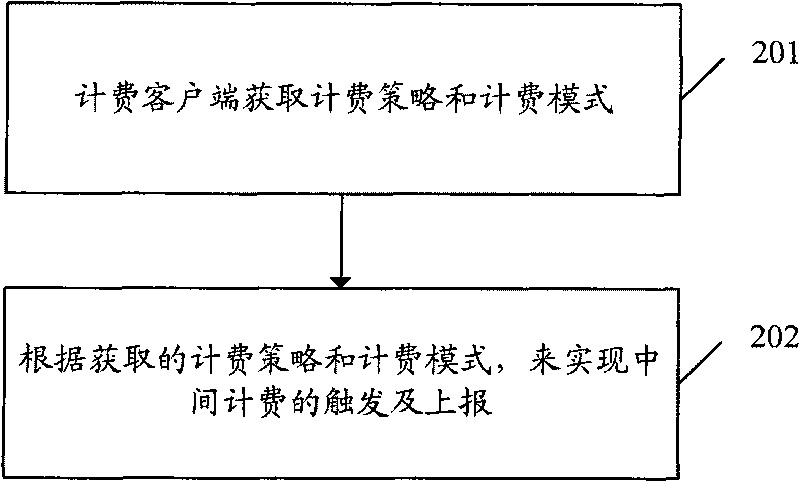
[0099] The third embodiment is: the current billing strategy is specifically based on the billing mode based on data flow, and the current billing strategy is specifically based on the billing strategy based on the time interval plus traffic interval, and different data streams are based on their respective time intervals plus traffic intervals To trigger intermediate charging, this method embodiment includes the following steps:
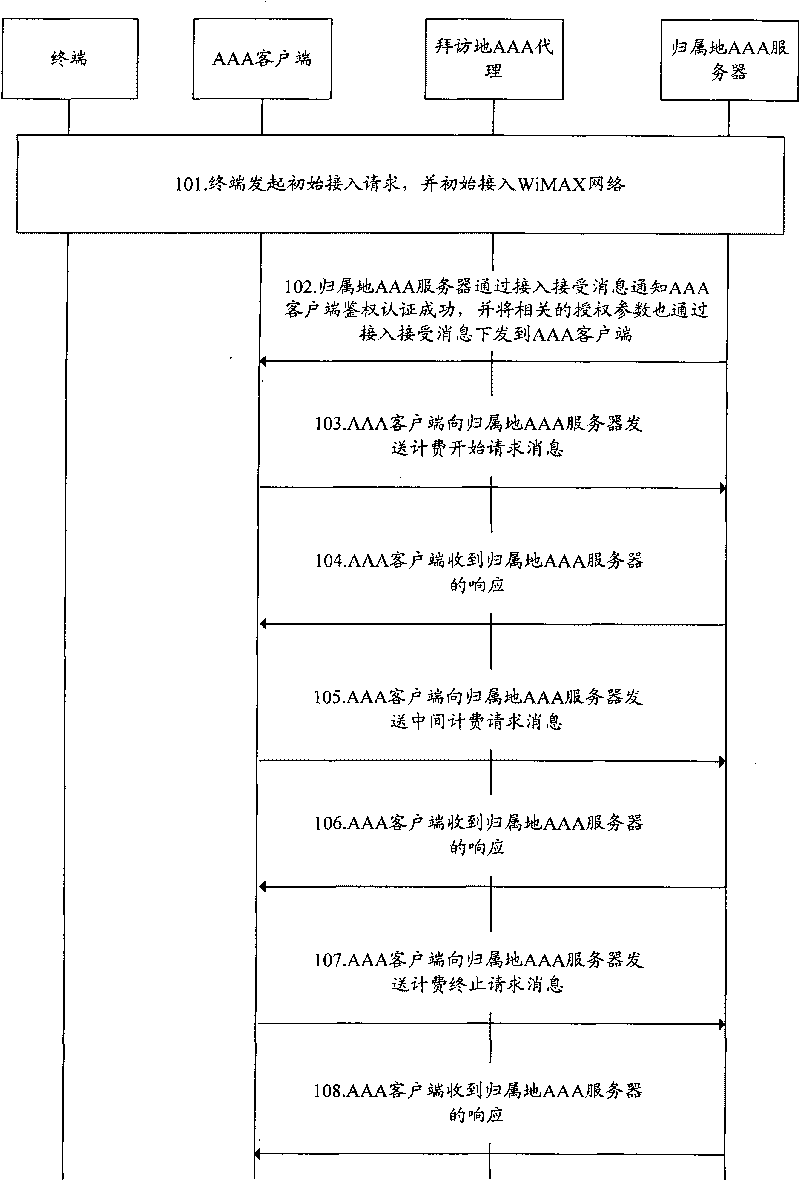
[0100] Step 501, the terminal enters the WiMAX network, the terminal initiates an initial access request, and initially accesses the WiMAX network.
