Safety JTAG module and method for protecting safety of information inside chip
A safe and secure configuration technology, applied in computer security devices, internal/peripheral computer component protection, instruments, etc., can solve the problem of not being able to access the content that user B can access, inconvenient for personalized distribution and multi-party development, and JTAG port protection measures failure and other problems, to achieve personalized management, avoid the risk of failure, and ensure the effect of safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] Specific embodiments of the present invention will be described below in conjunction with the accompanying drawings.
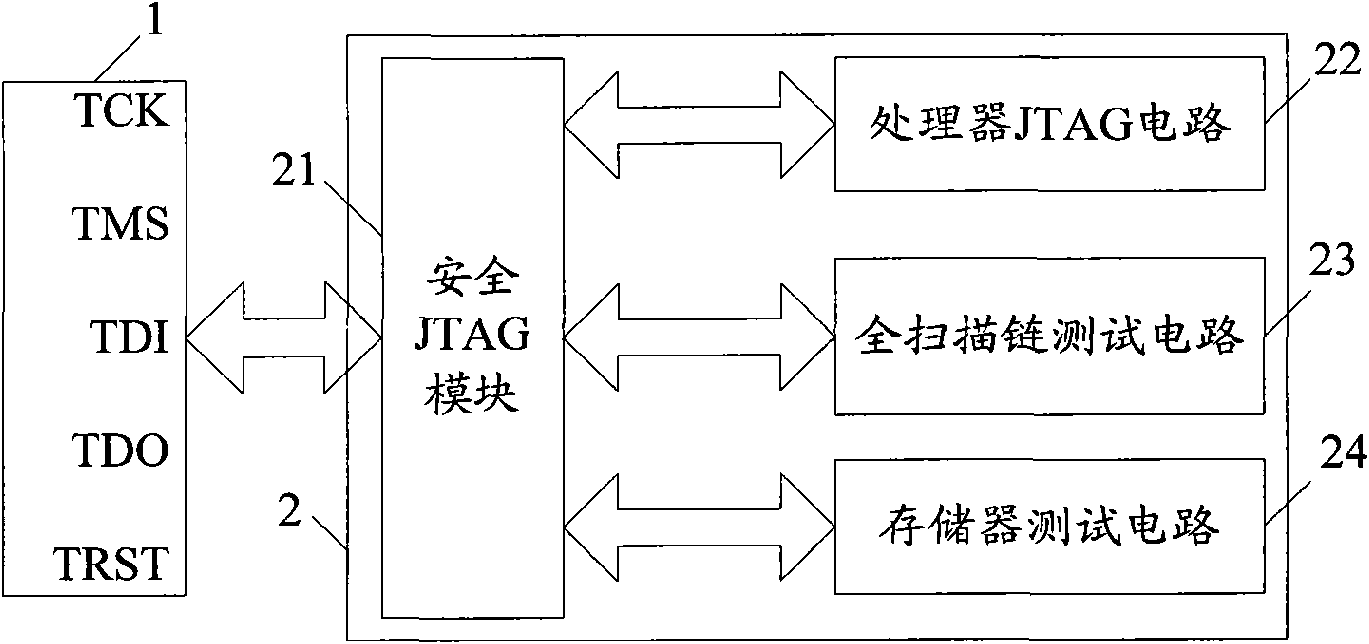
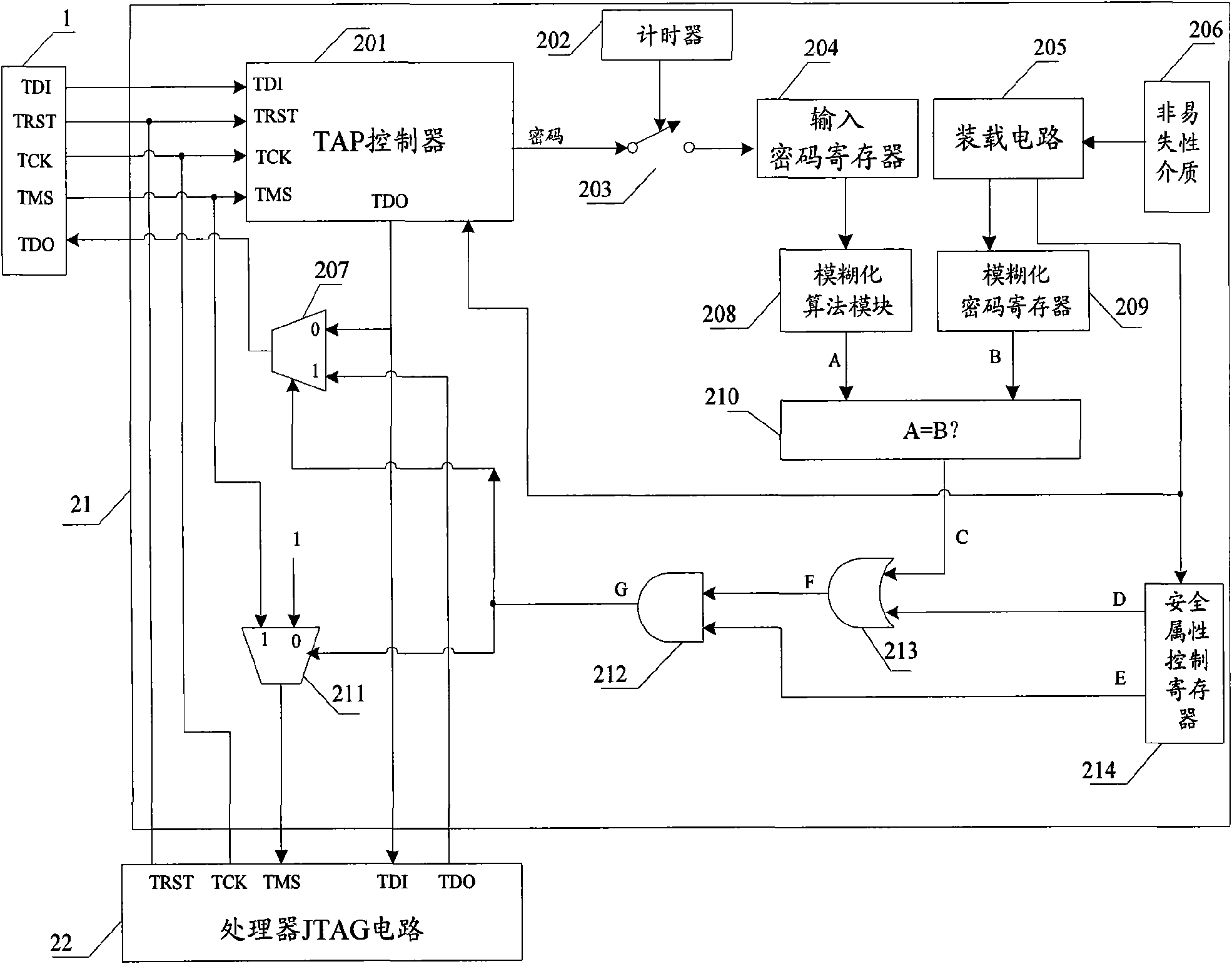
[0046] figure 1 It is a schematic diagram of the internal structure of the system chip disclosed in the present invention. A system on chip (System on Chip, SOC) 2 includes: a security JTAG (Join Test Action Group) module 21 , a processor JTAG circuit 22 , a full scan chain test circuit 23 and a memory test circuit 24 . Processor JTAG circuit 22, full scan chain test circuit 23 and memory test circuit 24 are the object (abbreviation protection object) that system chip 2 is protected by safety JTAG module 21, only through the safety permission of safety JTAG module 21, the user just can pass through JTAG port 1 accessing or starting the protection object, and realizing the test or debugging of the system chip 2 . Therefore, the present invention focuses on describing how the security JTAG module 21 implements security control on the processor JTAG circ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com