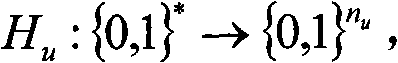Digital signature method based on identity
A digital signature and identity technology, applied in the direction of user identity/authority verification, etc., can solve problems affecting system operation efficiency, high calculation cost of verification equations, CDH difficult problem assumptions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The technical solution of the present invention will be further specifically described below in conjunction with the accompanying drawings.
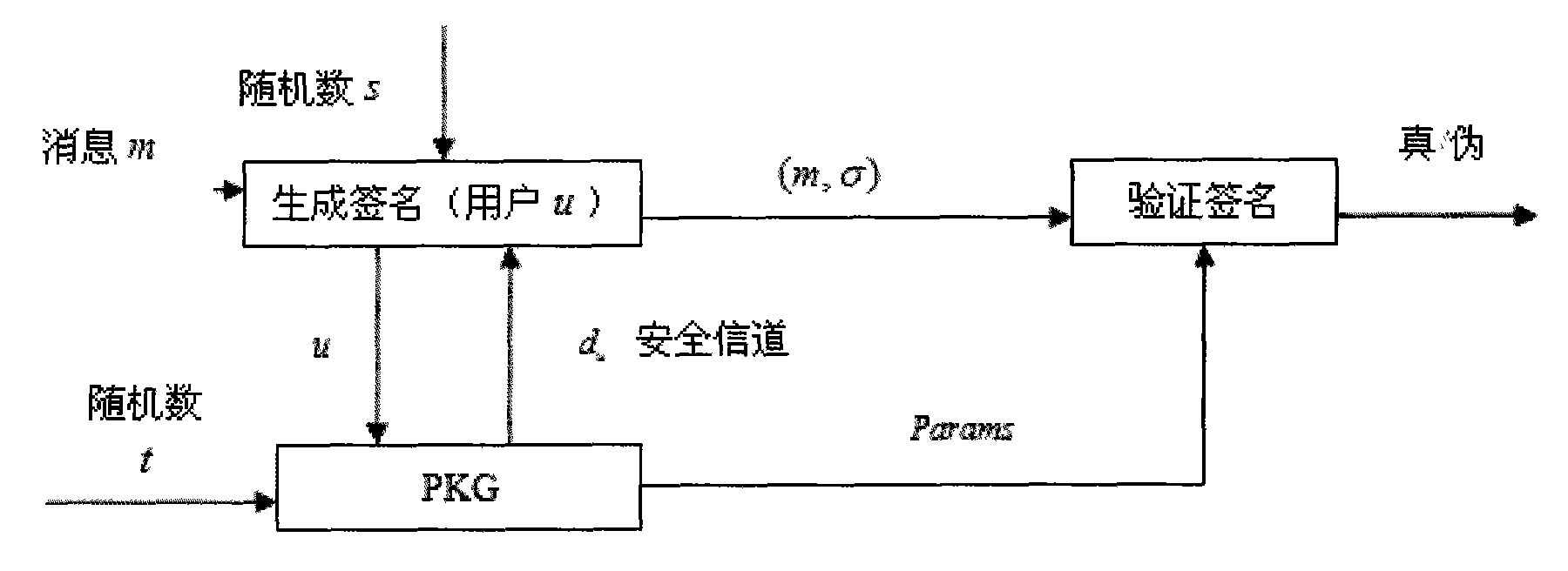
[0060] The present invention includes the steps of: generating system parameters for signing and verifying the signature; generating the user's private key according to the user's identity information and the system parameters; using the obtained private key (including the verification process of the private key) to The message is signed; the verifier verifies the signature of the message according to the system public parameters and the identity of the signer.
