Method for enhancing the trapping capability of honeynet and honeynet system
A honeynet and strength technology, applied in transmission systems, electrical components, etc., can solve the problem of high decoy in the honeynet system, and achieve the effect of increasing authenticity and interactivity, and improving deception.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
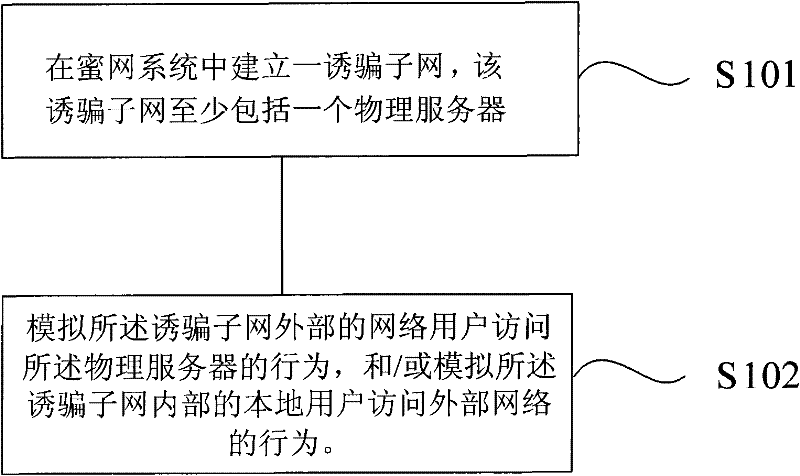
[0028] like figure 1 Shown is a flow chart of a method for enhancing honeynet deception provided by Embodiment 1 of the present invention. The method includes:
[0029] S101: Establish a decoy subnet in the honeynet system. The decoy subnet is the main part used to lure the attacker to attack it. The attacker is most interested in various types of servers. Therefore, in this embodiment, The decoy subnet includes at least one physical server. Of course, the more types of servers, the higher the decoy strength. In this embodiment, the server adopts a real physical server, which can make the decoy subnet look more authentic, thereby improving the decoy strength of the decoy subnet. The physical server can be an FTP server, HTTP server, WEB server, mail server etc. In this embodiment, the honeypot host and the physical server may be connected through a hub, router or switch.
[0030] As an embodiment of the present invention, a honeypot host can also be set in the decoy subnet,...
Embodiment 2
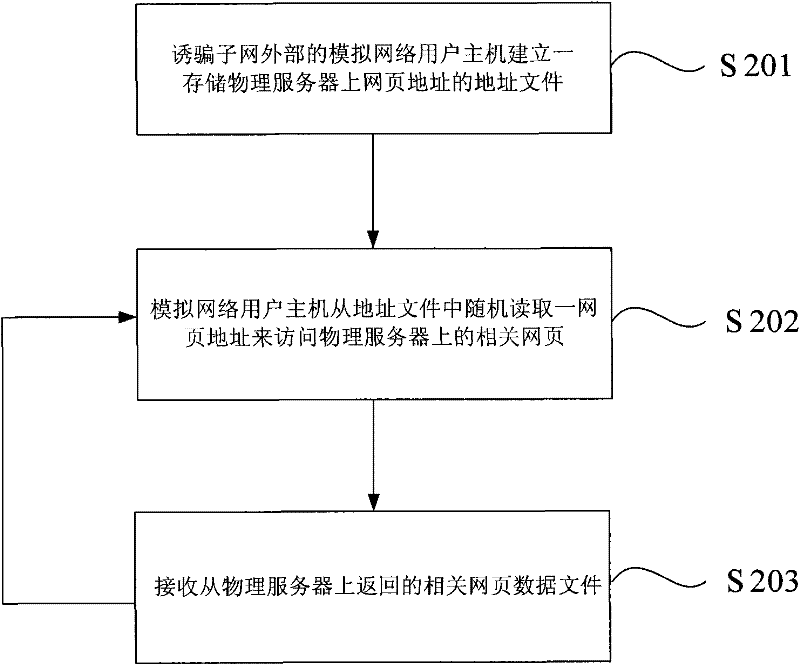
[0036] In this embodiment, we further introduce in detail the user behavior simulation in S102 in the first embodiment. First, we will introduce the behavior of simulating and deceiving network users outside the decoy subnet to access the physical server in the decoy subnet:
[0037] like figure 2 Shown is a schematic flow diagram of a simulated network user host accessing a physical server inside a decoy subnet provided by the implementation of the present invention. The access process includes the following steps:
[0038] S201: Deceiving the simulated network user host outside the subnet to create an address file storing the address of the web page on the physical server. Whether it is an FTP server, HTTP server, WEB server or mail server, to access it, you need to enter its webpage address, that is, the Uniform Resource Locator (Uniform Resource Locator, URL) address, so the establishment of this address file is for subsequent Access provides an access basis.
[0039]...
Embodiment 3
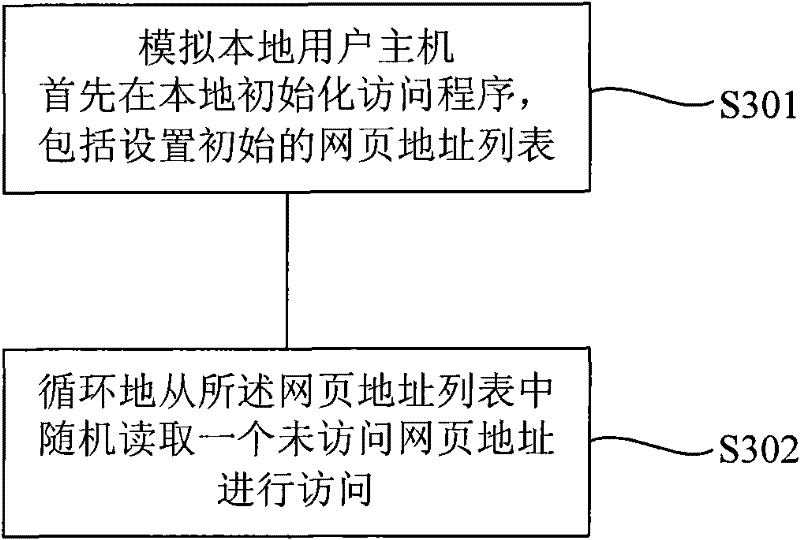
[0063] The third embodiment is to illustrate the modification and restoration of IP in the process of simulating network user hosts and simulating local user hosts in the second embodiment. like Figure 5 Shown is a schematic diagram of modifying and restoring IP interaction during a simulated network user host access process provided by Embodiment 3 of the present invention. The process includes the following steps:
[0064] S501: The simulated network user host sends a request data packet to the physical server in the decoy subnet to access the physical server.
[0065] S502: When the request data packet passes through the firewall, the firewall judges whether the request data packet is the request data packet sent by the simulated network user host: if not, directly let the request data packet enter the decoy subnet; if yes, enter the step S503. The judgment of the simulated user has been discussed in the second embodiment, and will not be repeated here.
[0066] S503-50...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com