[0101] Step 502: After the initial access authentication is successful, the home AAA server notifies the AAA client of successful authentication through a Radius-type access acceptance message, and sends relevant authorization parameters to the AAA client through an access acceptance message end.
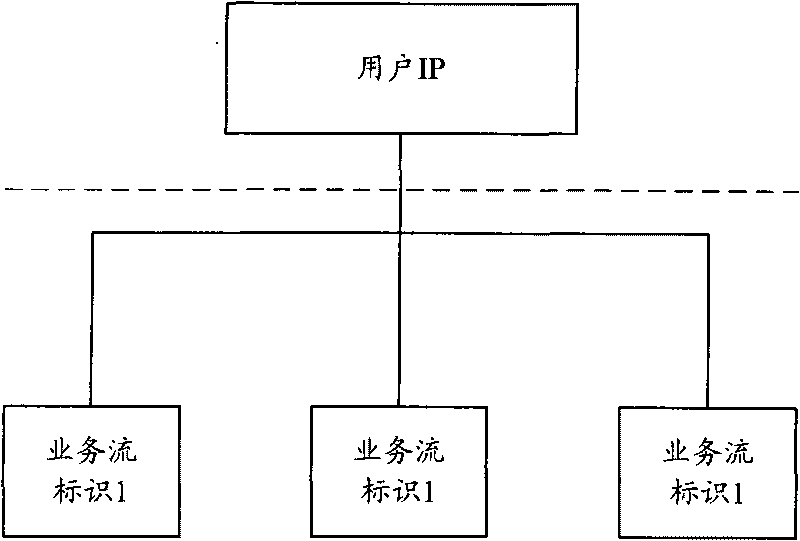
[0102] Here, the relevant authorization parameters are mainly: the billing mode is based on the data str...
Embodiment 4
[0110] Embodiment 4 is: the current billing strategy is specifically a billing mode based on data flow, and the current billing strategy is specifically a billing strategy based on traffic interval / duration interval / duration interval plus traffic interval, and different data streams are based on their respective The traffic interval / duration interval / duration interval plus the traffic interval triggers intermediate billing. This embodiment of the method includes the following steps:
[0111] Step 601, the terminal enters the WiMAX network, the terminal initiates an initial access request, and initially accesses the WiMAX network.
[0112] Step 602: After the initial access authentication is successful, the home AAA server notifies the AAA client of successful authentication through a Radius-type access acceptance message, and sends relevant authorization parameters to the AAA client through an access acceptance message end.
[0113] Here, the relevant authorization parameters...
Embodiment 5
[0121] Embodiment 5 is: the current billing policy is specifically the billing mode based on the IP session, and when the current billing policy is specifically the billing policy based on the traffic interval, intermediate billing is triggered based on the traffic interval. This embodiment of the method includes the following steps :
[0122] Step 701, the terminal enters the WiMAX network, the terminal initiates an initial access request, and initially accesses the WiMAX network.
[0123] Step 702: After the initial access authentication succeeds, the home AAA server notifies the AAA client of successful authentication through a Radius-type access acceptance message, and sends relevant authorization parameters to the AAA client through an access acceptance message end.
[0124] Here, the relevant authorization parameters mainly include: the charging mode is based on IP session, and the fields of charging policy based on traffic interval.
[0125] Step 703 , the accounting ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com