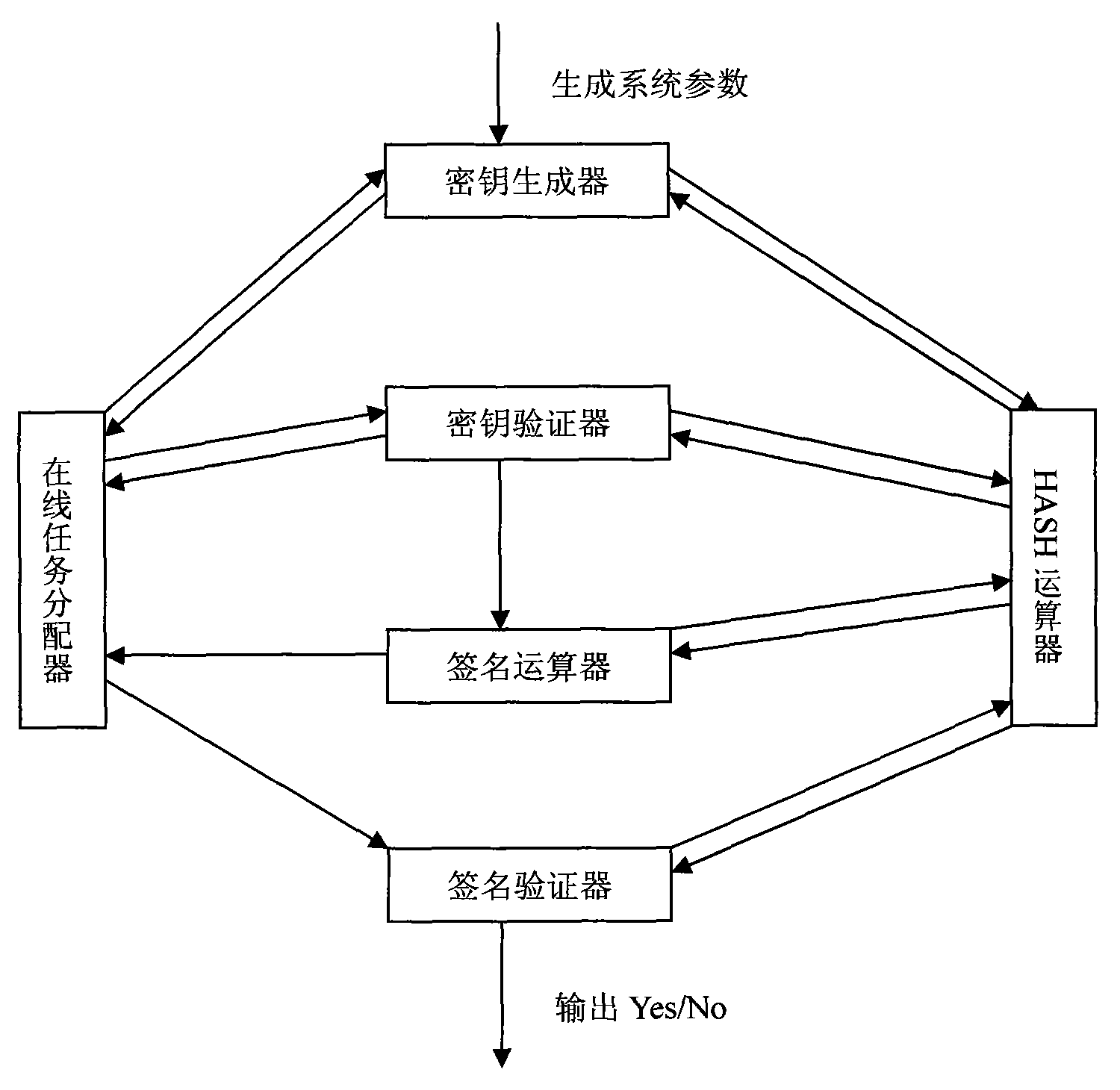
[0061] According to the system module flow chart, namely figure 2 , provide the concrete steps of the present invention through following each module to operate successively:
[0062] System parameter generation module (Setup):
[0063] PKG operation system parameter generation algorithm: first, the system selects a large prime number p, p factorial method cyclic group...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com