Method and system for security protection monitoring for mobile multimedia
A mobile multimedia and security monitoring technology, applied in closed-circuit television systems, instruments, alarms, etc., can solve the problems of high complexity, incomplete and insufficient security and privacy protection, etc., to reduce processing computing resources and reduce coding and decoding. The effect of delay and low bandwidth
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. The method for multi-code stream mobile multimedia security monitoring of the present invention comprises the following steps:
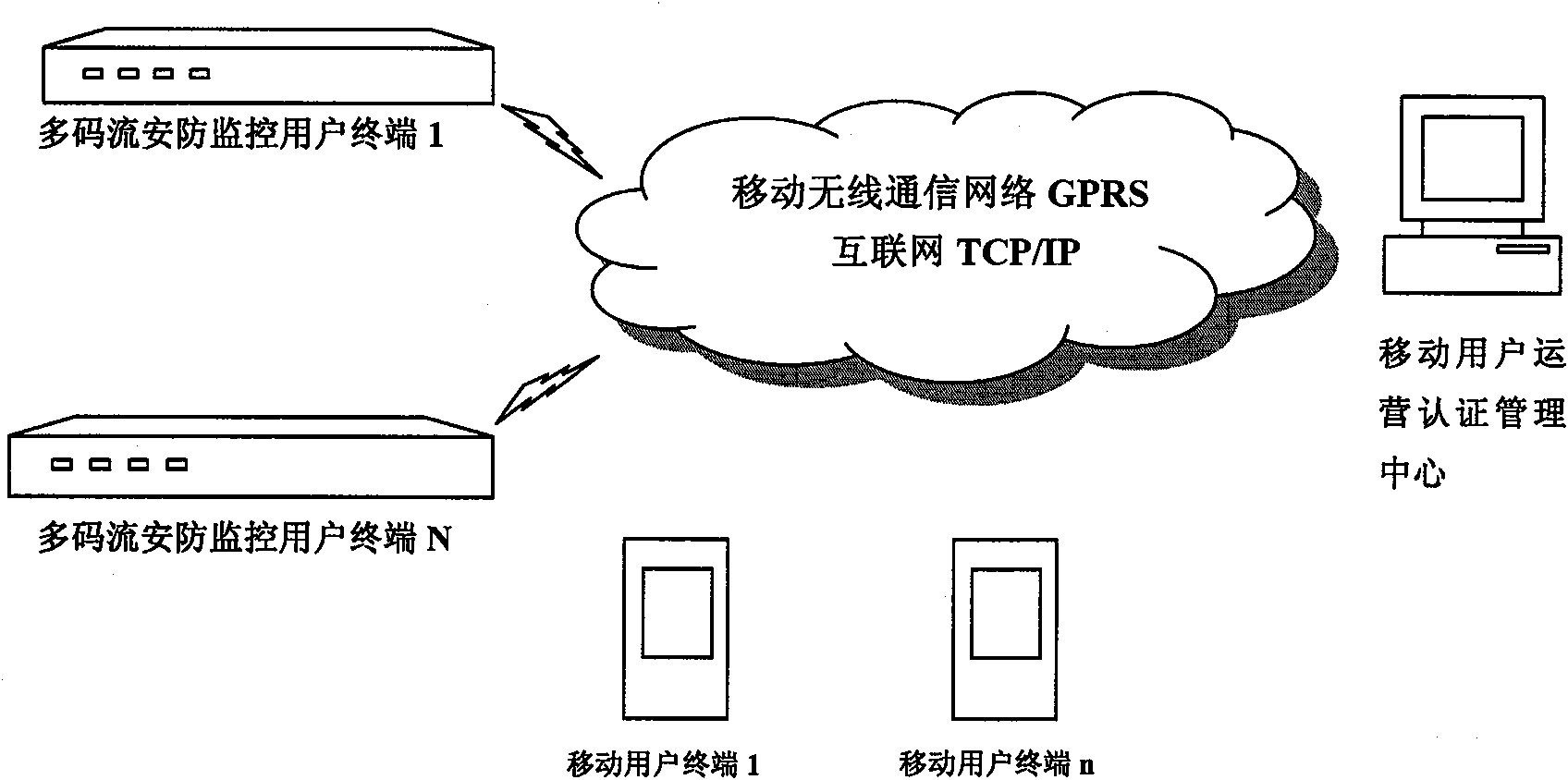
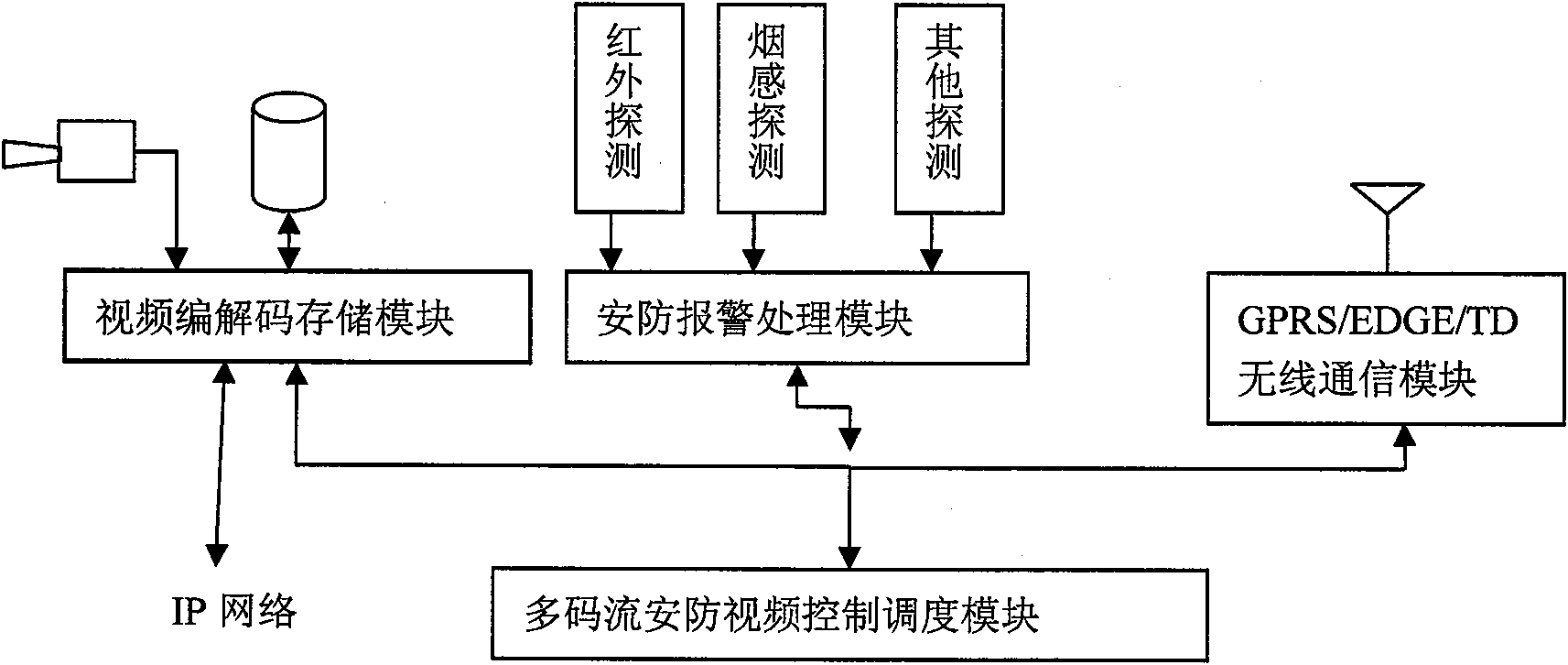
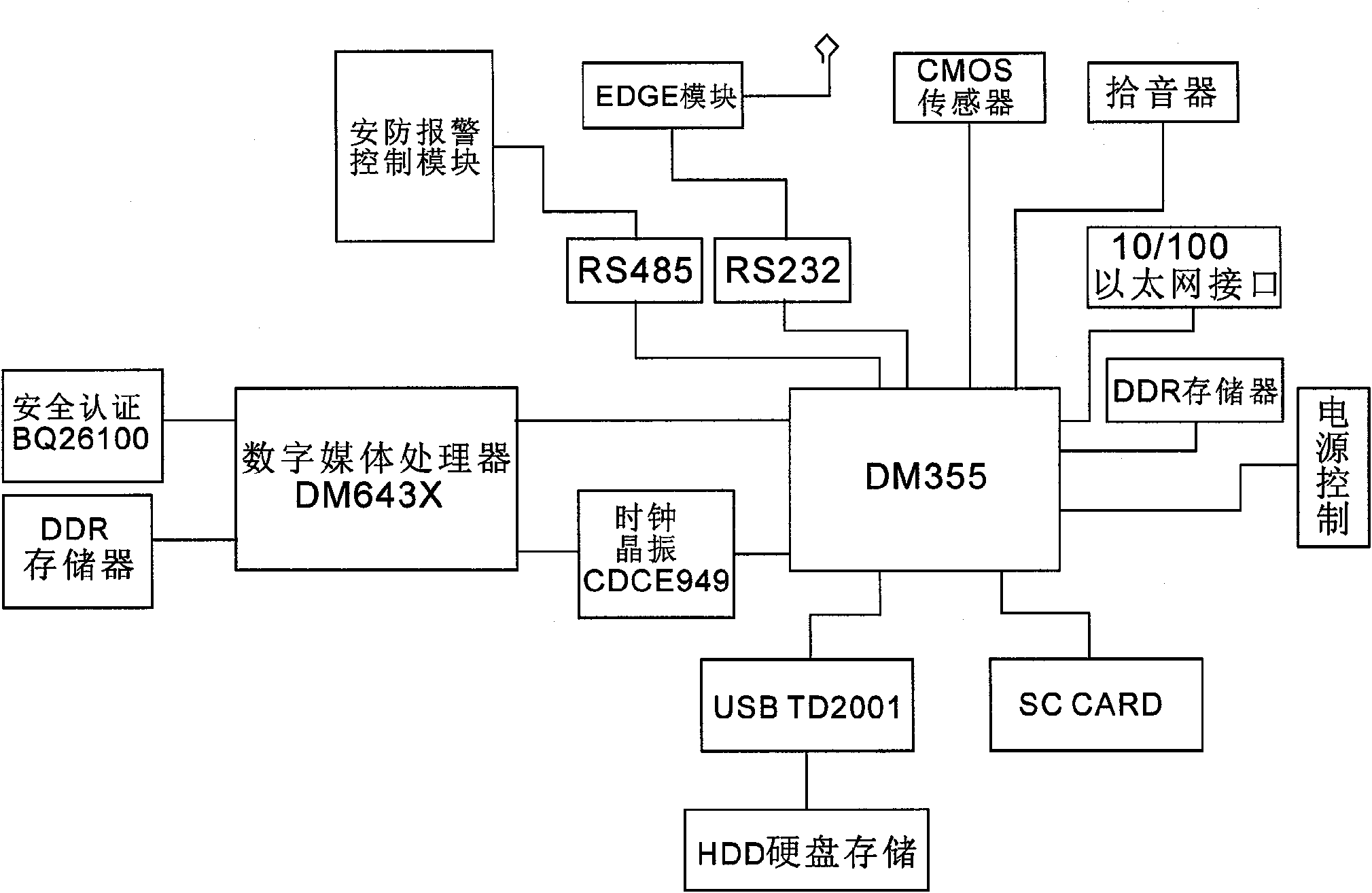
[0019] One, such as figure 1 As shown, more than one multi-stream security monitoring user terminal, more than one mobile user terminal of the user terminal, and a mobile user operation authentication management center are set. The multi-stream security monitoring terminal, mobile user terminal and mobile user operation authentication management center use the mobile wireless communication network GPRS / EDGE / TD or the Internet TCP / IP to network to form a mobile multimedia security monitoring network system. Such as figure 2 As shown, the multi-stream security monitoring user terminal is equipped with a security alarm processing module, which is connected to the multi-stream security video control dispatching module, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com