Vulnerability testing method in attack and system thereof
A vulnerability detection, the current state of the technology, applied in the field of network security, can solve the problems of executable program uncertainty, reduce the accuracy of analysis results, increase the difficulty of analysis, etc., to avoid failure to analyze, reduce memory usage, and good operability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
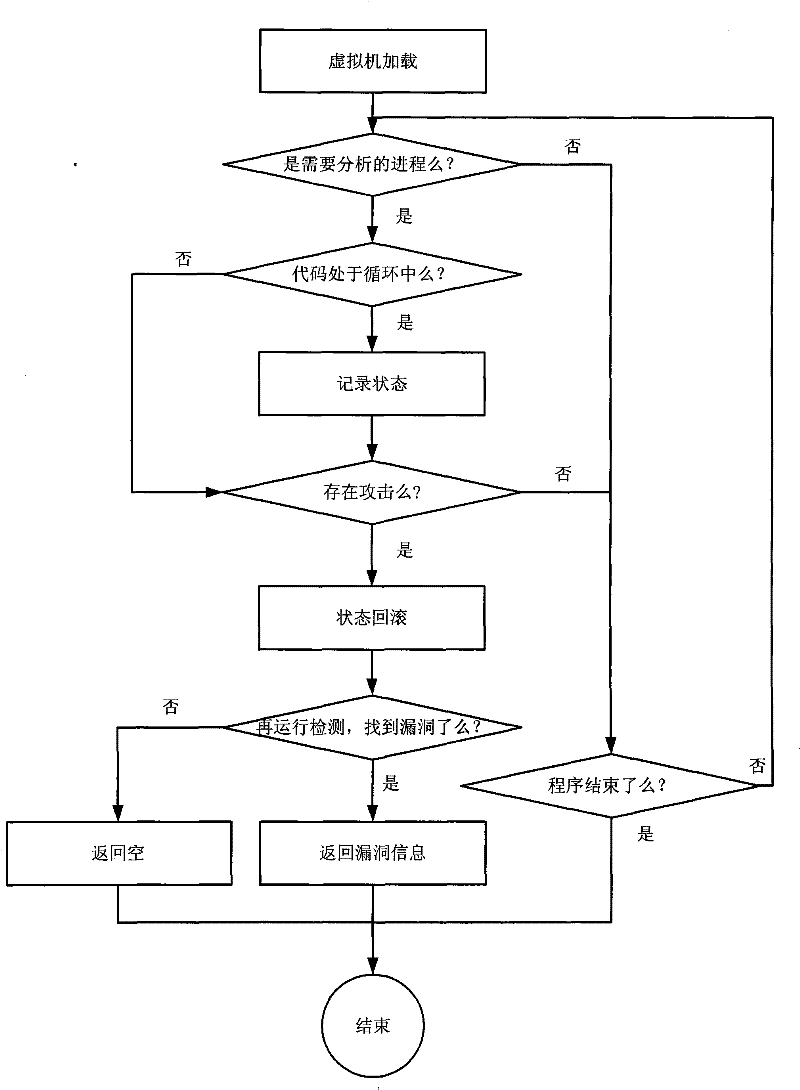
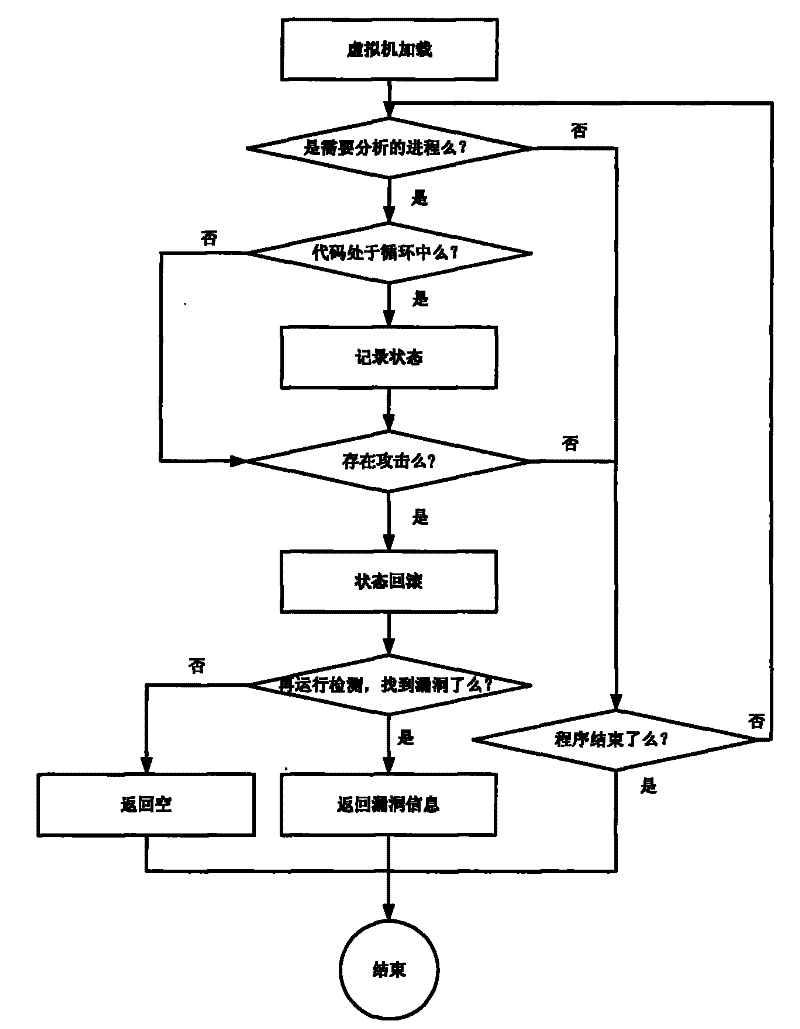
[0018] like figure 1 As shown in , it is the flowchart of vulnerability detection during attack in the most simplified mode. The specific implementation is as follows:
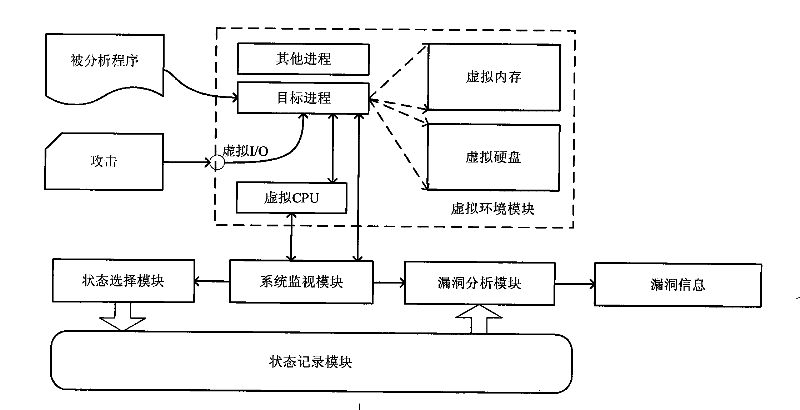
[0019] 1) Virtual machine loading: the analyzed program is loaded into the virtual environment module by the virtual loader and executed at the same time. The operating system installed in the virtual environment module as the operating platform of the analyzed program is called the guest operating system. The operating system chooses Windows or Linux according to the different programs to be analyzed. The specific code is as follows: run(target program);
[0020] 2) Process positioning: A program is a static description of the code, and a process is a dynamic description of the code, that is, the running program. Since the Windows operating system is installed in the guest operating system, it is a multi-tasking operating system, that is, multiple different programs may be executed on the virtual CPU with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com