Method, system and detecting device for network security interaction
A network security and linkage system technology, applied in the field of network security linkage methods, systems and detection devices, can solve the problems of high false alarm rate, lack of interaction, and inability to achieve cross-network domain linkage, so as to reduce the false alarm rate and ensure effective sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
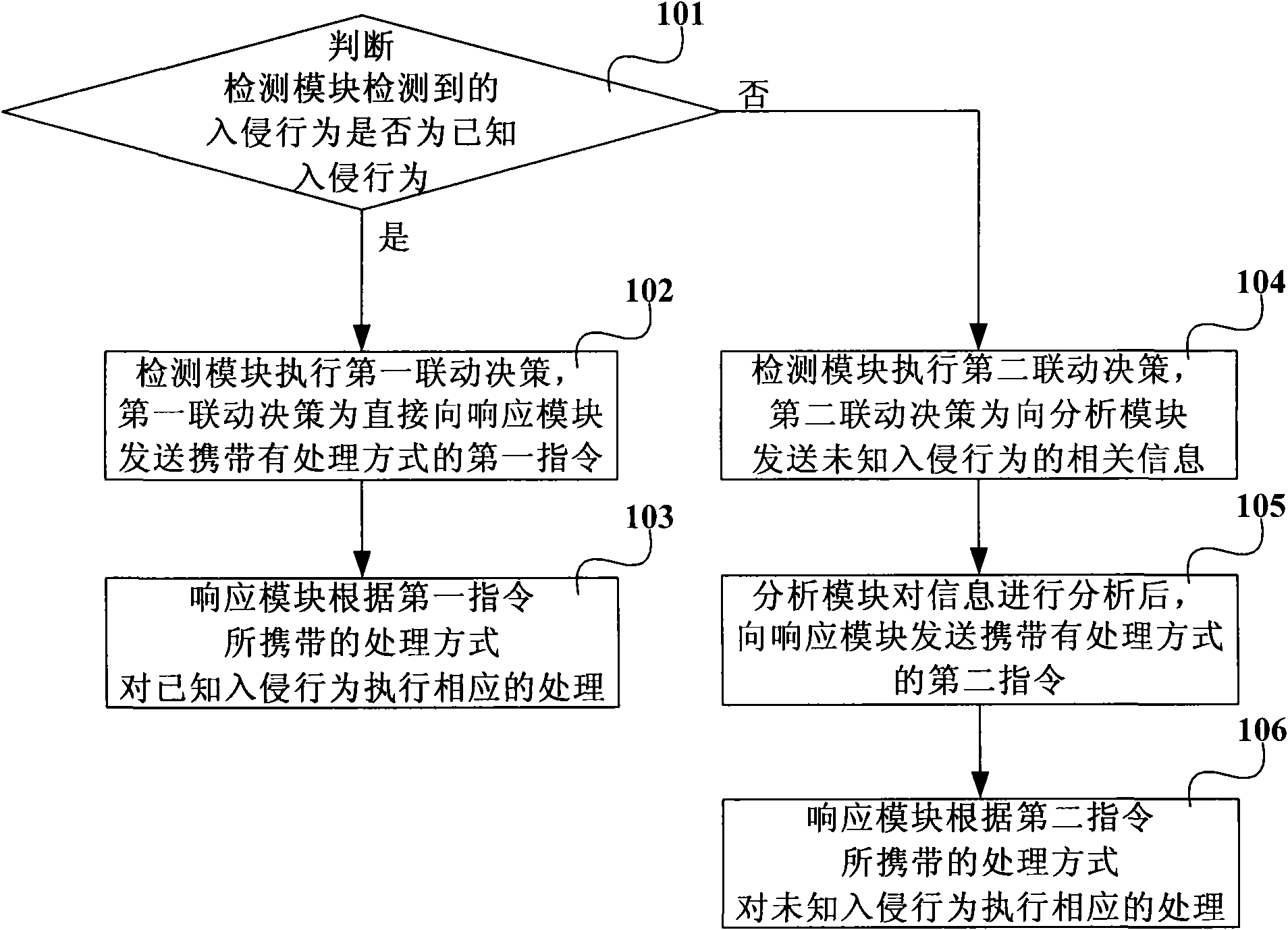
[0025] like figure 1 As shown, it is a schematic flowchart of the first embodiment of the network security linkage method of the present invention. This embodiment includes the following steps:
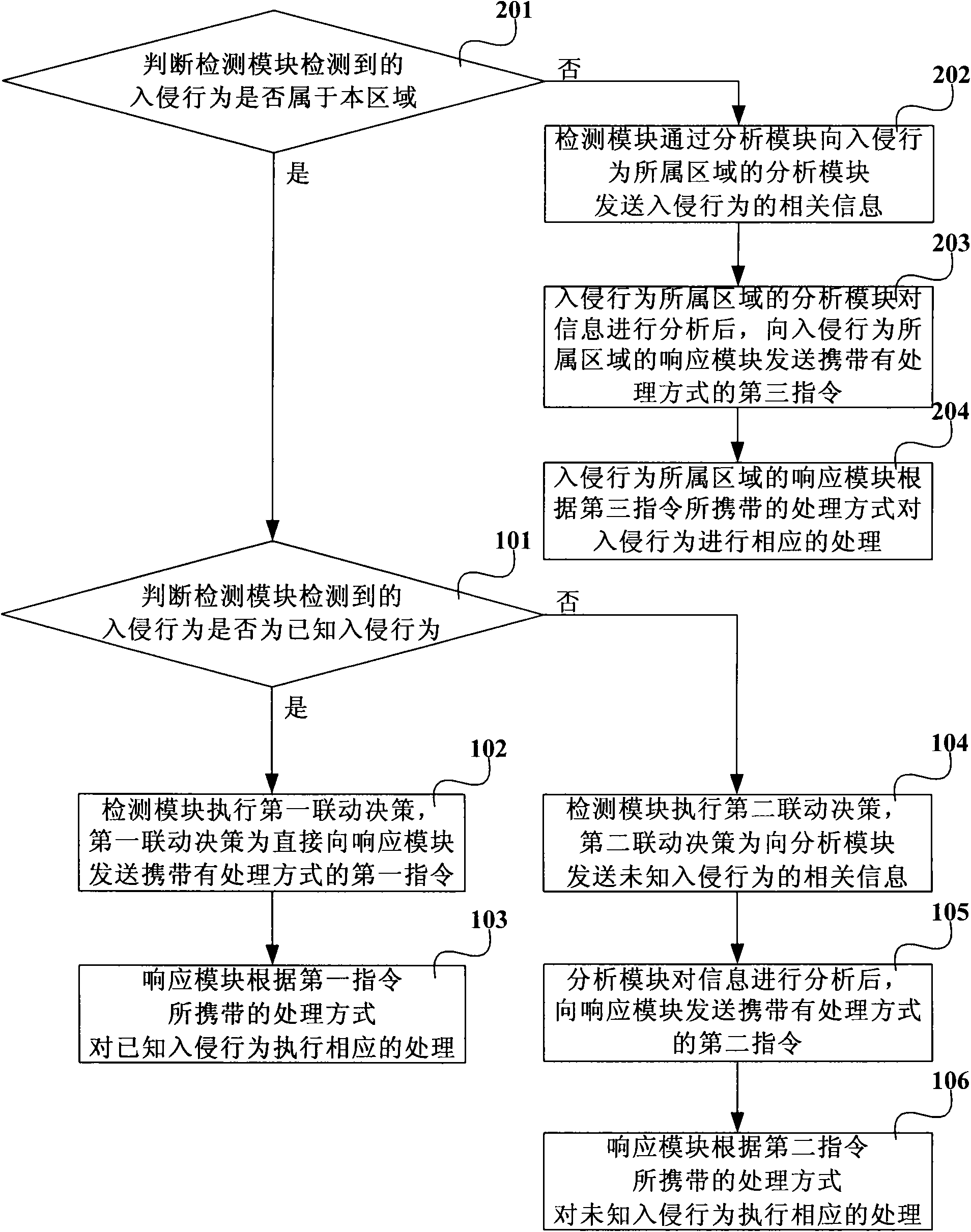
[0026] Step 101, after the detection module detects the intrusion behavior in the network, judge whether the intrusion behavior is a known intrusion behavior, if yes, then perform step 102 and step 103; otherwise, then perform step 104, step 105 and step 106 .
[0027] The known intrusion behavior is a known and definite security threat. In this step, the detection module can perform pattern matching according to the preset known attack pattern rule base to determine whether the intrusion behavior is a known intrusion behavior;
[0028] Step 102, the detection module executes the first linkage decision, the first linkage decision is that the detection module directly sends the first command carrying the processing method to the response module, so as to directly notify the response ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com